AcuRisQ – Risk Management with Advanced Risk Scoring
Introduction
Indusface WAS implements a sophisticated risk-scoring system to evaluate the severity of vulnerabilities across the organization's assets.
This feature enables organizations to efficiently identify and address vulnerabilities in their infrastructure, prioritizing based on the level of risk they pose.
The following walkthrough video explains how AcuRisQ feature works:
Assessing Asset Risk
- Log in to the Indusface WAS portal. Navigate to the Summary section to view the overall risk score of the organization.
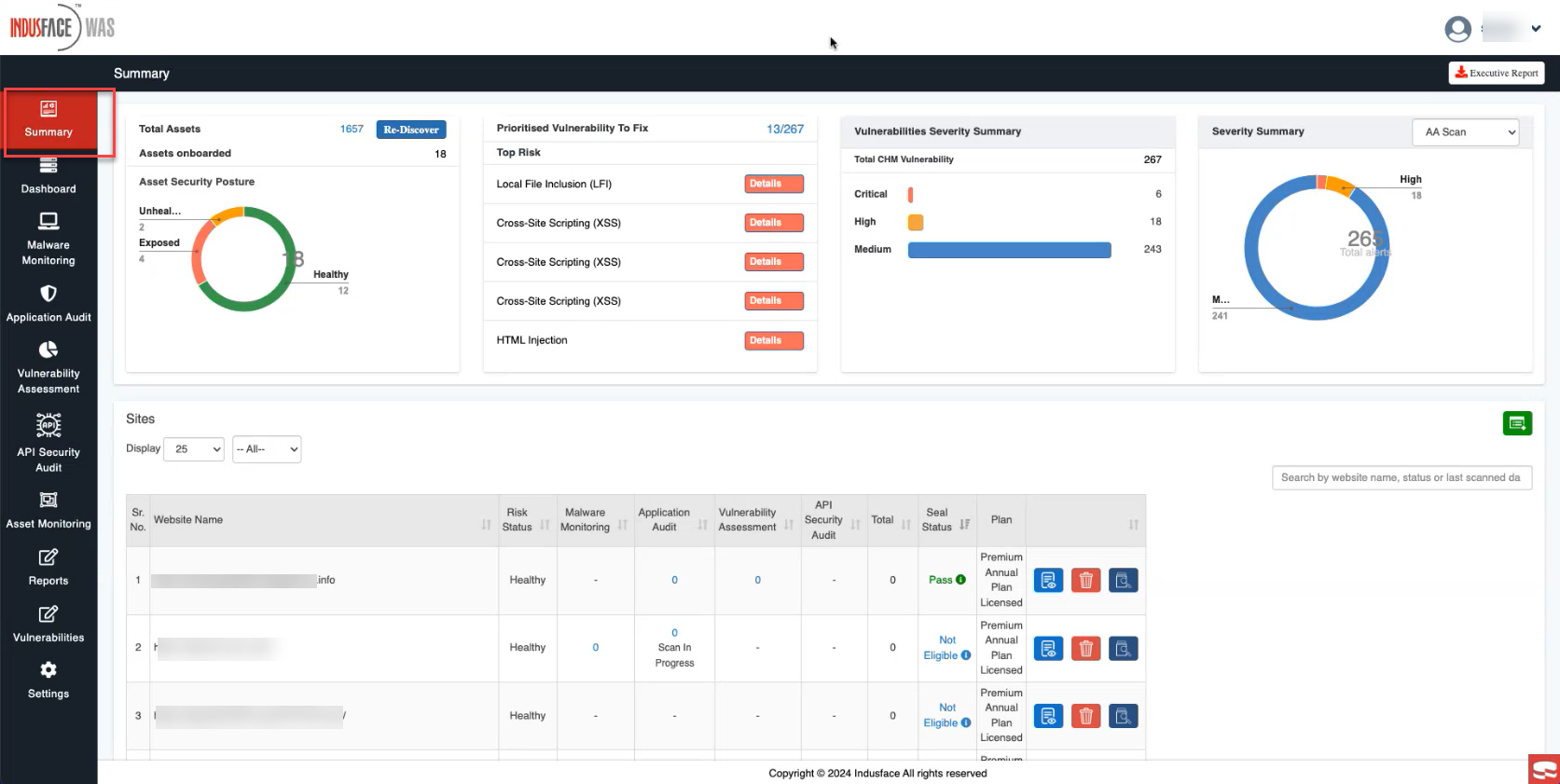
- Review the widget displaying the Total Assets onboarded and their security posture.
A detailed breakdown of the information displayed in the widget:
| Detail | Description | ||||||
| Total Assets | The total number of assets within the organization's inventory. | ||||||
| Assets onboarded | The number of assets successfully onboarded onto the Indusface WAS platform for security monitoring and assessment. | ||||||
| Asset Security Posture | Provides an overview of the security posture of the assets, categorized into different states:
| ||||||
| Re-Discover | Initiates re-discovery of assets when security status changes or updates since initial assessment. |
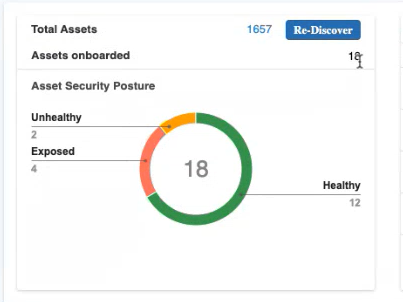
- Check the Vulnerabilities marked as High Risk.
Vulnerabilities are classified into High Risk, Need Attention, and Others based on Risk Score. How Risck scores are calculated is explained later in the document.
| Detail | Description |
| High Risk | Vulnerabilities with a Risk Score equal to or greater than 36 are classified as High Risk. These are vulnerabilities that need to be acted upon immediately by the organization |
| Need Attention | Vulnerabilities with a Risk Score equal to or greater than 26 are classified as Need Attention. These are vulnerabilities that are important and need prompt action. Ideally, it should be fixed within 30 days |
| Others | These are vulnerabilities with a Risk score less than 26. Though it is not classified as important vulnerabilities, it is recommended that all vulnerabilities are prioritized and fixed based on business needs. |
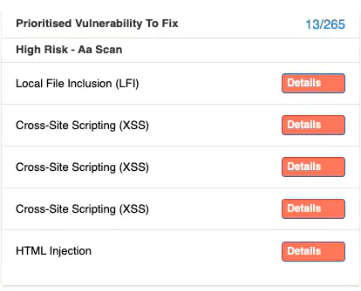
- The Vulnerability Severity Summary provides an overview of the severity levels of vulnerabilities affecting the organization's assets. The severity is calculated based on CVSS score of the vulnerability.
