Manage Vulnerabilities
Introduction
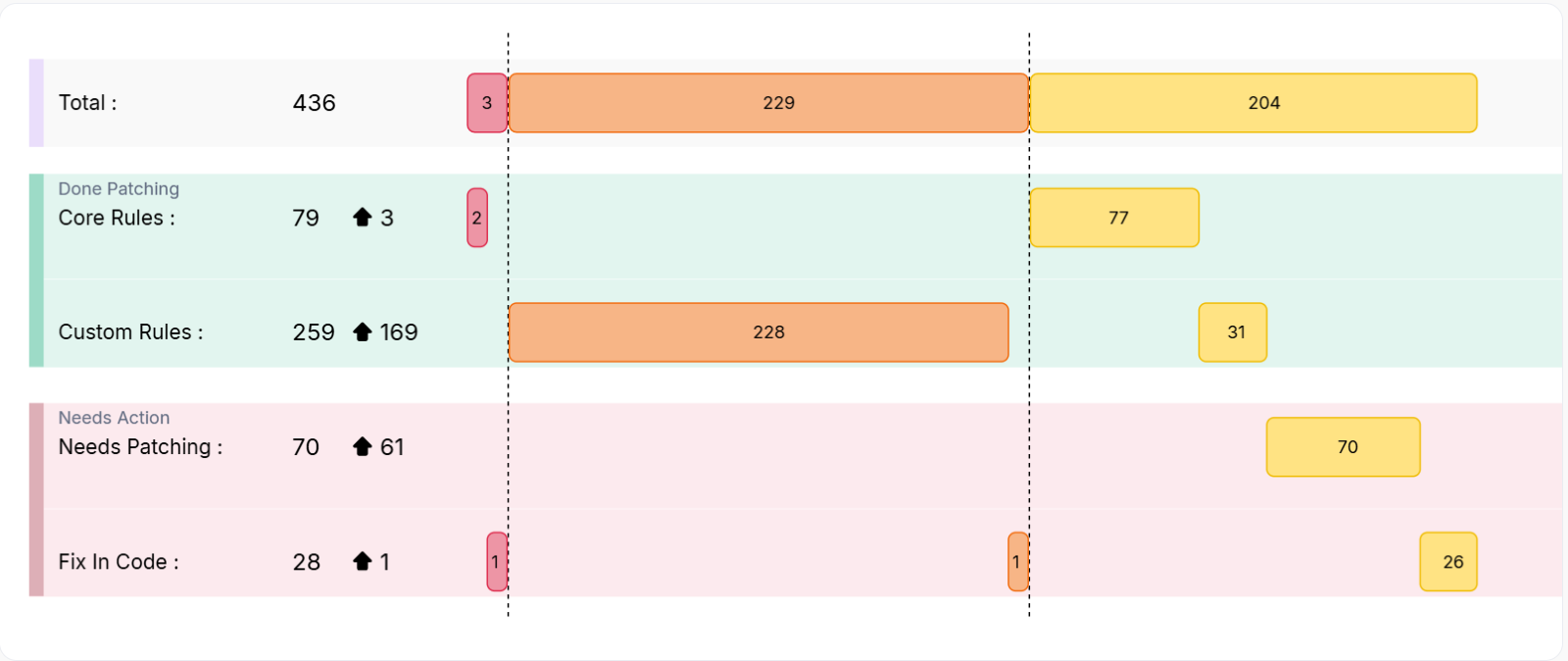
All vulnerabilities are categorized into three sections: total vulnerabilities, patched vulnerabilities, vulnerabilities that need patches and those requiring code fixes.
The number of critical, high, and medium severity vulnerabilities is displayed separately for each category.
The change in the number of vulnerabilities (increased or decreased) compared to the previous period (last 7 days, last week, last 30 days, or last month) is also shown.
Vulnerability Details
This section displays the maximum number of vulnerabilities for the top 5 categories. A summary is displayed to understand which vulnerability category contains the highest open vulnerabilities.
Top 5 vulnerability categories for:
- All unpatched vulnerabilities
- Patched by core rules
- Patched by custom rules
- Needs virtual patching
- Needs fix in code

Last 5 Scans
The bar graph displays the data of patched vulnerabilities and those requiring action or fixing from the last five scans.

Scanning Methods
There are three different scanning methods available.
