External Attack Surface Management (EASM)
This section is dedicated to manage and monitor your external assets' security posture.
Overview
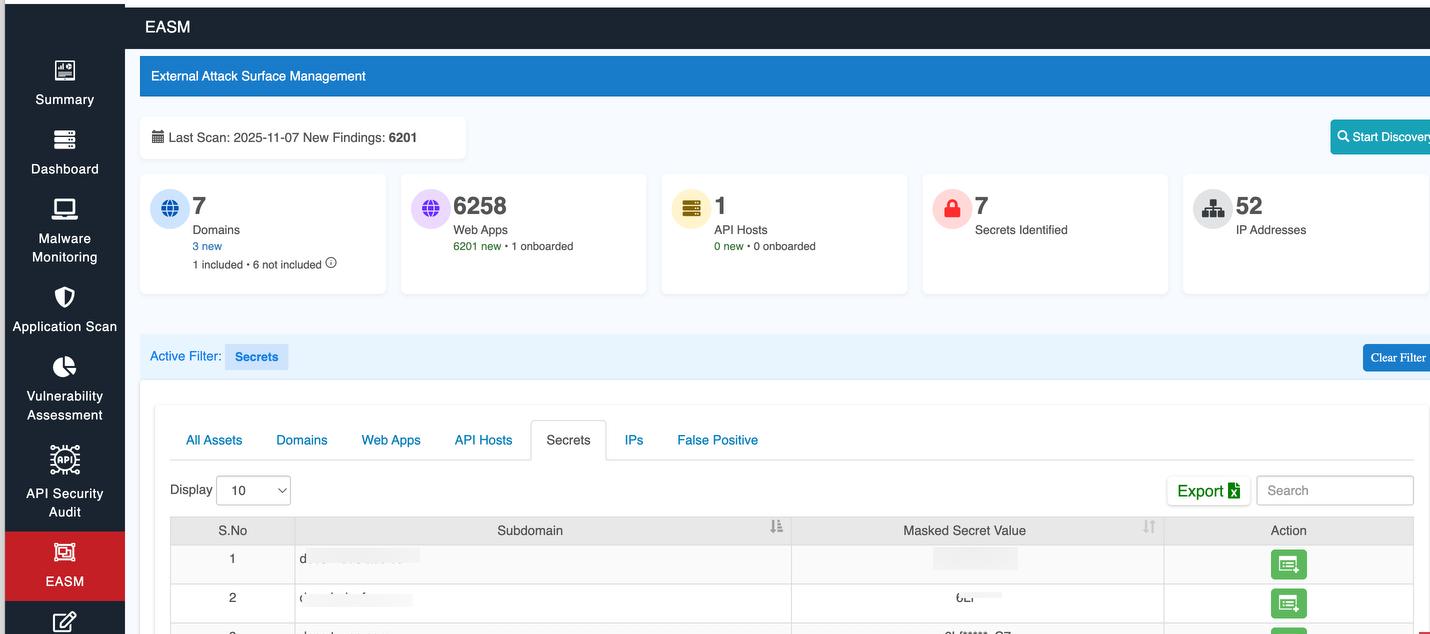
- Last Scan - The date when the most recent scan was performed to detect vulnerabilities, misconfigurations, and threats.