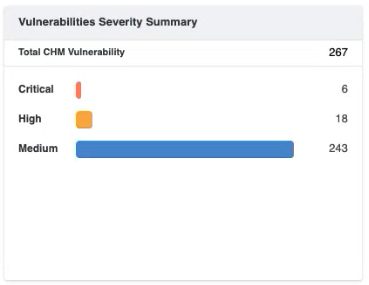
| Details | Description | ||||||
| Total CHM Vulnerabilities | Total number of Critical, High, and Medium Vulnerabilities.
|
- Access the Severity Summary of vulnerabilities Identified in different scans -Application Audit (AA) scan, Malware Monitoring (MM) scan, and Vulnerability Assessment (VA) scan.
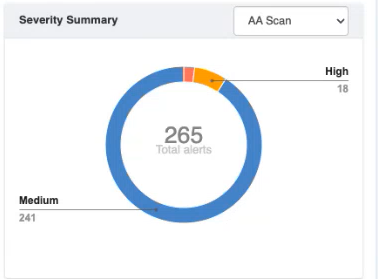
The chart includes the following details
| Details | Description |
| Total alerts | The total number of alerts identified |
| Critical | Indicates the number of vulnerabilities identified as Critical |
| High | Indicates the number of vulnerabilities identified as High |
| Medium | Indicates the number of vulnerabilities identified as Medium |
Delete Table - Column + Column + Row - Row |
|---|
Review the risk status of each asset in the table and utilize sorting functionality if needed.
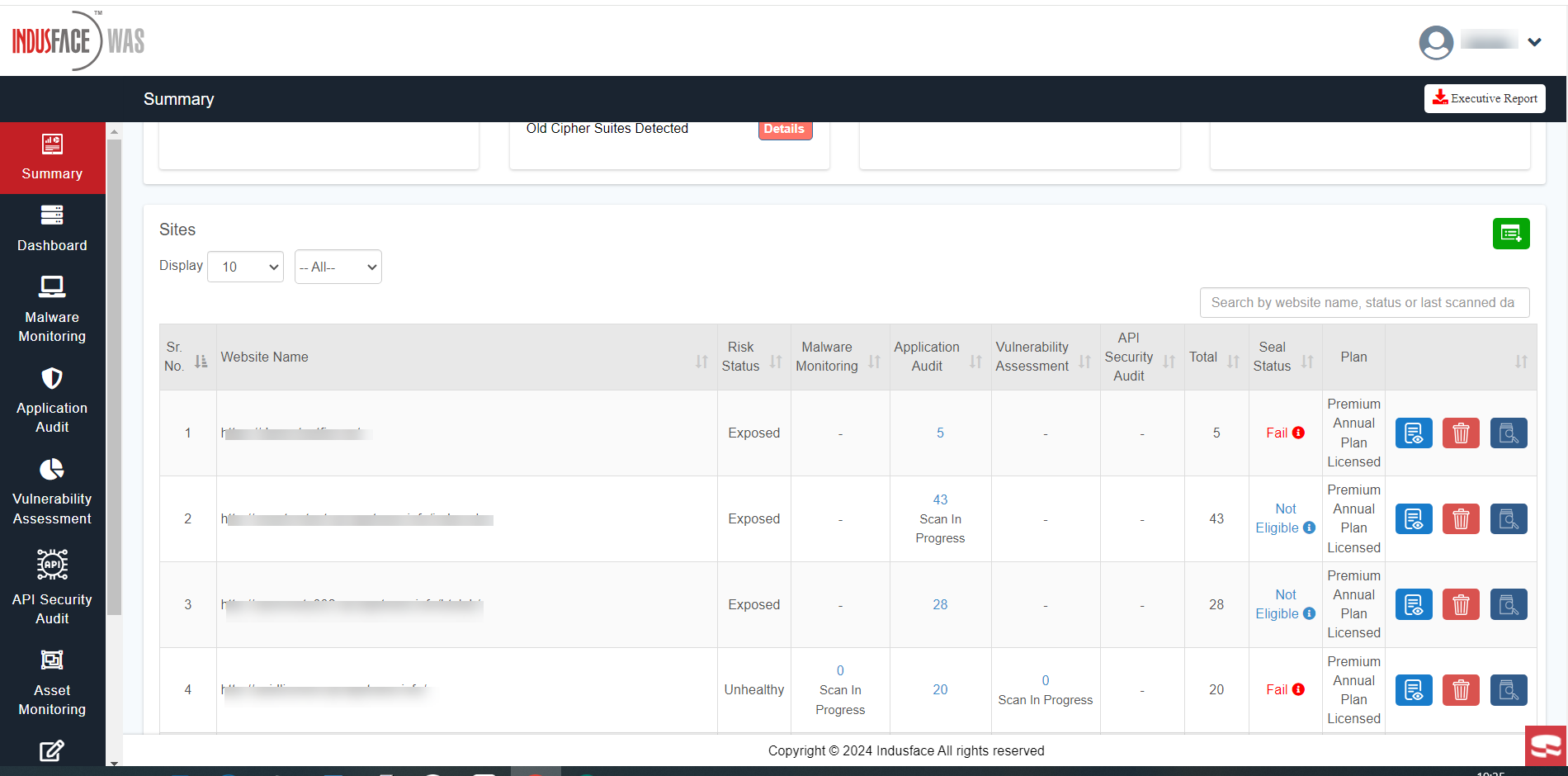
| Details | Description |
| Sr.No | Serial Number |
| Website Name | Name of the website or asset |
| Risk Status | Indicates the severity level of risk associated with the asset, categorized as exposed, unhealthy or healthy |
| Malware Monitoring | Outcome of malware monitoring scan on the asset |
| Application Audit | Outcome of the application audit scan on the asset |
| Vulnerability Assessment | Outcome of the vulnerability assessment scan on the asset |
| API Security Audit | Outcome of the API security audit scan on the asset |
| Total | The total count of vulnerabilities detected in the asset across all scans |
| Seal Status | Status of the security seal associated with the asset, indicating compliance or security status. |
| Plan | Type of Indusface WAS plan |
| View Details | Option to view detailed information about the vulnerabilities identified in the particular asset. |
| Delete | Option to remove the asset from the system. |
| Scan | Initiate a security scan for the asset to identify any new vulnerabilities or changes in security status. |
- Select the desired number of assets to be displayed on the screen using the "Display" filter.