- Auto-Scan
- Manual Pentest
- API Scan
Auto Scan
Auto Scan allows customers to discover the vulnerabilities of web apps and displays the last scan details and number of vulnerabilities detected in the last scan. Additionally, if a customer initiates a new scan, that information is also included in this section.
- Click Start Scan.
- A confirmation pop-up appears. Click Confirm to proceed further.
Configure Auto Scan Settings
- Click on the
icon in Auto Scan section.
| Parameter | Description |
| URL | Enter the URL that needs to be scanned. |
| Global | A toggle switch is given to apply these changes to all applications associated with your account. 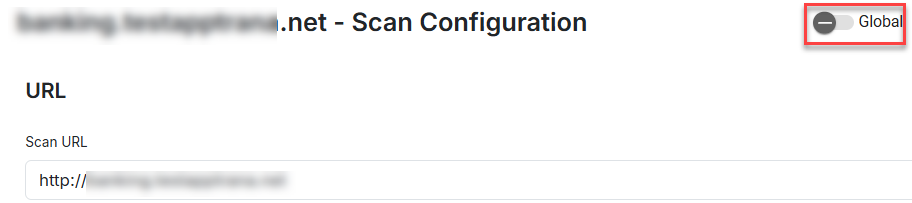 |
| Scan Options |
 |
| Schedule Scan |
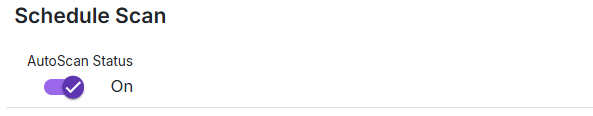
|
| Custom Timing Details |
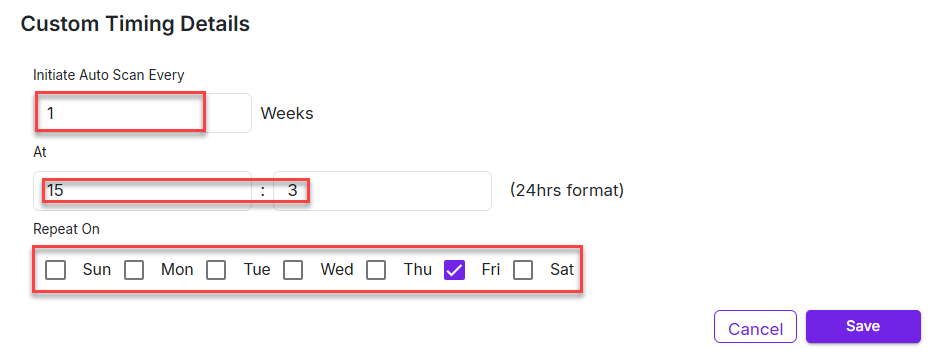 |
Download Auto Scan Report
- Click Download Report.
- The report exported into PDF format.
- The report includes details of scan summary, number of vulnerabilities detected and their severity, vulnerability trend for last 5 scans, and so on.
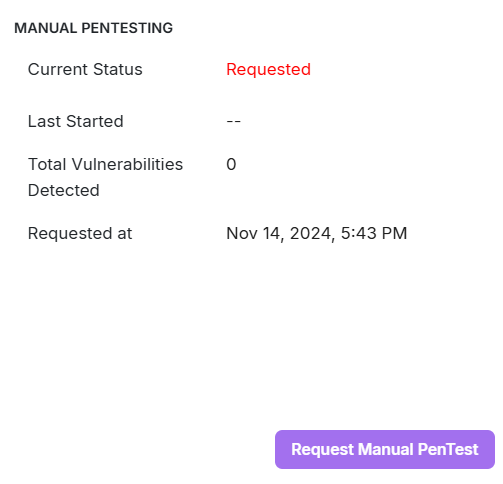
Manual Pen Test
The Manual Pen Test detects the vulnerabilities which are unable to be identified during the Auto Scan. The Manual PenTest section displays the details of the start date of pentest, number of vulnerabilities detected, requested date.
- Select a website for which you want to initiate Manual PT.
- Click Request Manual PenTest.
- Result: A confirmation pop-up appears.
- Provide the confirmation and the request will be forwarded to our AppTrana team.
API Scan
- From the application menu, select the API application.