- New Findings: - The number of new security findings from the latest scan.
Start Discovery
Click Start Discovery to initiate the discovery process.
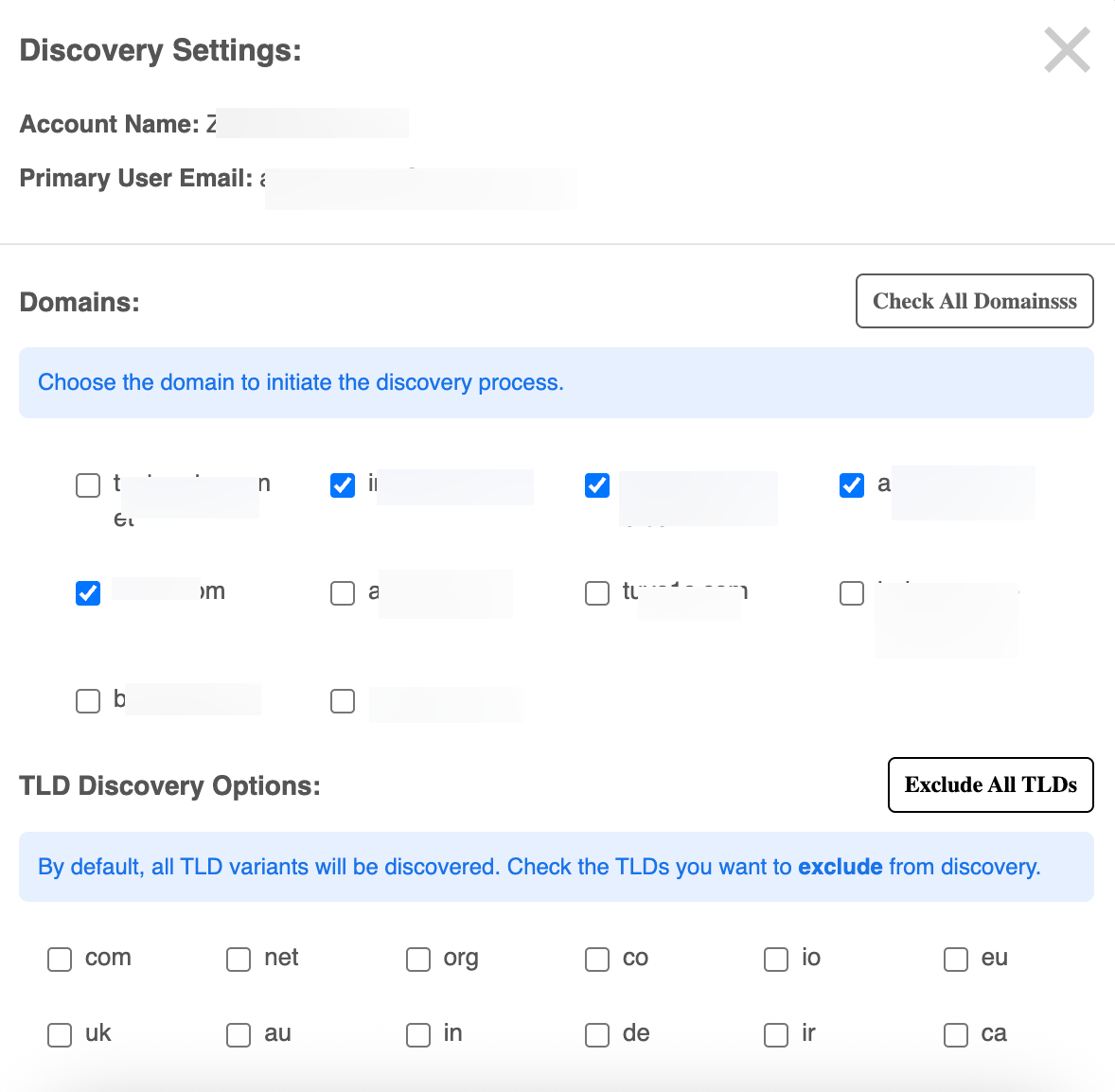
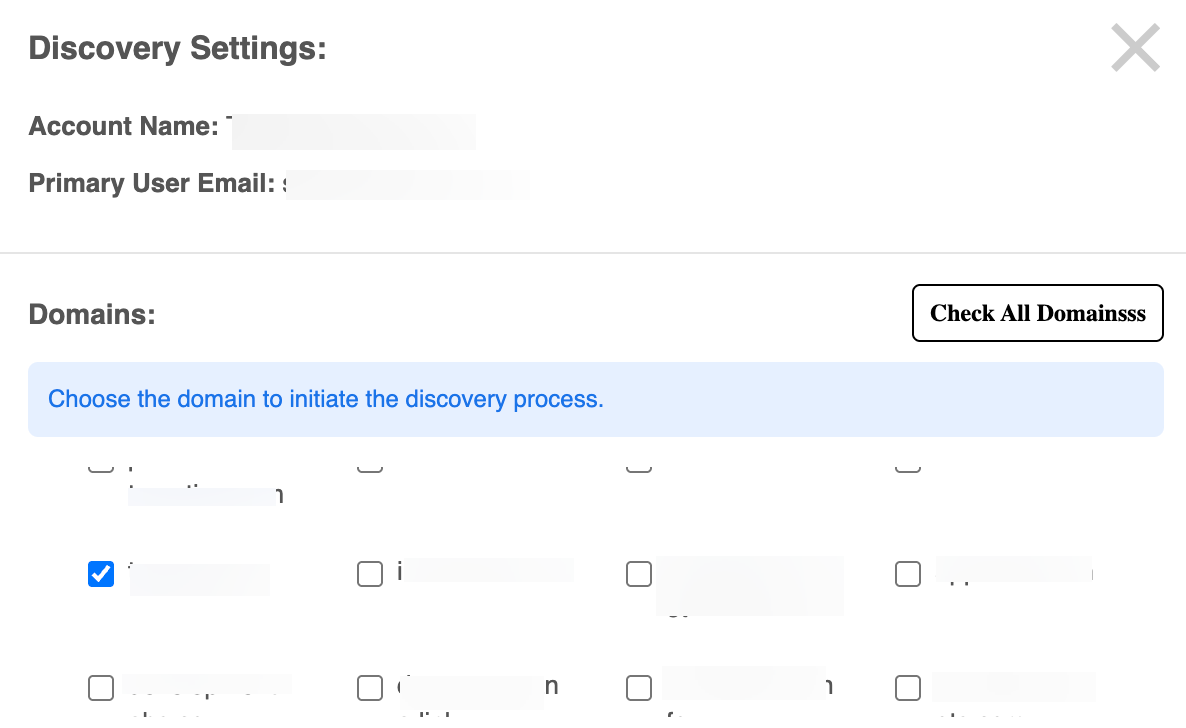
The Discovery Settings window opens for initiating a discovery process on specific domains and TLDs (Top-Level Domains).