- Use the Search option to find specific assets by name, status, or last scanned date.
Understanding Identified Vulnerabilities and Their Risk
Users have two options to access vulnerability details:
Clicking the numerical value within the Prioritized Vulnerabilities To Fix in the summary section will take the user to the vulnerabilities menu with the Risk-based prioritized list of vulnerabilities.
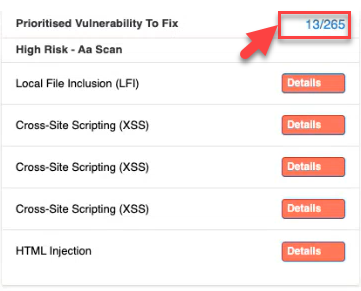
Navigate to "Indusface WAS" -> "Vulnerability" within the platform.
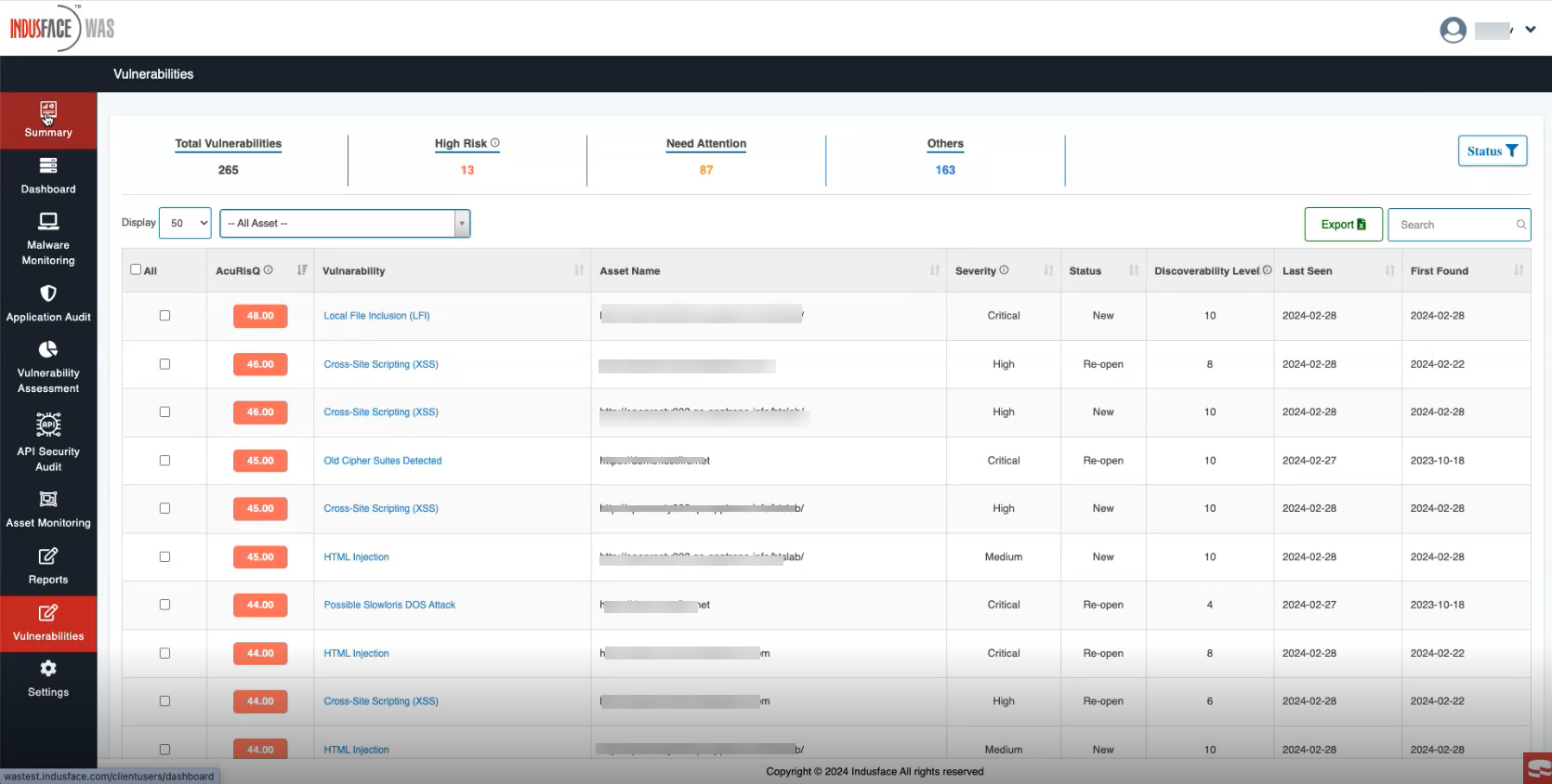
- Upon accessing the Vulnerability menu section, users are presented with an overview screen.
- This screen provides a summary of the Total Vulnerabilities detected within the system, as per the last scan.
- It also highlights the distribution of vulnerabilities based on their severity levels, such as High-Risk, Need Attention, and Others.
