API
The API Vulnerabilities dashboard provides a consolidated view of security vulnerabilities identified across scanned API endpoints. It enables teams to assess API-specific risks, prioritize critical exposures, and track remediation progress over time.
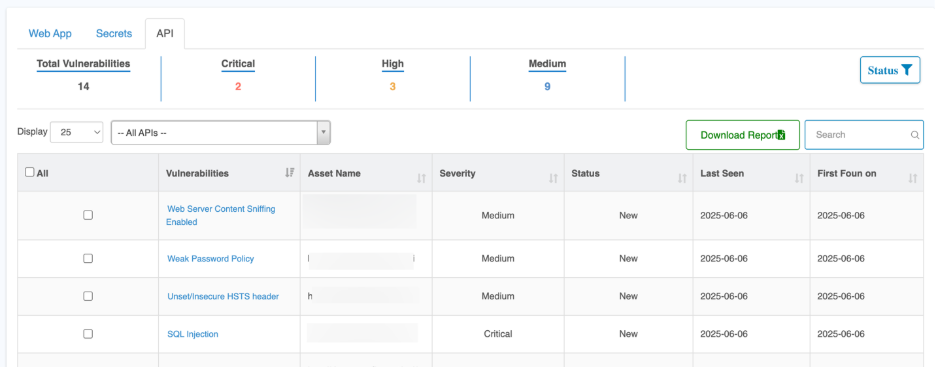 Vulnerability Summary Metrics
Vulnerability Summary Metrics
This section provides a real-time snapshot of API security posture by severity.

Metric | Description |
| Total Vulnerabilities | Total number of API security findings |
| Critical | Vulnerabilities with severe impact or direct exploitability |
| High | High-risk vulnerabilities with significant security impact |
| Medium | Moderate risk vulnerabilities |
| Status Filter | Filters by remediation state (New, Fixed, Re-open, etc.) |
Vulnerability Filters and Actions
This row allows focused analysis and reporting of API vulnerabilities.
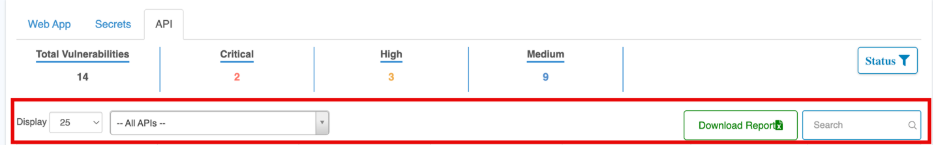
Control | Function |
| Results Display Count | Controls number of vulnerabilities shown per page |
| API Asset Selector | Filters vulnerabilities by specific API or endpoint |
| Download Report | Exports API vulnerability findings in csv file |
| Search | Keyword search across vulnerabilities and assets |
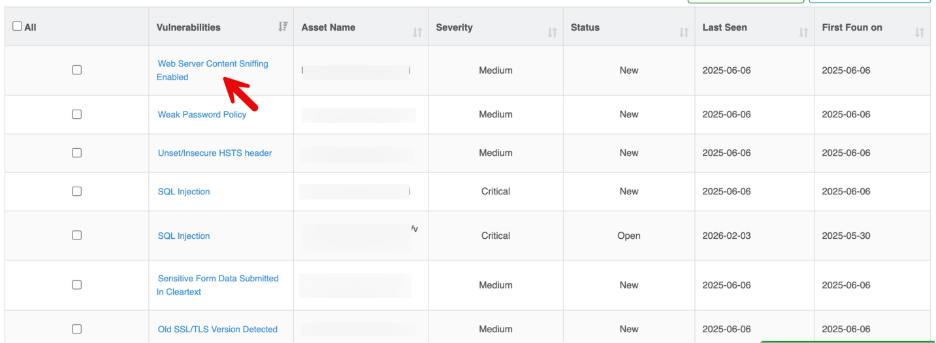
API Vulnerability Listing Table
Each row represents a security vulnerbaility detected in an API endpoint.
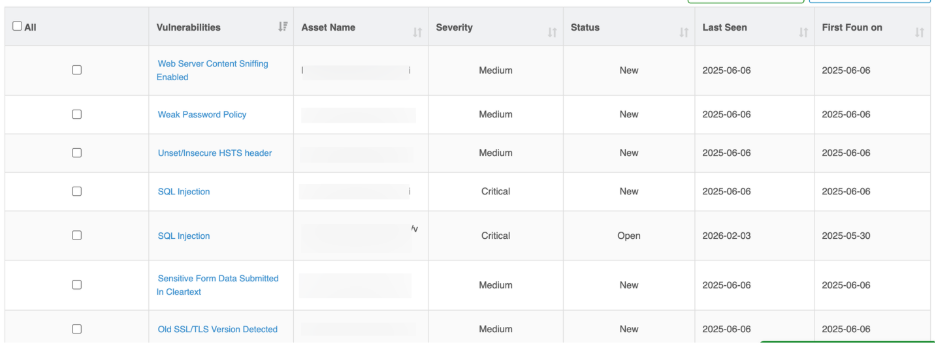
Column | Description |
| Vulnerability Name | Identified API security vulnerability (e.g., Authentication Bypass, Unsafe HTTP Methods) |
| Asset Name | Affected API endpoint or service |
| Severity | Risk level (Critical, High, Medium) |
| Status | Current remediation state |
| Last Seen | Most recent scan where vulnerability appeared |
| First Found On | Initial discovery date |
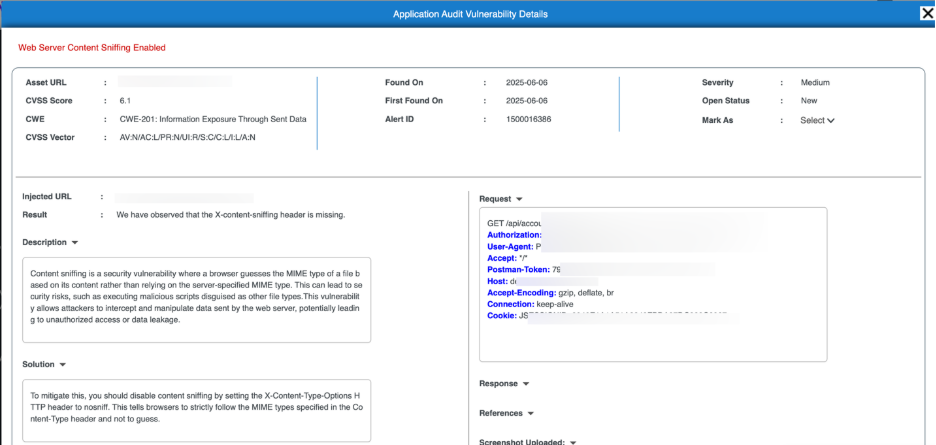
API Vulnerability Summary
The API Vulnerability Details page opens when you select an individual API vulnerability, providing in-depth technical evidence including request/response data, impact analysis, and remediation guidance.
It enables teams to validate exploit behavior, understand root cause, and apply precise fixes for API-specific security vulnerabilities.