BOT Policies
Introduction
In an era where web applications face constant threats, effective bot protection policies are essential for safeguarding against malicious traffic.
Bot protection policies are specifically designed to defend web applications against harmful automated traffic. By implementing these policies, organizations can mitigate risks associated with bot attacks, ensuring the integrity and availability of their online services.
Navigate to WAAP Policies > List of Rules and Policies > BOT Policies.
This section briefs about the number of BOT policies enabled and recent actions made based on bot confident score.
The actions linked to the BOT Prediction score change according to customer settings. Customers can define specific actions for low, medium, and high scores.
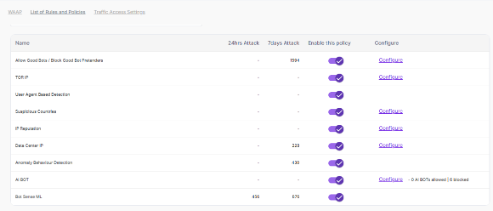
BOT Protection Policies
- Navigate to List of Rules and Policies > BOT Policies > Protection Policies.
- There are a total of 7 bot policies available.
- By default, all the policies are activated.
- The count of attacks received in the last 24 hrs and last 7 days after the policies are triggered.
- A search bar allows users to filter the policy by name and configure quickly.
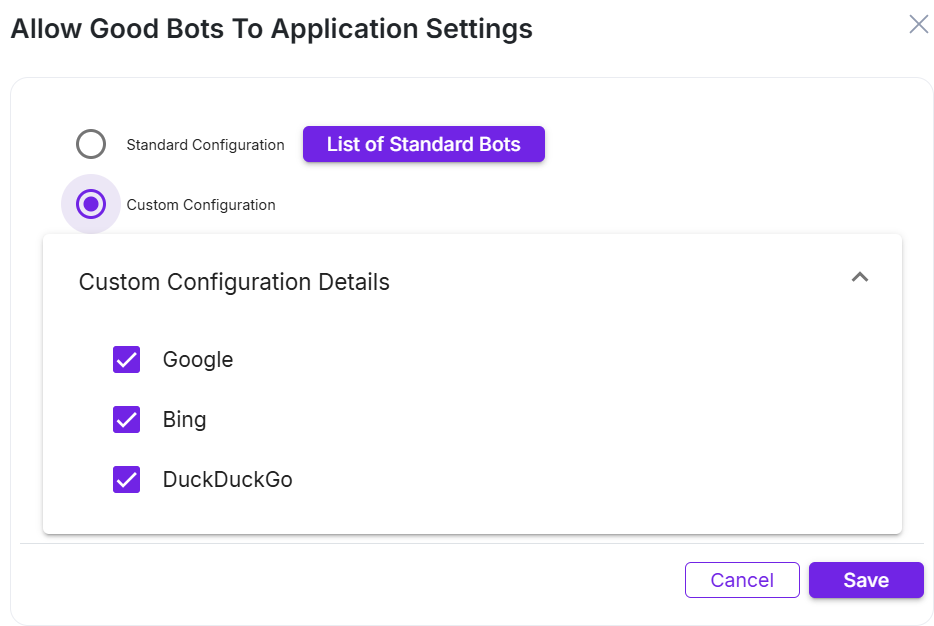
Allow Good BOTs and Block Good BOT Pretenders
- When the policy is in activated mode, it automatically allows the good bots and blocks the good bot pretenders.
- Click Configure to change the configuration in the policy. Two types of configurations are available.
- Standard Configuration: - This option allows the list of standard bots. Users can not remove certain bots.
- Custom Configuration: - There are 3 options given under custom configuration.
- Bing
- DuckDuckGo
By default, all the 3 options selected in custom configuration. Undo the checkmark to remove certain bots.
The maximum risk score for Good Bot Pretenders is 100.
TOR IP
- By default, the policy is available in activated mode.
- If a user selects to block all TOR IPs (from configure) and a request comes from the IP which is identified as TOR, then the risk score will be given as 100.
- If a user allows TOR IPs and a suspicious IP is detected, the risk score increases by 30.
- Click Configure to block the TOR IPs.

The maximum risk score for TOR IPs is 30.
User Agent Based Detection
- By default, the policy is available in activated mode.
- User agents help identify the nature of a request. Based on this information, a risk score is assigned.
- We have a database for user agents. If a request is detected from any of the user agents in data base, it automatically blocks.
The maximum risk score for User Agent Based Detection is 50.
Data Center IP
- We have a database for Data center IPs. The requests coming from Data center are mostly Bots.
- If you identify any attacks from a data center or server, click Configure and enable the policy. Once you enable the policy, it blocks all attacks from that data center or server.
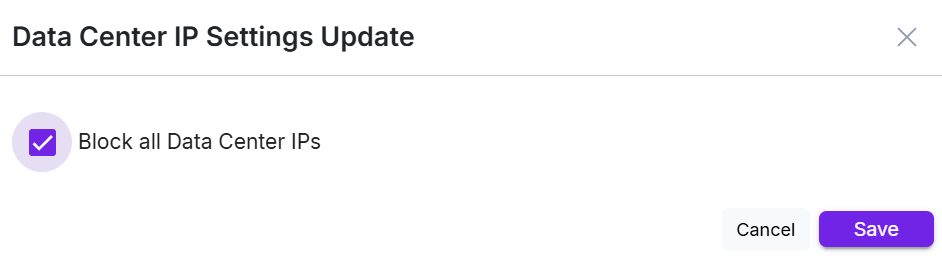
The maximum risk score for Data Center IPs is 30.
Suspicious Countries
- This policy helps to mark a country as suspicious instead of blacklisting the country. So, a request that comes from a suspicious country is used to determine the risk score of requests.