- The table on this screen covers the following details for each vulnerability:
| Details | Description |
| AcuRisQ | Indicates the risk score assigned to the vulnerability by the AcuRisQ |
| Vulnerability | Describes the type or nature of the vulnerability detected. |
| Asset Name | Specifies the name or identifier of the asset where the vulnerability was discovered. |
| Severity | Categorizes the severity level of the vulnerability as critical, high, or medium, providing insights into its potential impact on security. This is determined through CVSS score |
| Status | Status of the vulnerability - New, Open, Re-Open, Closed |
| Discoverability Level | Indicates the ease or difficulty of discovering the asset, the higher the value the easier it is to find. |
| Last Scan | Displays the date of the most recent scan where the vulnerability was identified. |
| First Found | Indicates the date when the vulnerability was first detected within the system. |
- Select the desired number of assets to be displayed on the screen using the "Display" filter.
- Choose assets by URL or apply filters based on severity level, asset type, or other criteria to refine the displayed vulnerability data.
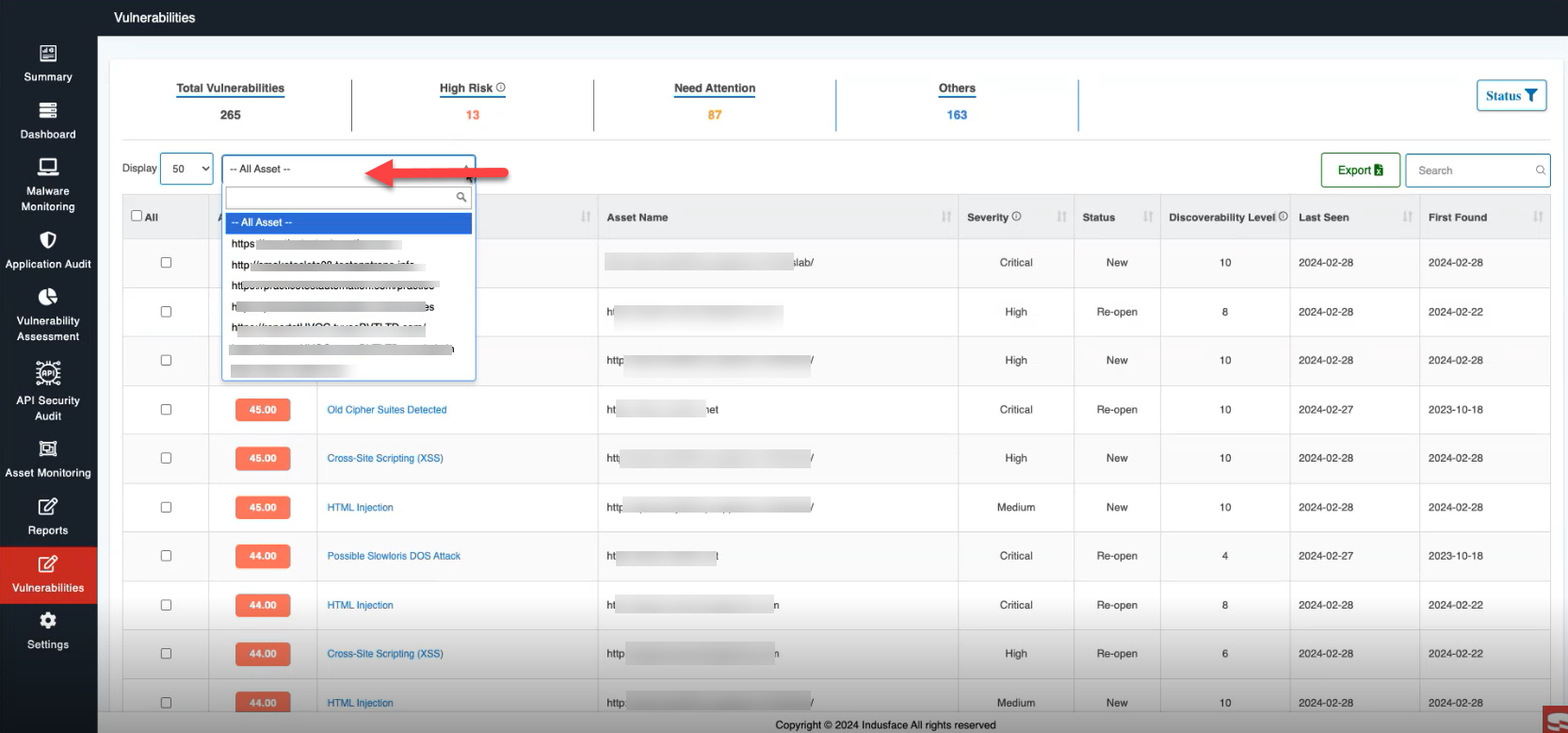
- Utilize Status to narrow down assets based on their status – All, New, Open, Re-Open and Closed
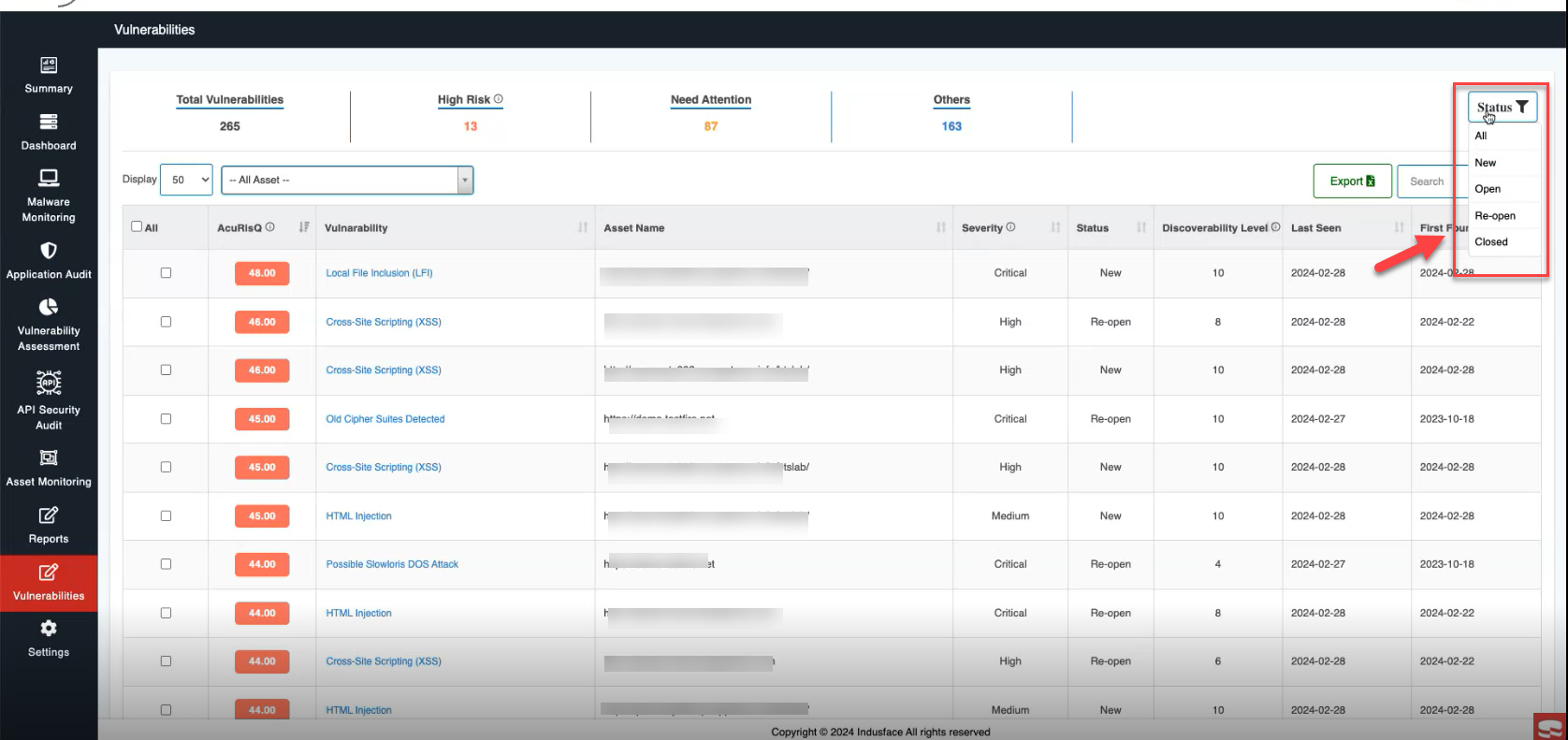
- The Filter option allows you to select assets and apply filters according to your requirements. You can then export the report by clicking the Export button, and downloading it in CSV format.
- Below is a sample report screenshot for reference.
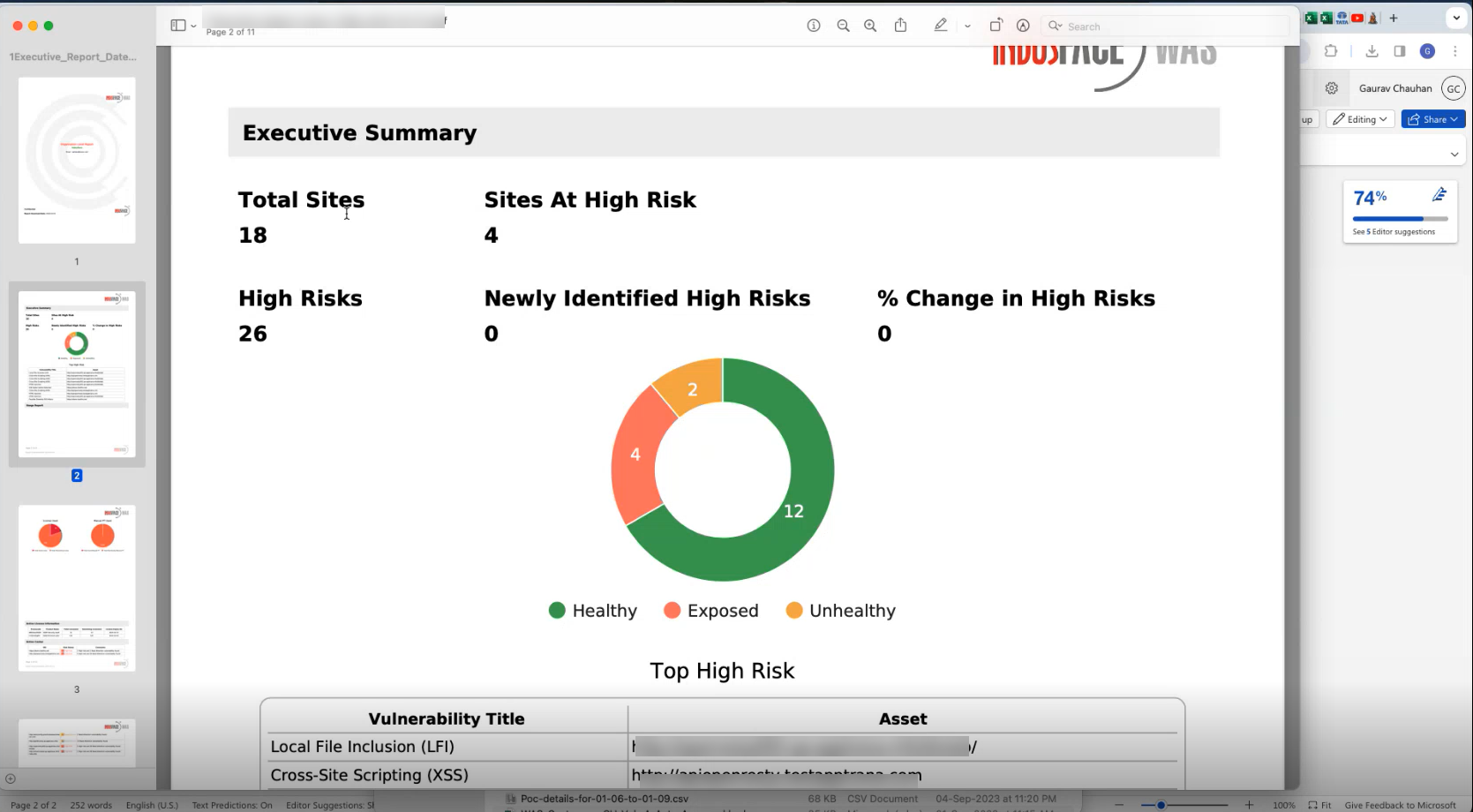
- Users can Mark (Mark as) selected assets as Whitelist or PoC Required.
