AppTrana
Getting Started
Frequently Asked Questions
Product Details
API Scan Coverage for OWASP Top 10
Whitelist Vulnerabilities on the AppTrana WAAP
API Request to Purge CDN Data
Analysis page - Attack Trend Visualisation
Advanced Behavioral DDoS
BOT Protection
Asset Discovery
Customize Application Behavior with Bot Score
Restricted Admin User
Self Service Rules
Configuring Custom Error Page in AppTrana
Enabling SIEM Integration
API Discovery Feature
SwyftComply
Analysis page - Access Trend Visualization
Manage WAAP Email Alerts
Enable and Configure Single Sign-On
WAF Automated Bypass and Unbypass
False Positive Analysis Report on WAAP
Product User Guide
Indusface WAS
Getting Started
Product User Guide
Summary
Dashboard
Malware Monitoring[MM]
Application Audit[AA]
Vulnerability Assessment[VA]
Reports
Settings
Asset Monitoring
New Reporting Structure
Frequently Asked Questions
Feature Summary
AcuRisQ – Risk Management with Advanced Risk Scoring
WAS Consulting License
API Key Based - Scan Log Export
WAS Defacement Checks
SIEM Integration with Sumo Logic
Indusface WAS Scanned Vulnerabilities
Total Application Security
Onboarding Documents
Indusface Newsletter
Indusface Product Newsletter - October 2021
Indusface Product Newsletter- April 2021
Indusface Product Newsletter-January21
Indusface Product Newsletter - June 20
Indusface Product Newsletter - October 19
Indusface Product Newsletter - August 19
Product Newsletter of May 19
Product Newsletter of March 19
Product Newsletter of January 19
WAF Portal Revamp June 18
Product Newsletter of July 18
Product Newsletter of May 18
Product Newsletter of March 18
Product Newsletter of February 18
Product Newsletter of January 18
Indusface Product Newsletter - March 2022
Indusface Product Newsletter - February 2023
Indusface Product Newsletter- October 2022
Zero Day Vulnerability Reports
Vulnerabilities Detected in 2023
Vulnerability Report of May 23
Vulnerability Report of March 23
Vulnerability Report of August 23
Vulnerability Report of July 23
Vulnerability Report of April 23
Vulnerability Report of November 23
Vulnerability Report of June 23
Vulnerability Report of December 23
Vulnerability Report of February 23
Vulnerability Report of January 23
Vulnerability Report of September 23
Vulnerability Report of October 23
Vulnerabilities Detected in 2016
CRS vs. Zero Day Vulnerability - December 2016
CRS vs. Zero Day Vulnerability - November 2016
CRS vs. Zero Day Vulnerability - October 2016
CRS vs Zero Day Vulnerability - September 2016
CRS Vs Zero Day Vulnerabilities - August 2016
Vulnerabilities Detected in 2017
Vulnerability Report of April 17
Vulnerability report for Apr 3rd - Apr 9th 17
Vulnerability report for April 17th - Apr 23rd 17
Vulnerability report of April 10th - April 16th
Vulnerability Report of March 17
Vulnerability report for Mar 20th - Mar 26th
Vulnerability report for Mar 13th - Mar 19th
Vulnerability report for 27th Feb - 5th Mar
Vulnerability report for Mar 27th - Apr 2nd
Vulnerability report for Mar 6th - Mar 12th
Vulnerability Report of February 17
Vulnerability Report of January 17
Vulnerability Report of December 17
Vulnerability Report of November 17
Vulnerability Report of August 17
Vulnerability Report of September 17
Vulnerability Report of October 17
Vulnerability Report of July 17
Vulnerability Report of June 17
Vulnerability Report of May 17
Vulnerabilities Detected in 2018
Vulnerability Report of December 18
Vulnerability Report of November 18
Vulnerability Report of October 18
Vulnerability Report of September 18
Vulnerability Report of August 18
Vulnerability Report of July 18
Vulnerability Report of June 18
Vulnerability Reports of May 18
Vulnerability Report of April 18
Vulnerability Report of March 18
Vulnerability Report of February 18
Vulnerability Report of January 18
Vulnerabilities Detected in 2019
Vulnerability Report of December 19
Vulnerability Report of November 19
Vulnerability Report of October 19
Vulnerability Report of September 19
Vulnerability Report of August 19
Vulnerability Report of July 19
Vulnerability Report of June 19
Vulnerability Report of May 19
Vulnerability Report of April 19
Vulnerability Report of March 19
Vulnerability Report of February 19
Vulnerability Report of January 19
vulnerabilities Detected in 2020
Vulnerability Report of December 20
Vulnerability Report of November 20
Vulnerability Report of October 20
Vulnerability Report of Sep 20
Vulnerability Report of July 20
Vulnerability Report of June 20
Vulnerability Report of May 20
Vulnerability Report of April 20
Vulnerability Report of March 20
Vulnerability Report of February 20
Vulnerability Report of January 20
Vulnerabilities Detected in 2021
Vulnerability Report of November 21
Vulnerability Report of October 21
Vulnerability Report of September 21
Vulnerability Report of August 21
Vulnerability Report of July 21
Vulnerability Report of June 21
Vulnerability Report of May 21
Vulnerability Report of April 21
Vulnerability Report of March 21
Vulnerability Report of February 21
Vulnerability Report of January 21
Vulnerability Report of December 21
Vulnerabilities Detected in 2022
Vulnerability Report of January 22
Vulnerability Report of February 22
Vulnerability Report of March 22
Vulnerability Report of April 22
Vulnerability Report of May 22
Vulnerability Report of June 22
Vulnerability Report of July 22
Vulnerability Report of August 22
Vulnerability Report of September 22
Vulnerability Report of October 22
Vulnerability Report of November 22
Zero-Day Vulnerability Report - December 2022
Vulnerabilities Detected in 2024
Security Bulletin
Vulnerabilities 2024
Critical Apache OFBiz Zero-day AuthBiz (CVE-2023-49070 and CVE-2023-51467)
ScreenConnect Authentication Bypass (CVE-2024-1709 & CVE-2024-1708)
CVE-2024-1071 – Critical Vulnerability in Ultimate Member WordPress Plugin
Oracle WebLogic Server Deserialization
ApacheStructs_VG
Apache Struts 2 Vulnerability CVE-2023-50164 Exposed
Unpacking the Zimbra Cross-Site Scripting Vulnerability(CVE-2023-37580)
Adobe ColdFusion Vulnerabilities Exploited in the Wild
Remote Unauthenticated API Access Vulnerabilities in Ivanti
Multiple Moveit Transfer Vulnerabilities
HTTP/2 Rapid Reset Attack Vulnerability
Apache log4j RCE vulnerability
Table of Contents
- All Categories
- Security Bulletin
- HTTP/2 Rapid Reset Attack Vulnerability
HTTP/2 Rapid Reset Attack Vulnerability
 Updated
by Rama Sadhu
Updated
by Rama Sadhu
Google, Amazon Web Services & others disclosed a vulnerability in HTTP/2 protocol recently which is being tracked as “CVE-2023-44487”. The flaw lies in the way HTTP/2 protocol was implemented to increase the efficiency of transmitting various messages between end-points by “Stream multiplexing.