- Click the Configure icon on the right side to mark a country as suspicious.
- Click Add Country+ to add a country as suspicious.
- Click Delete Icon on the right side of the country to remove the country from blocklist.
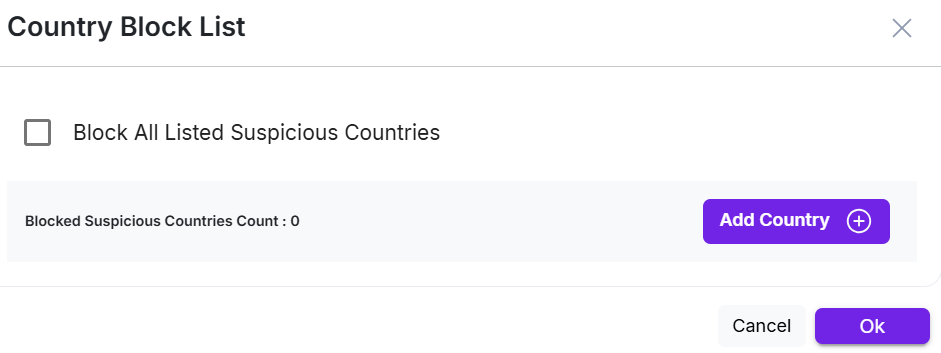
The maximum risk score for Suspicious Countries is 20.
IP Reputation
We have a database to identify the malicious IPs. If any malicious activity is identified from this IP, the risk score will be increased. When the risk score breaches the website threshold, the IP will be blocked automatically.
The maximum risk score for IP Reputation is 70.
To learn more about configuration: Visit ASN Based IP Whitelisting.
BOT Sense ML
Bot Sense ML is a machine learning-driven module that enhances application security. By analyzing traffic patterns and behavioral signals in real time, it accurately identifies malicious automated traffic while minimizing false positives.
This feature is available to AppTrana Advance Plus and Premium customers.
- By default, the policy is activated.
- The policy triggers when more than 60 requests are received from the same IP address and then all the subsequent requests are verified for legitimacy.
- The generated BOT Sense ML score is aggregated with the scores of other policies and then the risk score is evaluated accordingly.
The maximum risk score for the BOT Sense ML is 20.
LLM Crawler Monitoring
LLM Crawler Monitoring helps to understand the data of number of requests being made by AI Bots and the bandwidth used. The data helps you to make accurate decisions by monitoring and blocking crawlers as needed.
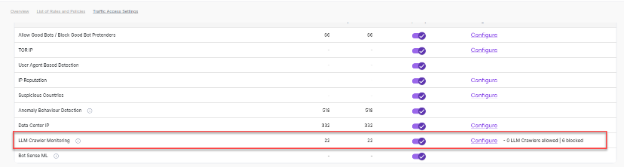
- Helps the users to monitor the traffic coming from the LLM Crawlers.
- User can see the data of LLM Crawlers for for the selected time period in the Bandwidth page.
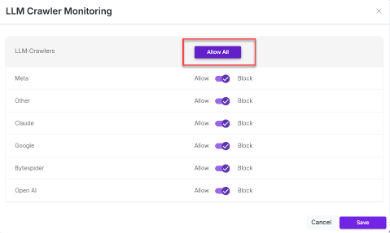
- The Configure button lets the user to Allow (or) Block certain LLMs.
- User can allow either certain LLM crawlers or allow all.
Anomaly Behavior Detection
- The policy works based on the cumulative attacks log data.
- If any attack is blocked by BOT module (TOR IPs, Good Bot pretenders, IP Reputation, and so on) or by Behavioral DDOS policy, then the risk score will not be calculated under anomaly behavior detection and then the policy will not be triggered.
- Irrespective of the type of attack (like Injection attack, Local file inclusion, cross-site scripting attack, and so on) on website, risk score will be calculated based on the attacks count and attacks severity.
- The attacks which are blocked by using core rules and custom rules, based on the severity of attack risk score will be calculated and the IP will be blocked once the risk tolerance level is breached.
Risk Score for Critical Severity– 10, Risk Score for High Severity – 5, Risk score for Medium Severity – 3
- When the risk score breaches the website threshold tolerance value, then the IP will be blocked for 10 min (TTL).
- During the blocking period, if an attack or a legitimate request is received from the same host IP address, that IP address will be blocked in the TTL period, but the TTL will not be refreshed.
- Once the TTL is completed, again the risk score will be calculated, and then the policy will be triggered based on the tolerance level.
The maximum risk score threshold for anomaly detection is 100.
Anomaly Behavior Detection policy is now only available for Premium and API plan customers.
How Does Anomaly Behavior detection work?
Walk through the following example for a better understanding.
Case 1 | Policy | Risk Score | Total Risk score = 70 |
| IP Reputation | 20 | ||
| TOR IP | 30 | ||
| Data center IP | 40 | ||
As per the tolerance level IP will be blocked only if the risk score is >60. Here the combined risk score is >60. So, this IP can be blocked. | |||
Case 2 | Policy | Risk Score | Total Risk Score = 40 |
| IP Reputation | 10 | ||
| TOR IP | 20 | ||
| Data Center IP | 10 | ||
Here the combined risk score is <60. So, this IP can be locked under IP reputation/ TOR IP/ Data Center IP. However, anomaly detection policy will be triggered once the risk tolerance level is breached. | |||
Case 3 | Policy | Risk Score | Total Risk Score = 90 |
| Attacks patched by Core rules | 20 | ||
| Attacks patched by Custom rules | 70 | ||
Here the combined risk score is >60 and anomaly detection policy will be triggered and blocks the IP for 10min. | |||