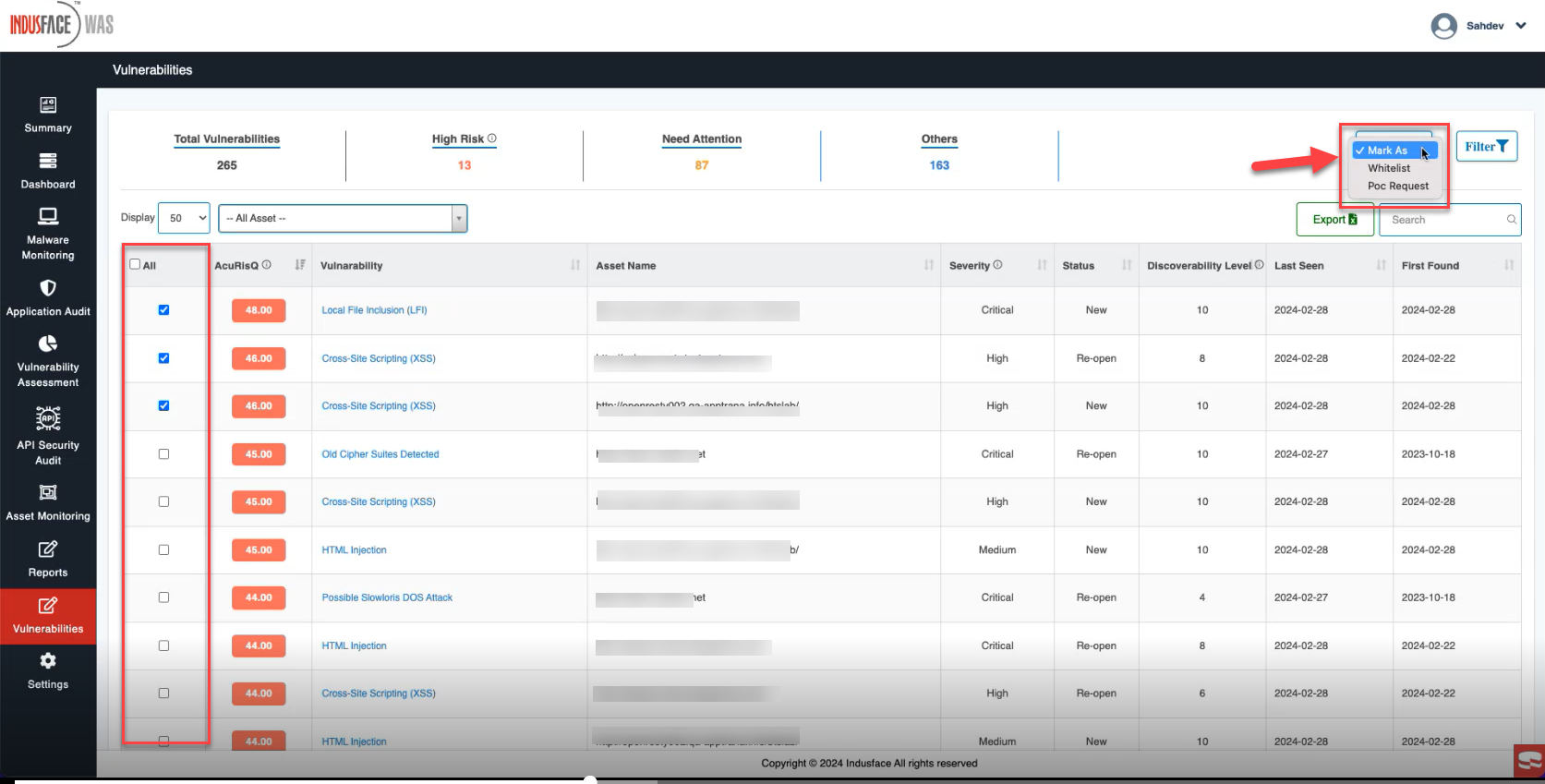
| Whitelist | To exclude the assets from certain security scans or actions
|
| PoC Required | To designate selected assets as requiring Proof of Concept (PoC) before taking any remediation actions. |
- Utilize the Search bar to search for specific assets or URLs within the system, streamlining navigation to the desired information.
Transparent Risk Score in AcuRisQ
Users can view the vulnerability details by clicking on the respective vulnerability, which reveals comprehensive information about the vulnerability and its score.