Domains
- Choose the domain to initiate the discovery process -A list of domains is displayed with checkboxes next to each one:
- Check All Domains: This button will select all domains in the list at once for the discovery proces
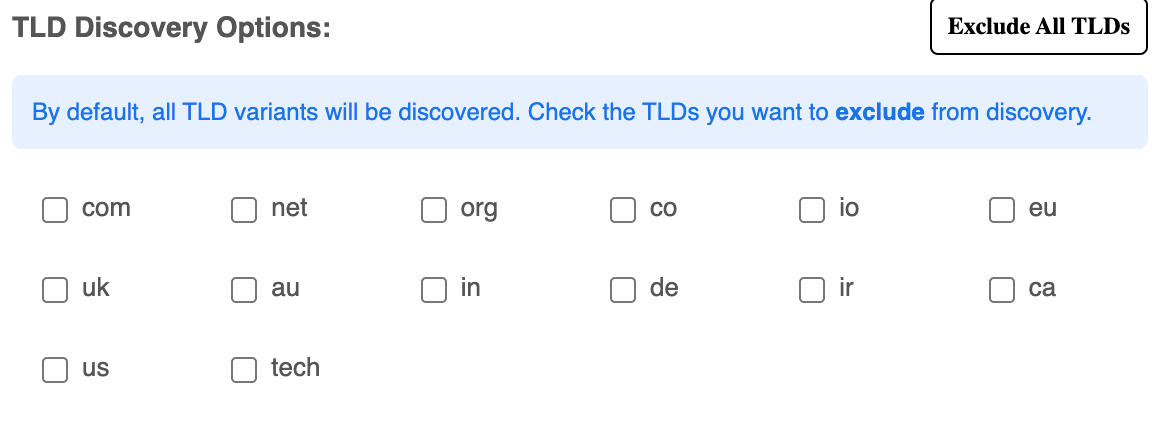
TLD Discovery Options:
This section allows you to select or exclude specific TLDs (e.g., .com, .net, .org, etc.) during the discovery process.
Users can uncheck any TLD they wish to exclude from the discovery process (e.g., .co, .io, .eu).
Exclude All TLDs: Clicking this button will uncheck all TLD options, effectively excluding all TLDs from the discovery.
Note: Unless specified otherwise, the tool will consider all possible TLD variants for discovery
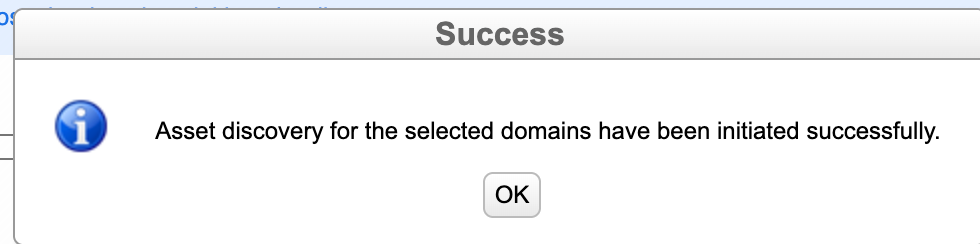
Start Discovery: Once the domains and TLDs are selected, you can click this button to initiate the discovery process.
A confirmation window will popup:
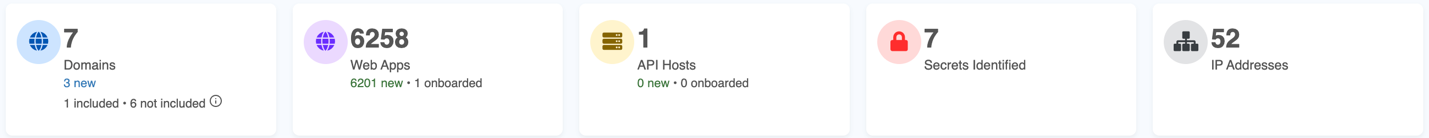
Key Security Metrics
This section presents a high-level summary of key metrics about your digital assets.