HTTP/2 protocol provides a mechanism for clients to request the cancellation of a previously initiated stream by transmitting an RST_STREAM frame to the server. This cancellation process assumes that the cancellation takes place immediately on the server side once RST_STREAM frames are received. But the client is allowed to send a reset stream immediately after sending the request frame, which is received by the server, processed, and rapidly resets. The requests are cancelled, but the connection remains open. As the cancellation is immediate and not dependent on the server side, the Client can initiate many such streams simultaneously, followed by streams containing HTTP/2 headers and/or data frames within the limit of concurrent allowed streams negotiated between the client and server. In a default HTTP/2 implementation, the server still needs to process the cancelled requests, eventually causing resource exhaustion on the server.
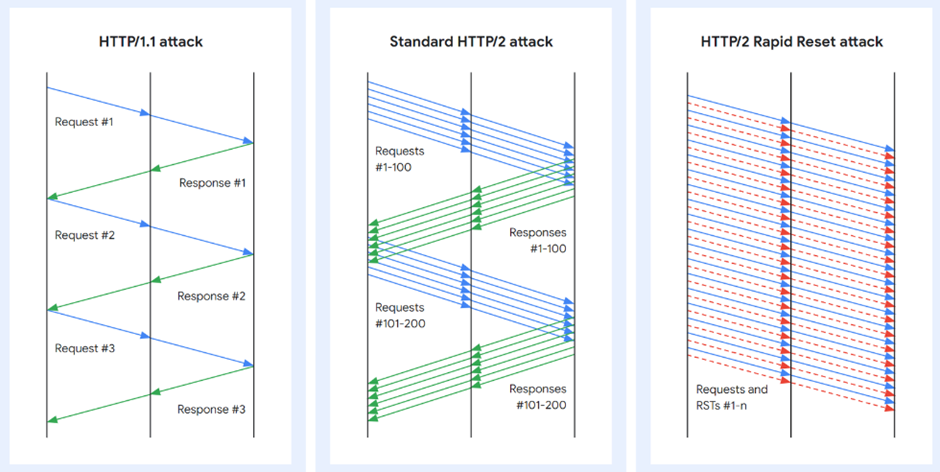
It is now popular as “Rapid Reset Attack” and the vulnerability allows a remote, unauthenticated attacker to cause an increase in CPU usage that can lead to a denial-of-service (DoS). It is also known to be exploited in the wild from August through October 2023 and multiple exploits are available in the public.
Severity: HIGH
CVSSv3.1: Base Score: 7.5 HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
CVSSv2: Base Score: 5 MEDIUM
Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:P
Exploit available in public: Yes.
Exploit complexity: Low
Active Exploitations
It is also known to be exploited in the wild from August through October 2023 and multiple exploits are available in the public.
In parallel, the CISA also issued an advisory regarding the vulnerability, incorporating it into their Known Exploited Vulnerabilities (KEV) list.
Prevention and Mitigation
- Apply vendor recommended patches/security updates.
- Disable the HTTP/2 protocol on your web server if vendor updates are not available.
- Restrict access to external/public to your web applications wherever possible.
- For .NET and Kestrel, servers without HTTP/2 enabled are not affected. Include a protocol setting for each Kestrel endpoint to limit your application to HTTP1.1
AppTrana WAAP Threat Coverage
AppTrana customers are protected from the vulnerabilities from Day 0.
Apart from the patches provided by the vendor, AppTrana WAAP offers additional protection patterns that can serve as an extra layer of defense against potential exploits.
References
- HTTP/2 protocol
- Google: How it works: The novel HTTP/2 ‘Rapid Reset’ DDoS attack
- AWS: CVE-2023-44487 - HTTP/2 Rapid Reset Attack
- NGINX: HTTP/2 Rapid Reset Attack Impacting NGINX Products
- Microsoft Response to Distributed Denial of Service (DDoS) Attacks against HTTP/2 CISA: Understanding and Responding to Distributed Denial-of-Service Attacks