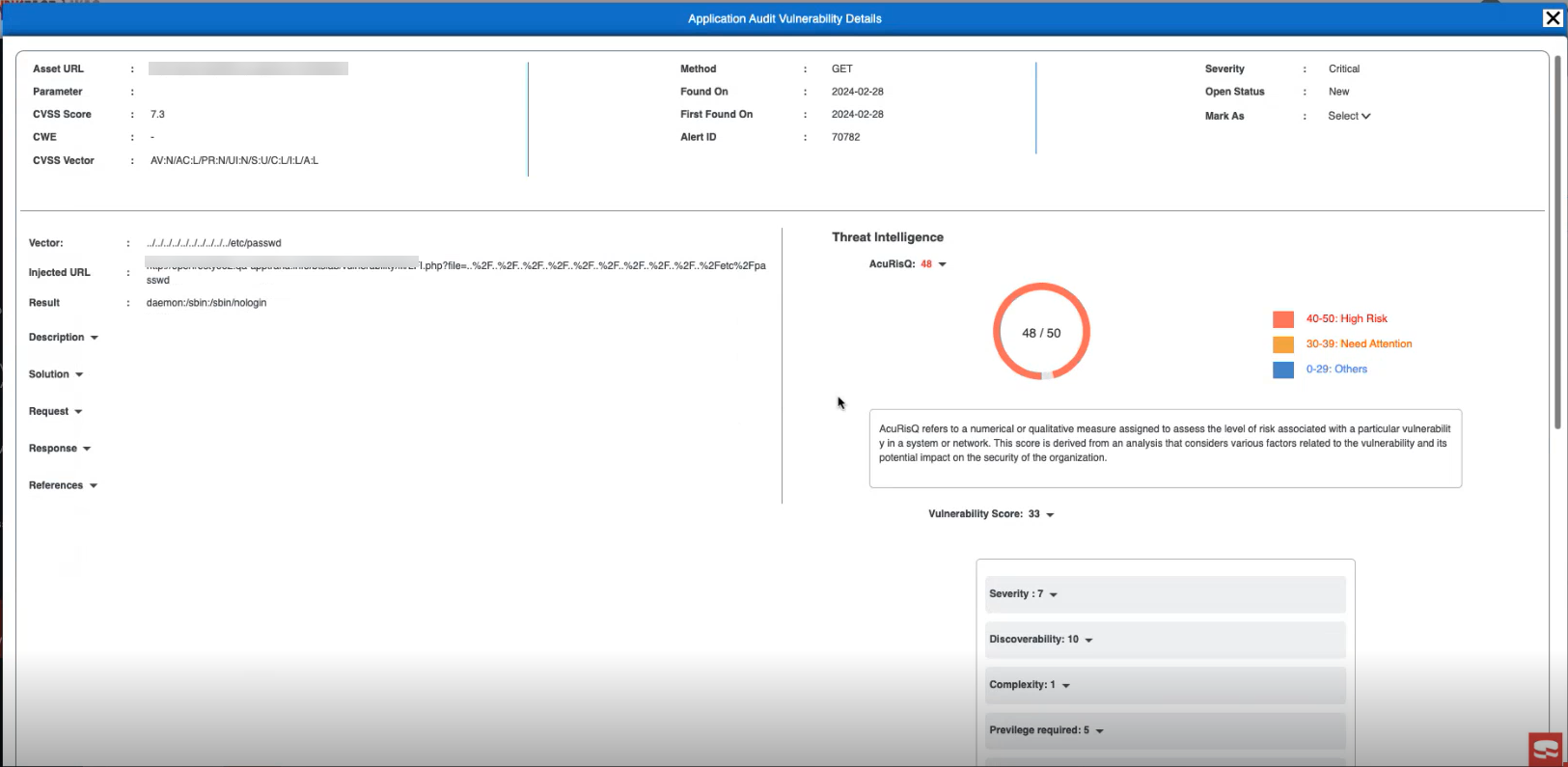
The details include:
1. Insightful Overview: The Top Portion
| Details | Description |
| Asset URL | URL of the asset where the vulnerability was detected. |
| CVSS Score | Common Vulnerability Scoring System (CVSS) score, indicating the severity of the vulnerability |
| CWE | Common Weakness Enumeration (CWE) ID associated with the vulnerability |
| CVSS Vector | Vector representation of the CVSS score |
| Method | Method through which the vulnerability was detected |
| Found On | Location where the vulnerability was found |
| First Found On | Date when the vulnerability was first discovered |
| Alert ID | Unique identifier for the vulnerability alert |
| Severity | Severity level of the vulnerability |
| Open Status | Status indicating whether the vulnerability is open or resolved |
| Mark As | Option to mark the vulnerability as whitelist or request Proof of Concept (PoC) |
Detailed Analysis: The Left Side
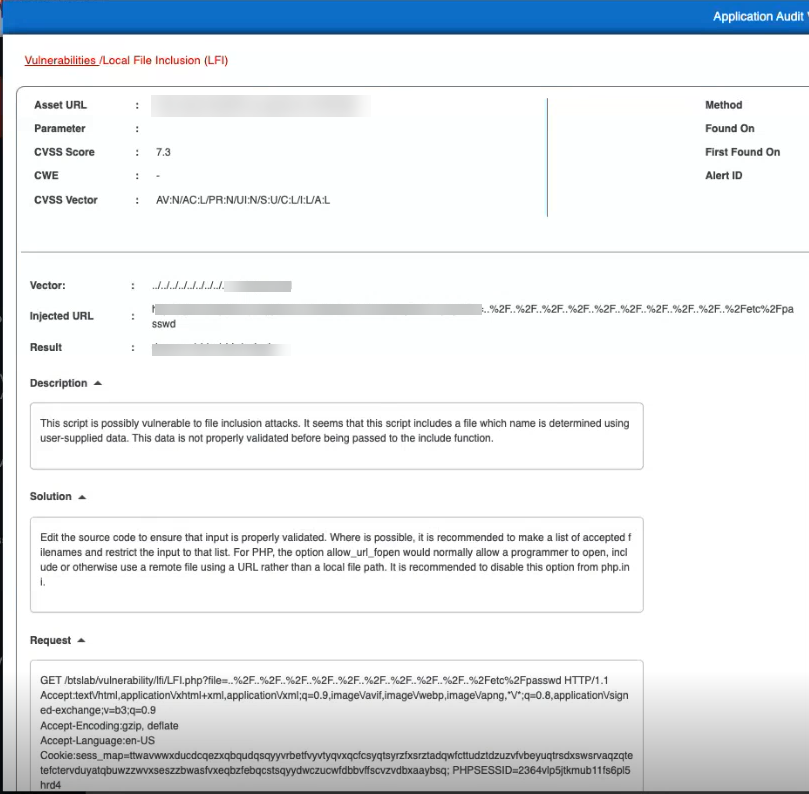
| Details | Description |
| Injected URL | URL where the injection occurred. |
| Result | Result of the vulnerability injection |
| Description | Detailed description of the vulnerability |
| Solution | Recommended solution or mitigation steps |
| Request | Details of the HTTP request associated with the vulnerability |
| Response | Details of the HTTP response associated with the vulnerability |
| References | References or additional resources related to the vulnerability |
Threat Intelligence: The Right Side
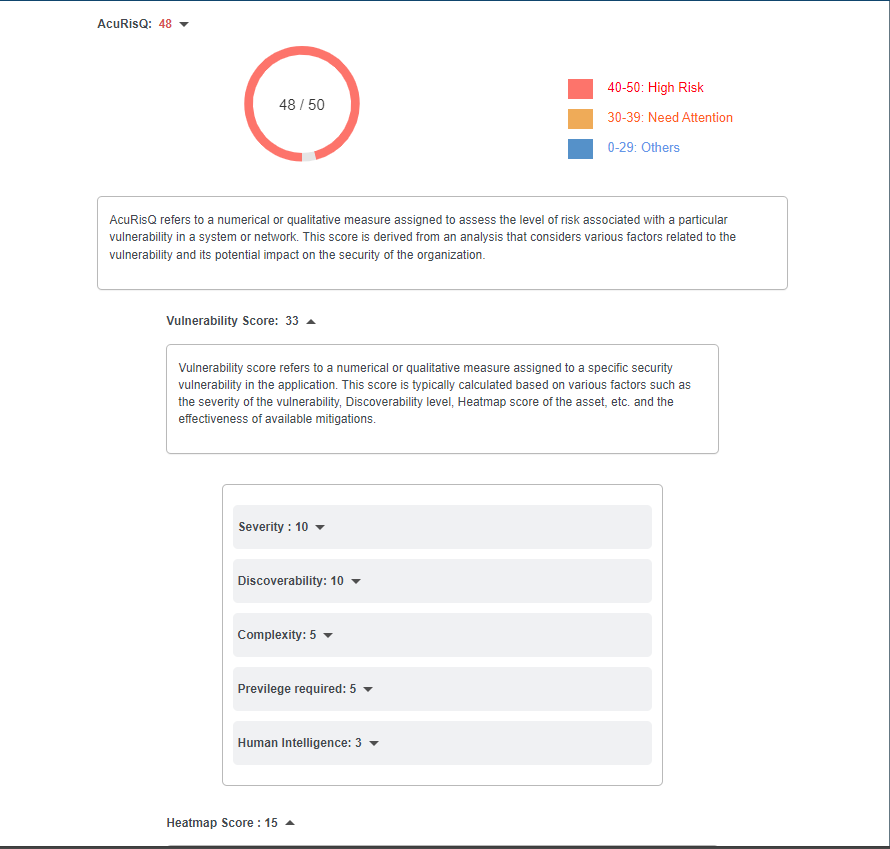
AcuRisQ Legend: AcuRisQ helps you prioritize vulnerabilities by assigning a risk level.
Here's how it is classified:
0-25: Others: These vulnerabilities are considered lower risk.
26-35: Needs Attention: These vulnerabilities deserve investigation and may require mitigation strategies.
36-50: High Risk: These vulnerabilities pose a significant threat and should be addressed promptly.
Indusface WAS AcuRisQ uses factors like Vulnerability Score and Heatmap Score to accurately calculate the risk level of vulnerabilities.
| Details | Description |
| AcuRisQ | AcuRisQ prioritizes vulnerabilities based on calculative risk, allowing businesses to focus their efforts on the most critical issues across their entire account. Risk score assigned to the vulnerability by AcuRisQ, categorize the vulnerabilities as High Risk(36-50), Need Attention(26-35), or Others (0-25) based on predefined criteria. |
| Vulnerability Score | A numerical or qualitative measure of the vulnerability, calculated based on severity, discoverability, complexity, privilege required, and human intelligence. The range lies between 0-35. |
| Severity | This is determined based on severity of vulnerability which is determined by CVSS score so the Critical vulnerability gets a severity score of 10, High 7, and Medium 5. The score range lies between 0-10. |