| Parameters | Descriptions |
| Domains | Displays the total number of domains being monitored. It also shows how many are actively included in the scan and how many are not. |
| Web Apps | This section tracks the total number of web applications identified across the environment, including the ones that are actively monitored. |
| API Hosts | Displays the number of API hosts, which are critical for any API-based services. This section helps monitor their status and security posture. |
| Secrets | Represents the number of sensitive data or secrets, like API keys or credentials, that have been detected in the scanned assets. |
| IP Addresses | Provides a count of the IP addresses related to the monitored assets, helping to track exposure at the network level. |
Key Asset Views
This section allows you to filter the displayed data based on specific criteria
Tab | Description |
|---|---|
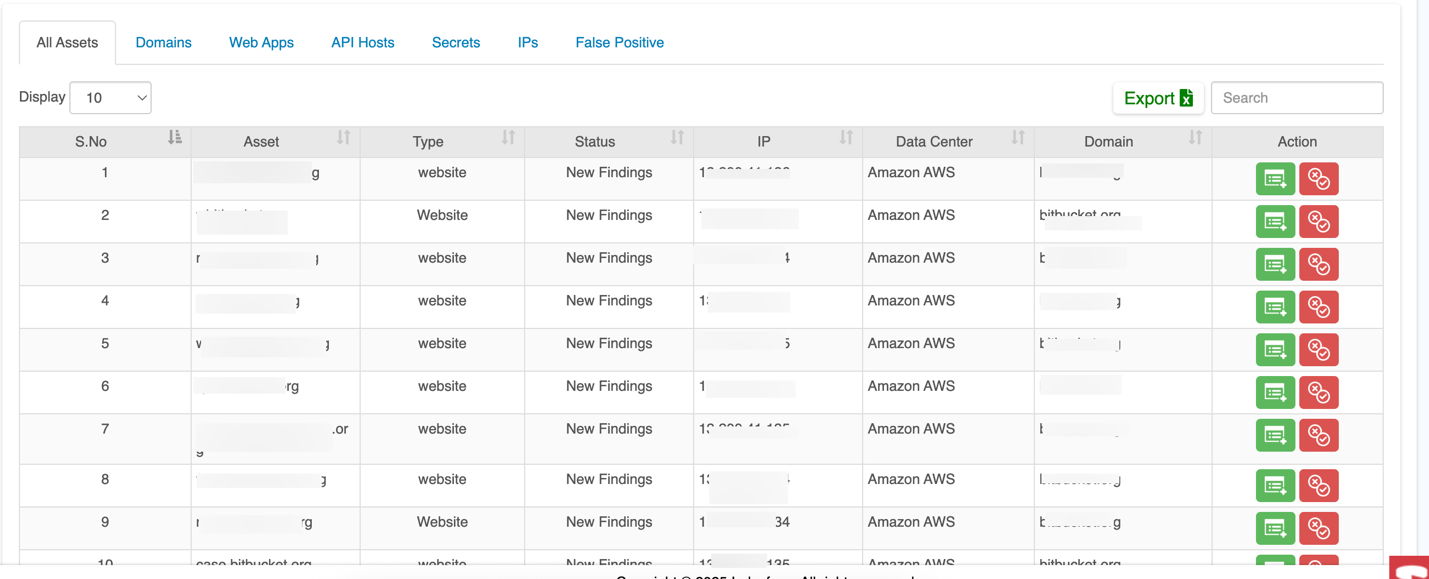
| All Assets | Displays a comprehensive list of all assets that are being monitored, including domains, web apps, and other resources where vulnerabilities or secrets have been detected. |
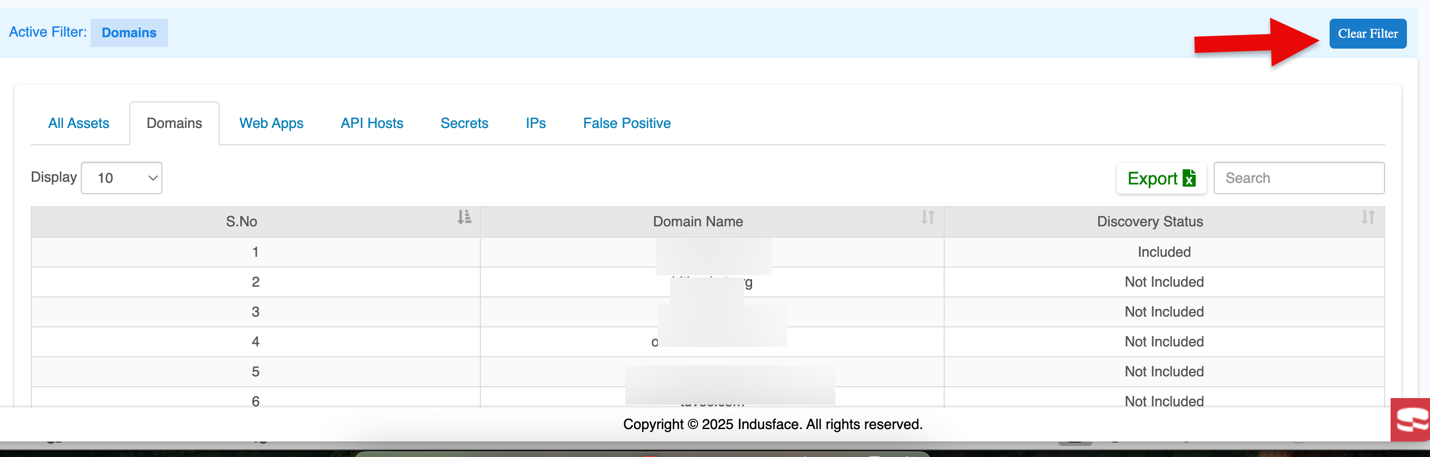
| Domains | Shows a list of domains that have been onboarded and where secrets or vulnerabilities are identified. It typically includes the domain name and other relevant details like severity of the issue. |
| Web Apps | Displays detected vulnerabilities or secrets related to web applications. This tab includes information about the app, such as its URL, associated domain, file paths, and any exposed secrets. |
| API Hosts | Provides a list of API hosts where secrets (such as API keys, tokens) or vulnerabilities have been detected. The information includes the API host, the secret found, and its location. |
| Secrets | Focuses specifically on secrets (such as API keys, tokens, or other sensitive data) that have been exposed or detected within files or code on various assets. Each entry includes the secret's location and severity. |
| IPs | Displays the IP addresses that are connected to detected vulnerabilities, offering insights into the source or destination of malicious or unauthorized activity associated with the vulnerabilities. |
| False Positive | Identifies potential false positives — vulnerabilities or secrets that were flagged as issues but have been verified as non-issues. This tab helps reduce noise by showing false alarms. |
When you click on Clear Filter, it resets any active filters and takes you back to the All Assets tab.