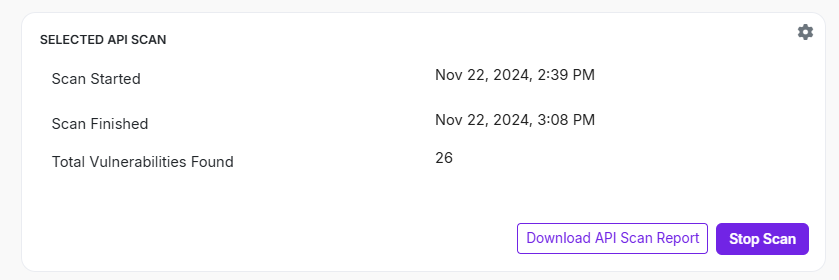
- Navigate to Selected API Scan field.
- This section indicates the recent API scan details, such as scan start date, finished date, and total number of vulnerabilities identified during the recent scan.
- Click API Scan to start API scan.
Configure APIs
- Click the
icon in the Selected API Scan field.
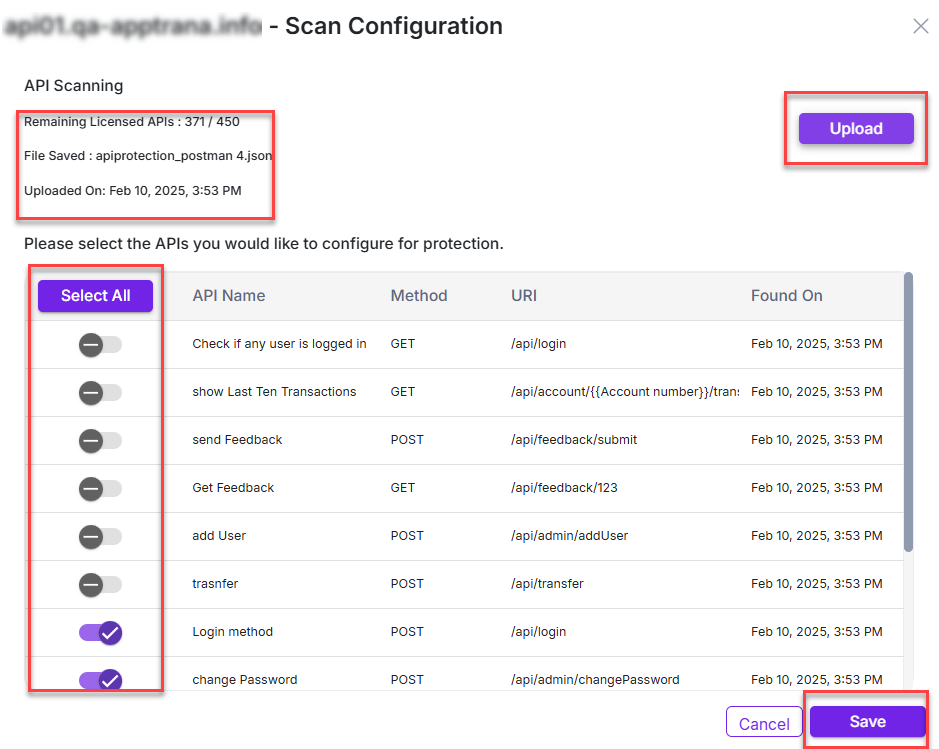
- Result: The API Scan configuration pop-up window opens.
- The system displays the number of remaining licenses available for the API scan and the uploaded Postman filename.
- Click the Upload button to upload a new postman file.
- Once you upload the Postman file successfully, the system displays a list of all APIs from the file in the table.
- You can identify the API details such as API name, endpoint method, URI, and the date the API was found.
- Select the APIs to scan. To scan all APIs, click Select All.
- Once the configuration is finished, click Save.
Download API Scan Report
- Click Download API Scan report.
- The report exported into PDF format.
- The report includes details such as API scan summary, number of vulnerabilities identified, severity, and so on.
