SIEM Integration through API
This document provides information on how to use Indusface SIEM service.
Connector Registration
- To use SIEM service, customer must register for the connector in Apptrana portal.
- Connector registration is done based on customer's request.
- For connector registration, contact our support.
- Once the registration is completed successfully, the Connector Name, API ID, and Key are displayed in API Integration section.
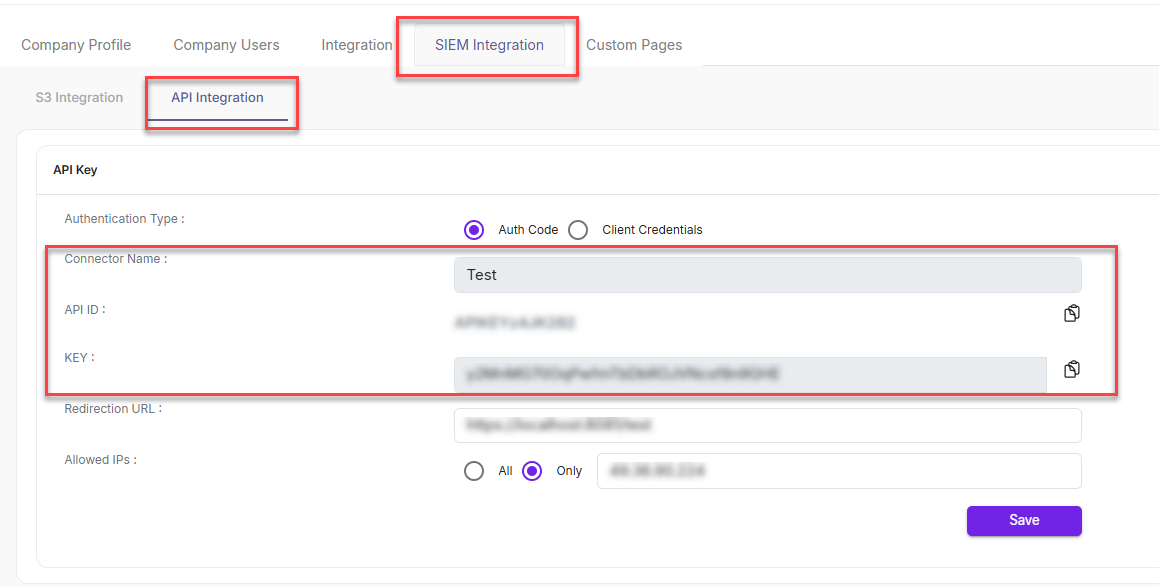
Authorization Code
Client must get authorisation code to get the access token.
Follow these details to get authorisation code:
Endpoint : https://tas.indusface.com/wafportal/rest/siem/v1/authorize
Method: GET
Header: "Content-Type":"application/json"
Query param: client_id (use API ID from Apptrana portal)
Authorisation code will be sent back in the query string of the pre-configured redirection URL.
Generate Token
- To access SIEM API, client must get authenticated through clientKey, clientSecret and authorisation code(use copied API ID and Key generated at portal).
- On successful authentication, sever will issue access token which is valid for 24 hours. Client must use this token for subsequent request.
The API details for the same are:
Endpoint: https://tas.indusface.com/wafportal/rest/siem/v1/getAuthToken
Method: POST
Header: “Content-Type”:” application/x-www-form-urlencoded”
Authentication: Client Id, Client secret and authorisation code should be passed in body( parameter name should be client_id,client_secret and code).
Success Response:
Status Code: 200
{"access_token":"{token}","token_type":"Bearer","expires_in":86400}Error Response:
Status Code: 401 Unauthorised
{"errorMessages":["Unauthorised"]}Get Attack Details
Client can retrieve attack details from the time SIEM service is enabled in portal and details are available up to 30 days. The following parameters are supported.
Time range: This is a mandatory field. Specify startTime and endTime in milliseconds (UTC) and maximum time range allowed is 5 mins.
eventType: It is either Log or Block. When not specified, it will respond to both Log and Block.
access_token: It is mandatory while requesting and should be passed in Authorisation header.
websiteName: Name of the website for which details should be retrieved. If website is not specified, API will respond with all the websites. It is recommended to specify the website name.
API details for the same are as follows:
Endpoint: https://tas.indusface.com/wafportal/rest/siem/v1/getAttackInfo
Header: "Content-Type":"application/json" and "Authorisation" : " Bearer {access_token}"
Request Body without website:
{
"startTime":"1547190000000",
"endTime":"1547186100000",
"websiteName":"www.abc.com"
}Success Response:
Status Code: 200
{
"successMessage":"Success",
"data":[
{
"websiteName":" www.abc.com ",
"attacks":[
{
"attackerIP":"52.66.186.232",
"attackerGeo":"IN",
"severity":2,
"eventType":"Log",
"attackTime":"2019-01-11T05:54:02.091Z",
"attackUri":"/rm/email/send",
"target":null,
"attackData":"curl/7.29.0",
"ipReputation":"UNK",
"category":"Bot Attacks",
"ruleId":"40",
"requestId":"XDgvJ11cQNtD@oi4vIg3fwAACDg",
"ruleName":"Request Indicates an automated program explored the site",
"tagName":"WEB_ATTACK/AUTOMATION/SECURITY_SCANNER",
"hostName":" www.abc.com ",
"statusCode":200,
"requestHeader":"\"Host\":\" www.abc.com \" , \"User-Agent\":\"curl/7.29.0\",\"Accept\":\"*/*\",\"Accept-Language\":\"-\",\"Accept-Encoding\":\"-\",\"Connection\":\"-\",\"Cookie\":\"-\"",
"responseHeader":"\"Cache-Control\":\"-\",\"Connection\":\"-\",\"Content-Type\":\"-\",\"Content-Length\":\"0\",\"Date\":\"-\",\"Keep-Alive\":\"-\",\"Server\":\"-\"",
"tlsVersion":"TLSv1.2",
"requestProtocol":"HTTP/1.1"
}
]
}
]
} Sample Curl request
curl --header "Content-Type: application/json" --header "Authorisation: Bearer {access_token}" --request POST --data "{ \"startTime\":\"1547185800000\",\"endTime\":\"1547186100000\"}" https://tas.indusface.com/wafportal/rest/siem/v1/getAttackInfoError Response
Status code: 400 on bad request
Status code: 401 on unauthorised access
Status code: 500 on server error