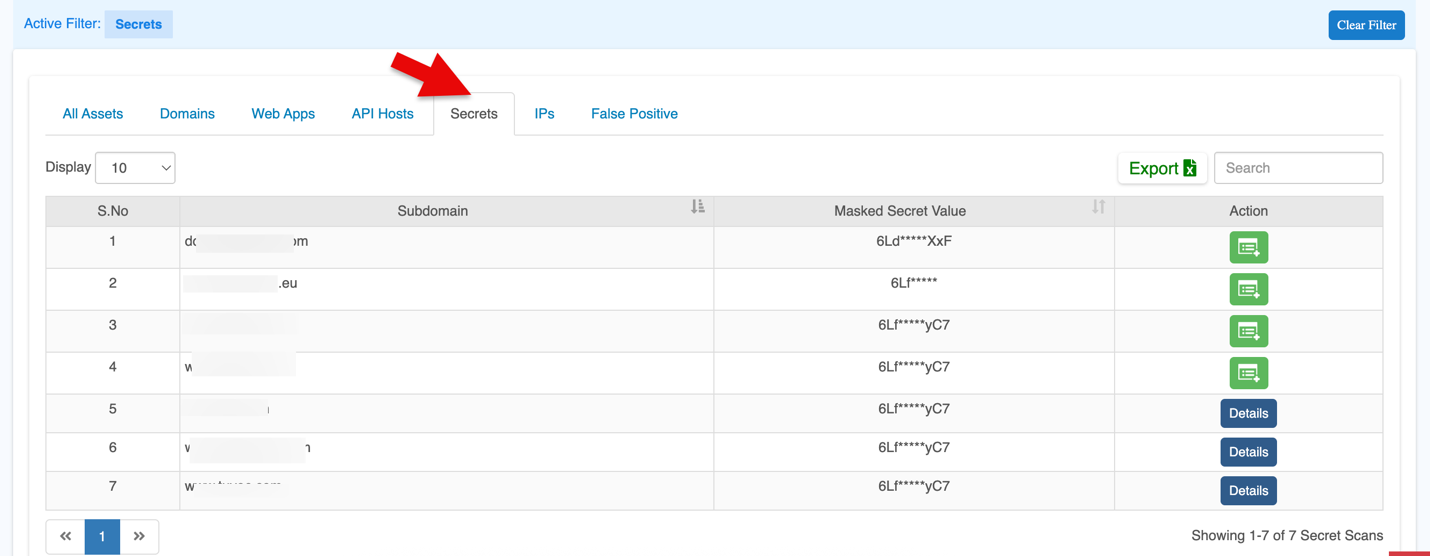
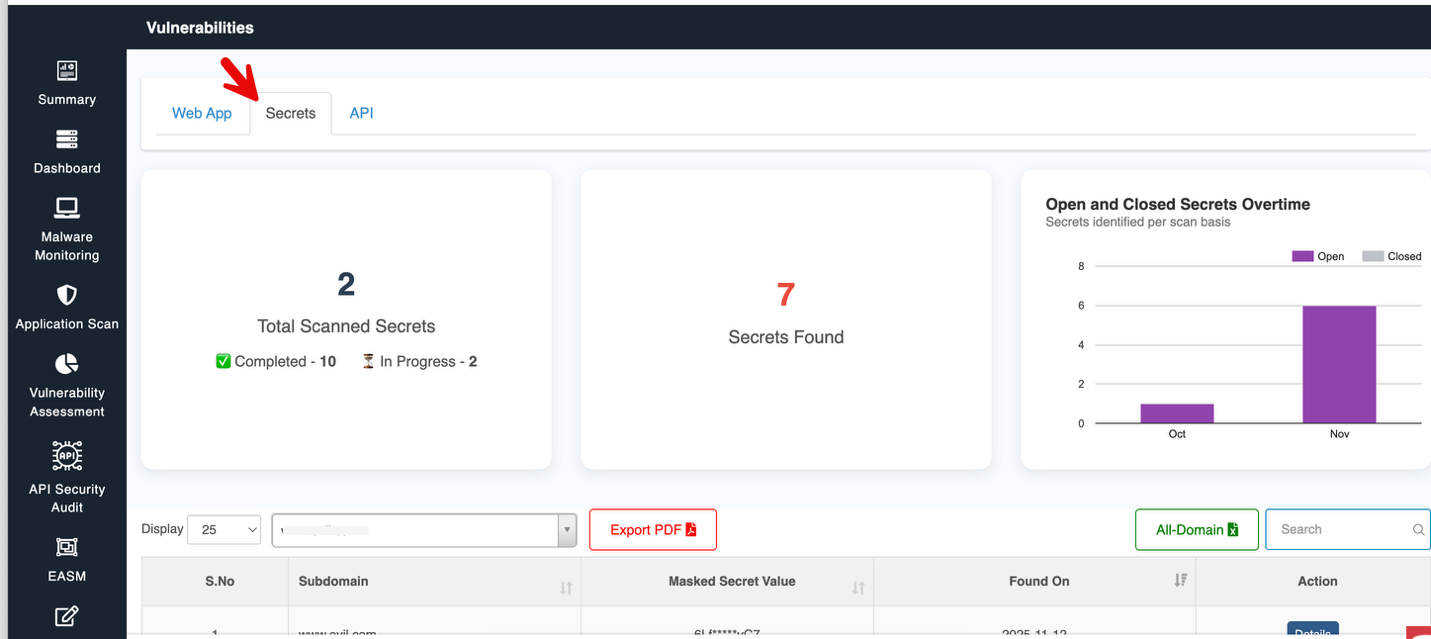
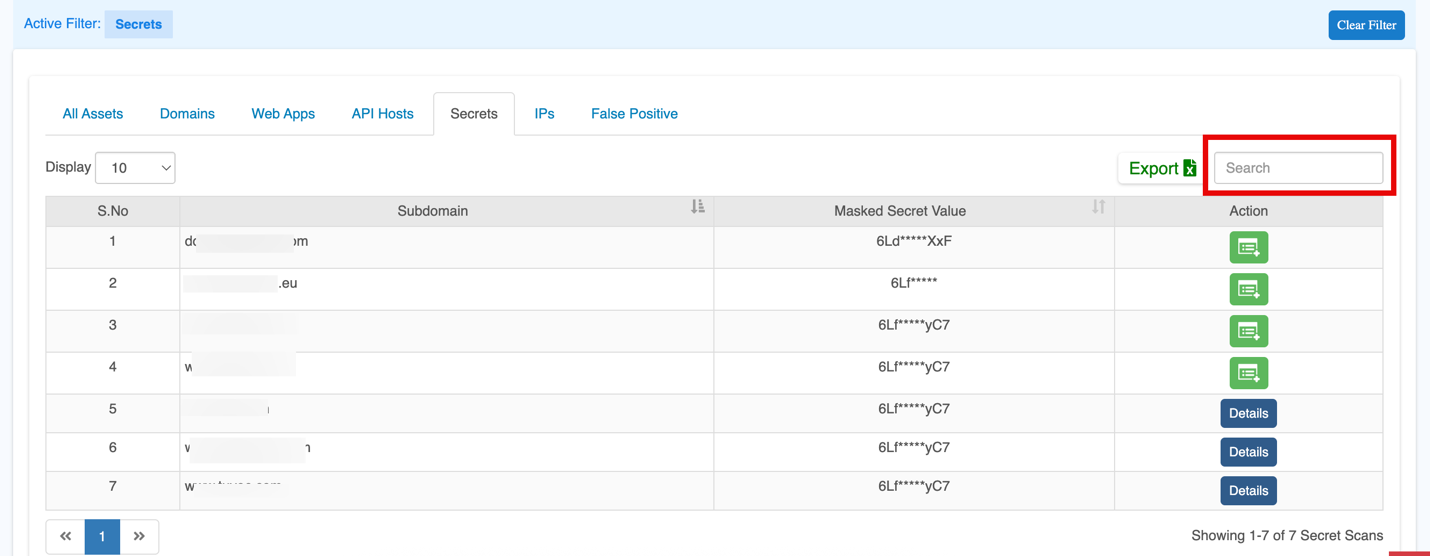
Secrets
This section give an overview of the assets containing secrets:
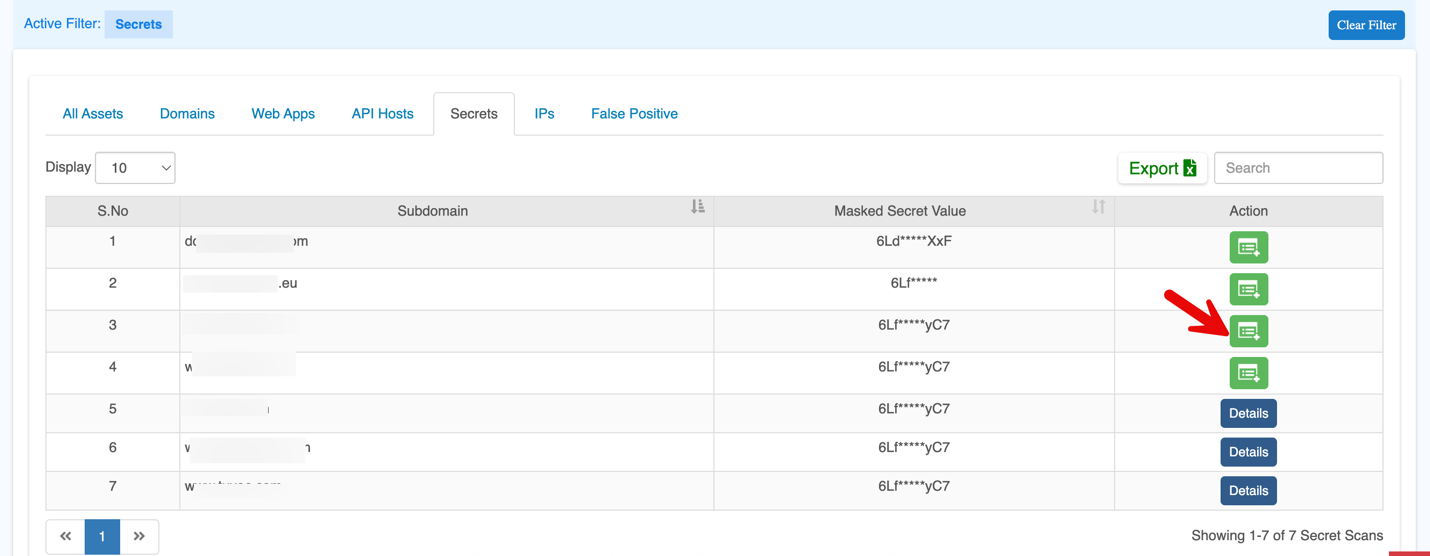
| Parameters | Descriptions |
| Subdomain | Any subdomain associated with the asset, which helps identify the specific section of the organization’s digital footprint.