| Discoverability | This is determined based on where the vulnerability is found. If it is found on the home page then it is easier to find and provided a higher score than vulnerability found 3 steps down or in the inner pages. The score range lies in between 0-10. |
| Complexity | Complexity Score refers to an assessment of the difficulty or intricacy associated with exploiting a particular vulnerability. Moderate score meaning an attacker with some skills could exploit it. The score range lies in between 0-5. |
| Privilege required | This score indicates the level of access needed to exploit that vulnerability. The score range lies in between 0-5. |
| Human Intelligence | Human intelligence pertains to the supplementary factor that our expert team contributes as value to the comprehensive vulnerability score. The score range lies in between 0-5. |
| Heatmap Score | The Heatmap score involves assessing linked assets, considering the criticality of these linked assets, and applying assigned weight factors to calculate the overall heatmap score. This calculation includes the normalization of all relevant factors to ensure a standardized evaluation. The score range lies in between 0-15. |
Example: AcuRisQ in Action
Imagine a vulnerability called "Session Cookie Manipulation" found on an asset (e.g., www.abc.com). While the severity score is medium (5), AcuRisQ assigns a higher overall risk ("High Risk") due to other factors.
AcuRisQ evaluates vulnerabilities beyond just their severity. Here's how it breaks down:
Discoverability Score (10): This measures how easily an attacker can find the vulnerability. A higher score(10) means it's more accessible and therefore riskier.
Complexity Score (5): This assesses how hard it is to exploit the vulnerability. A moderate score (5) suggests it requires some skill to exploit.
Privilege Required (5): This indicates the level of access needed, like whether authentication is required. A score of 5 means the attacker might need some access but not necessarily administrative privileges.
Human Intelligence Score (0): This reflects the additional insights security experts can provide for specific vulnerabilities. In this example, the score is 0, but it could be higher for more concerning vulnerabilities.
Putting it all together:
Total Vulnerability Score: 25 (5 + 10 + 5 + 5 + 0)
Heatmap Score: 15 (This score likely reflects the criticality of the asset - a high score indicates it's vital for your business security, this is determined by our algorithm based on asset linkage to other assets in the organization)
The Result (40): AcuRisQ classifies this vulnerability as "High Risk" based on these combined scores. Even though the severity might be medium, factors like discoverability and exploitability elevate the overall risk.