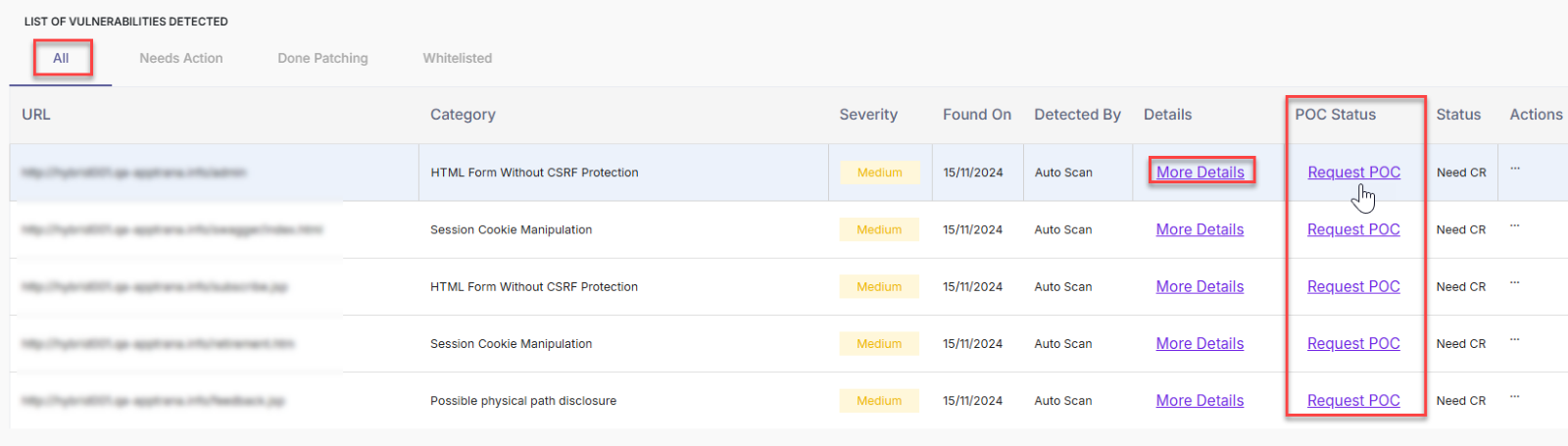
List of Vulnerabilities Detected
This section details the list of vulnerabilities identified during the Auto scan, Manual PT, and API scan.
There are 4 different sections available here.
All - A complete list of detected vulnerabilities at the site level, including details such as the URL, vulnerability category, date found, scanning method used, and more.
- Request POC: Click Request POC to see the proof or valid use cases to validate the feasibility of a concept.
- Result: A confirmation pop-up opens with a note saying POC takes at least 48hours. Provide the confirmation accordingly.
- More Details: This field allows you to see the full details of the vulnerability, such as description, solution, reference links, attack details, and so on.
- Click More Details.
- Allows you to request for SwyftComply report and request a Custom rule to fix the vulnerability.
- Request Custom Rule: To fix a specific kind of attack, click Request Custom Rule in the More details section.
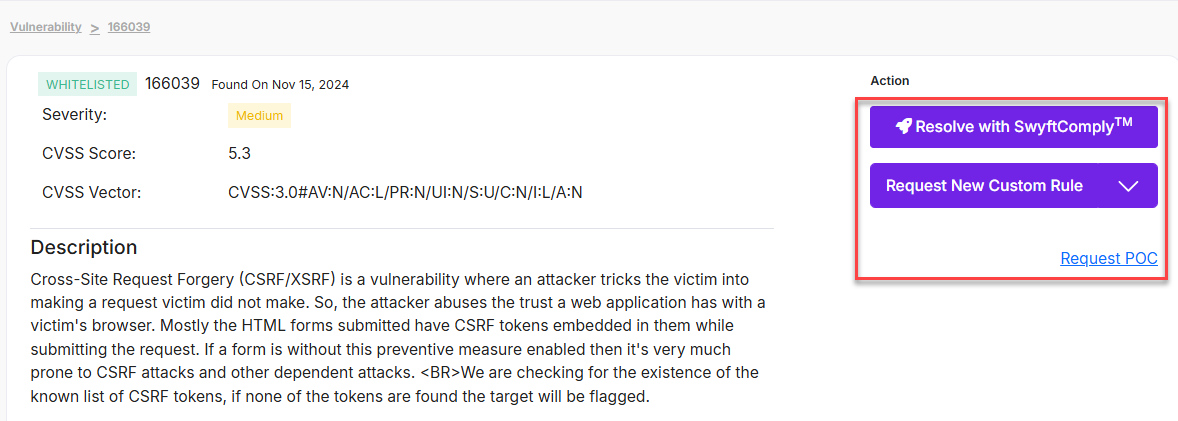
Needs Action – This field allows you to whitelist the vulnerabilities. Click here to understand more about whitelisting and unwhitelisting vulnerabilities.
Done Patching – All fixed vulnerabilities data is displayed here.
Whitelisted – The vulnerabilities and vulnerability categories which are whitelisted are displayed in this table.