|
| Masked Secret Value | The actual secret value with part of it masked (for security reasons). |
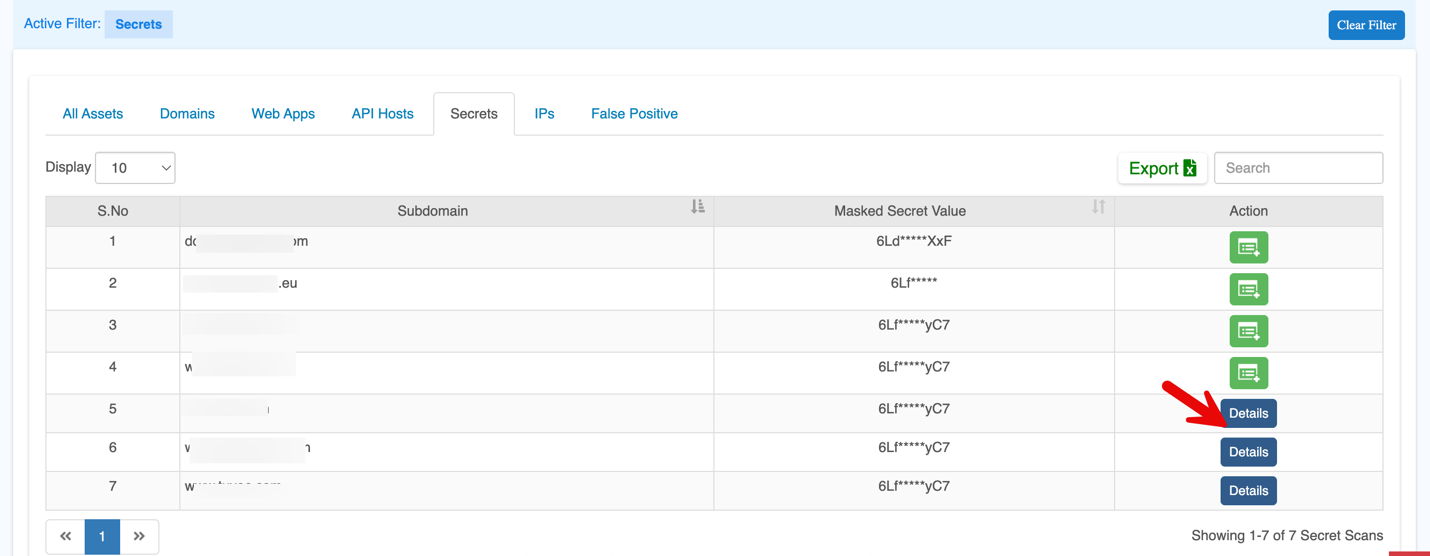
| Action | Shows available actions. For onboarded domains, click Details to view more information. If not onboarded, use Add Website to include it. (If a domain has not completed verification or setup, the platform shows this option so the user can onboard it.)
|
Actions
Secrets Overview in Vulnerabilities
By clicking Details, you can view the complete information about the secrets and navigate to the Secrets tab in Vulnerabilities.
For comprehensive information about identified secrets, their severity and action taken, refer to the Vulnerbailities - > Secrets Documentation.
