CI/CD Integration
CI/CD Integration Using Jenkins
Integrating Continuous Integration and Continuous Deployment (CI/CD) with Jenkins enhances application security by detecting and fixing vulnerabilities early.
This integration automatically conducts security scans at each stage of the development pipeline, identifying potential threats before they reach production. Promptly addressing these vulnerabilities maintains a strong security posture and reduces the risk of exploitation.
How does Jenkins Integration Work?
The integration is carried out in 2 steps.
Install and configure the WAS Plugin in Jenkins
Begin by installing and configuring the WAS Plugin in Jenkins to enable seamless integration between your build environment and AppTrana.
Click here to access the installation and configuration guide for the WAS Plugin. The document also includes details on initiating a scan, checking the scan build status, and more.
Note: The reference document contains information and a sample report related to the Indusface WAS Plugin, which is also configured in AppTrana.
Configure Scan Build Pass/Fail Criteria in AppTrana
Set up the scan build criteria to ensure that your build process accurately reflects the defined vulnerability thresholds.
Generate Security Key
- Navigate to Settings > Integration > CI/CD.
- This section allows you generate a security key to integrate the site with Jenkins.
- Click Generate Key.
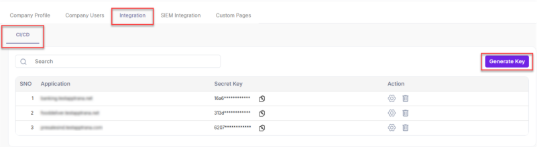
- Result: A pop-up window opens.
- Select the application and then click Save.
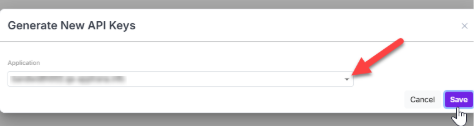
- Result: The system generates a security key for the application.
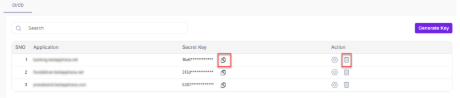
- The table displays the security keys of all the sites and allows you to configure the scan build criteria.
- Click the delete icon to remove the security key for a selected application.
Configure Scan Build Pass/Fail Criteria
- Users must set the pass/fail criteria for scan build. The Fail/Pass criteria are determined based on the threshold set by the customer for vulnerabilities found at different severity levels.
- Click the settings icon in the Action column.
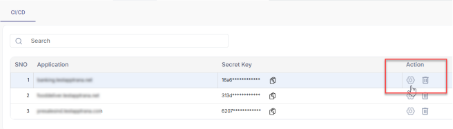
- Result: A pop-up window opens.
- Click the toggle switch to set threshold value and configure scan build Pass/Fail criteria.
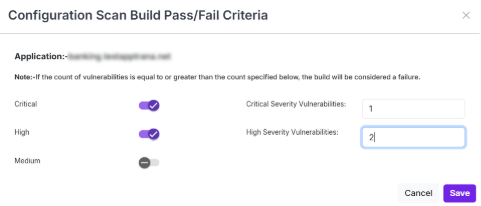
Example case
- A user sets the threshold at 1 critical and 2 high vulnerabilities.
- The build is considered Fail if it has 1 or more critical vulnerabilities and 2 or more high vulnerabilities.
- If either condition is not met, the build Fails.
| Critical | High | Criteria |
| 1 | 2 | Fail |
| 0 | 2 | Fail |
| 1 | 0 | Fail |
| 0 | 1 | Pass |
| 2 | 3 | Fail |
