Discover APIs
Introduction
API Security Policies play a crucial role in safeguarding the communication between systems and ensuring that APIs are properly managed and protected. These policies are particularly important once a website has been onboarded and successfully accessed, as they provide a framework for discovering, securing, and monitoring APIs.
In this document, we will explore how API Security Policies facilitate the discovery of APIs.
- Navigate to Applications & Groups.
- Select an API site from the All Domains drop-down tab.
- Go to Discovered APIs Section.
Discovery Summary
The summary shows the total APIs discovered, total approved APIs, APIs waiting for review, and Sensitive APIs.
APIs that consist of tags in it are considered as Sensitive APIs.
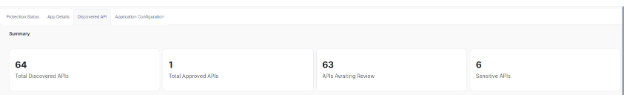
The APIs that consist of tags are considered as sensitive APIs.
An API is marked as Modified when any of its parameters are changed during a subsequent discovery. Once an API is in the Modified state, the user must review it and update its status to Approved.
Discovered APIs
This section shows the details of number of endpoints used and the remaining endpoints scan capacity. Additionally, the name of the swagger file uploaded, and the last date and time of swagger file uploaded is displayed here.
A search bar is given to allow the users to search the endpoint by name, type, and label.
Also, users can apply various filters to select specific APIs by HTTP methods, Type of APIs (Sensitive APIs and Authenticated APIs), and API Status.

All the APIs discovered during onboarding are displayed on the table.
| Parameter | Description |
| API | The API endpoint column displays the full URL or path of the API that was discovered during the onboarding process. |
| Discovered on | This field shows the date and time when the API was discovered |
| Methods | The HTTP method (e.g., GET, POST, PUT, DELETE) indicates the type of requests that can be made to the API. If an API has 2 or more methods then that API will be clubbed as per the methods. |
| Authenticated | The authentication status indicates if any authentication is required to access the API. |
| Tag | We have three different tags. PCI – Payment Card Information Deals with payment cards, such as credit cards and debit cards PII – Personally Identifiable Information Deals with a broad range of personal information. PHI – Protected Health Information Deals with health-related data. |
| Status | When the API is discovered, the status shows pending. Customers change the status to deprecated or approved from the configure menu. |
| Action | This field allows customers to configure the API policies. |
Configure Discover Policy
Click the Configure button on the API Discovery table.
There’re three different sections present.
- General
- Details
- Policy Enforcement
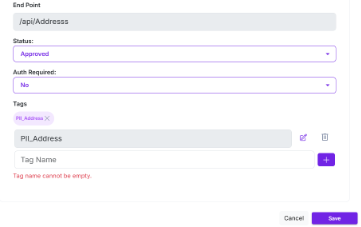
General: Once the parameters are set, click Save to apply the changes.
| Parameter | Description |
| Endpoint | This field displays the endpoint name and cannot be edited. |
| Status | This field allows the user to set the status as approved or blocked. If a user sets the status as approved, then the user must select the appropriate actions from the policy enforcement section. |
| Auth required | There is a drop-down menu given for the use to set either YES or NO, which means authentication is required or not to access the API. |
| Tags |
|
Details: This section displays details of different parameters used in the API, such as query, path, and body parameters. Also, it displays different http methods to call the API.
Users can click on any of the methods identified and can see their parameters.

Policy Enforcement: This part triggers when the user sets the API status as approved, which means approving API to use and confirming that it meets the security and operational standards.
There are five different parameters given for the positive security model. Based on selecting the parameters positive security model applied to the API accordingly.
- Blocks this API - When a user selects the option Block All Requests For This API, the system disables the positive security model for the API and blocks access to API.
- Block new Methods - When userselects this option, the system disables positive security model for the all the new methods of same API.
- Enforce path parameters - The positive security model applied only when the endpoint contains path parameters. Example: GET /users/{userId}/posts
- Enforce query parameters – The positive security model applies when the endpoint contains query parameters. Example: GET /search?query=shoes
- Enforce body parameters: The positive security model applied when the API must contains body parameters. Example: Name, email, password
Upload APIs
- Click Upload APIs.
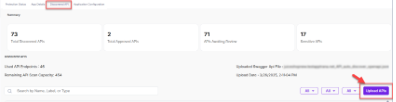
- A pop-up opens to upload a swagger file.
- Once the file is added, click Upload.
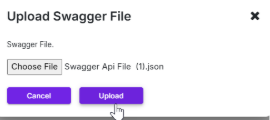
- After the file uploads successfully, the system displays the file's information, including the number of endpoints used, the remaining endpoints for scanning, the file name, and the upload date and time.
Download APIs
Users can download a single, multiple, or all APIs using the checkboxes.
When a user clicks on the checkbox of a specific APIs or selects all APIs, then the Download APIs option triggers in the bottom.
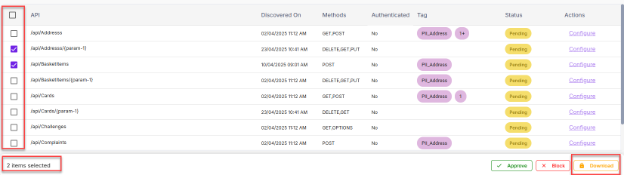
Users can also approve or block multiple or specific APIs by selecting checkboxes.
Enable/Disable APIs
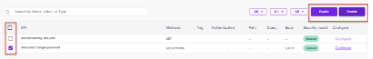
- Navigate to WAAP Policies > List of Rules & Policies > API.
- A table is given to display the approved and deprecated policies.
- This section allows users to enable or disable the positive security model to the API.
- Click the specific checkbox to enable/disable the security model.
- A confirmation pop-up appears. Click Confirm.
Approve Deprecated APIs
- Download the API file.
- Open the API file in any notepad.
- Enter false in the deprecated field.
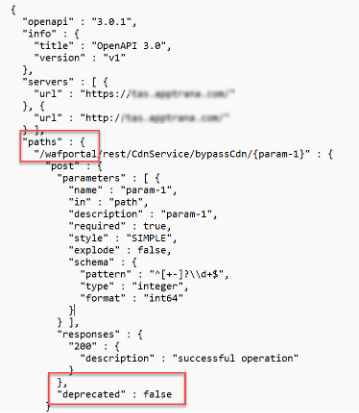
- Save the API file.
- Re-upload the saved file again.
- APIs will be approved automatically.