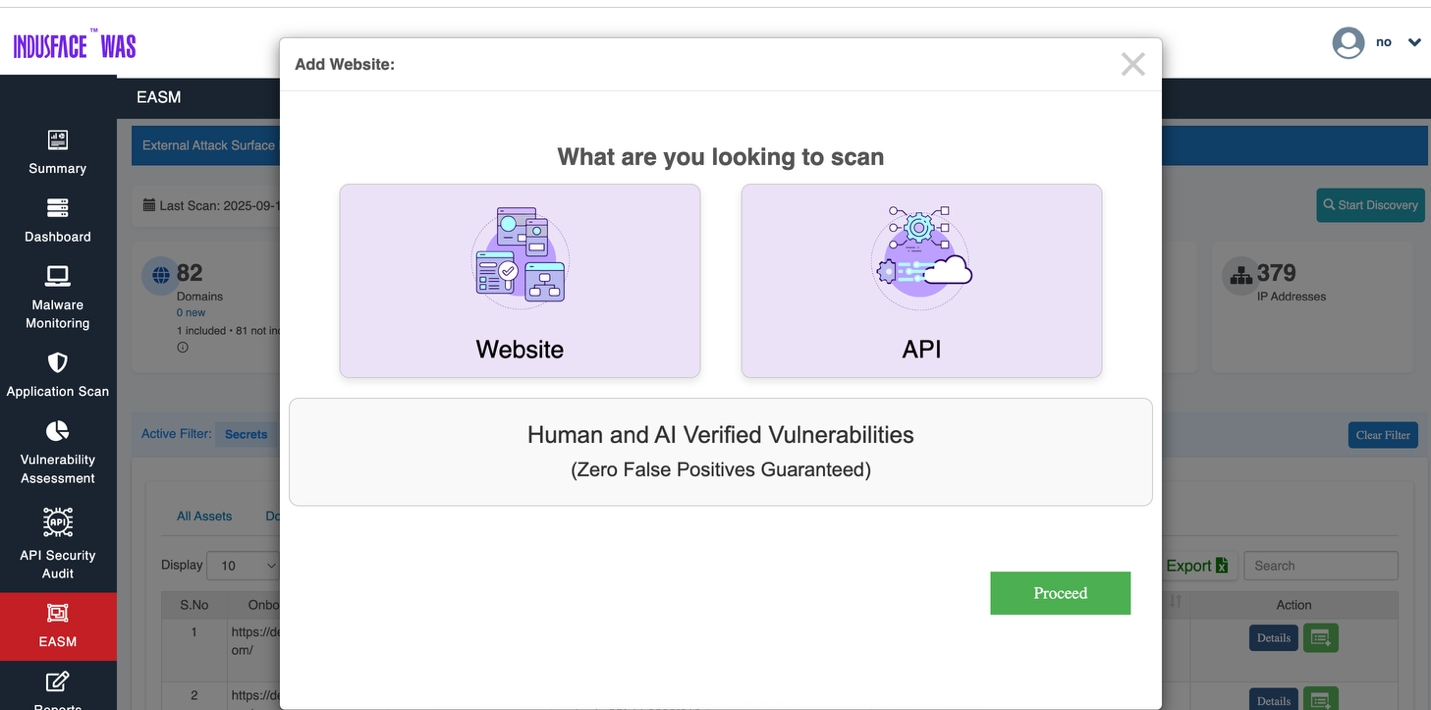
Add Website
Click the Add Website button to onboard a new application or API.
For step by step guide on adding new webiste, refer to the WAS Consulting License documention.
Asset Control and Filter Options
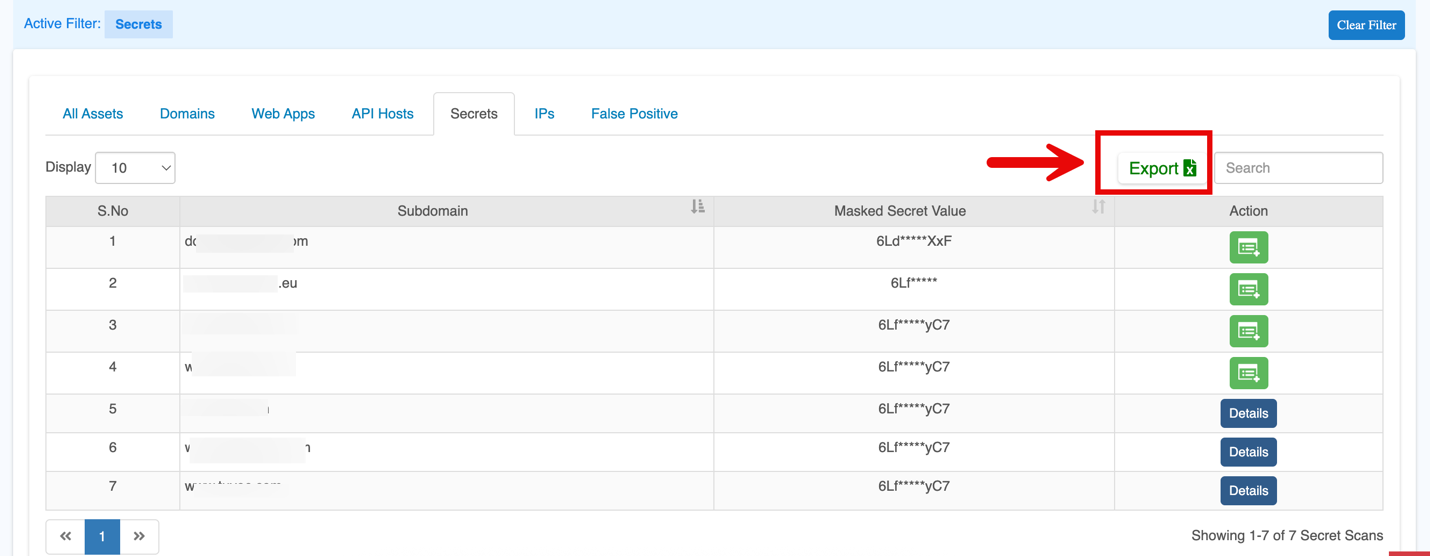
Export
Allows to export the secrets or asset findings into CSV format for further reporting or analysis. The exported report will include secrets only for the onboarded sub-domains.
Search
The search bar helps you quickly find specific assets, secrets, or vulnerabilities by entering keywords or applying filters (e.g., subdomains, severity level).