Table of Contents
Indusface Product Newsletter- October 2022
 Updated
by Rama Sadhu
Updated
by Rama Sadhu
October 2022 Edition
Learn about the recent launches and updates to the product.
-----------------------------------------------------------------------------------------
AppTrana Updates
URI-based DDoS Protection
- The Next Level to Behavioral DDoS Protection - This policy provides an advanced level of protection to AppTrana users. You can now go beyond the formula-based protection, i.e., provide the specific URIs that you want to keep a check on.
- For critical and transactional pages such as: Login, Checkout, Sign-up, Pricing, etc, the URI-based policy is the best tool to safeguard your business.
- For more details, read our blog – URI-based DDoS Protection for AppTrana
Enhanced Bot Protection
We have added the following new modules to enhance bot protection:
- Allow Good Bots/ Block Good Bot Pretenders
- Tor IP
- User Agent Based Detection
- Suspicious Countries
- IP Reputation
- Data Center IP
- API Client IPs
- Anomaly Behavior Detection
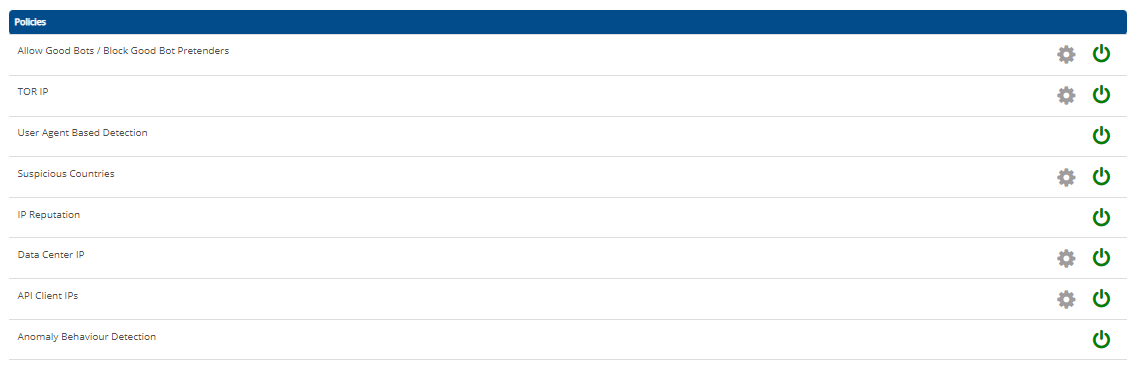
- Now, with all these modules adding their own risk score, for an identity (generally an IP), the risk score continuously gets adjusted and when it goes above a threshold, the identity will be blocked. AppTrana users get to adjust at what threshold the bots should be blocked by configuring their sensitivity to bots in the AppTrana portal.
- For more details, read our blog – Enhanced Bot Protection with AppTrana.
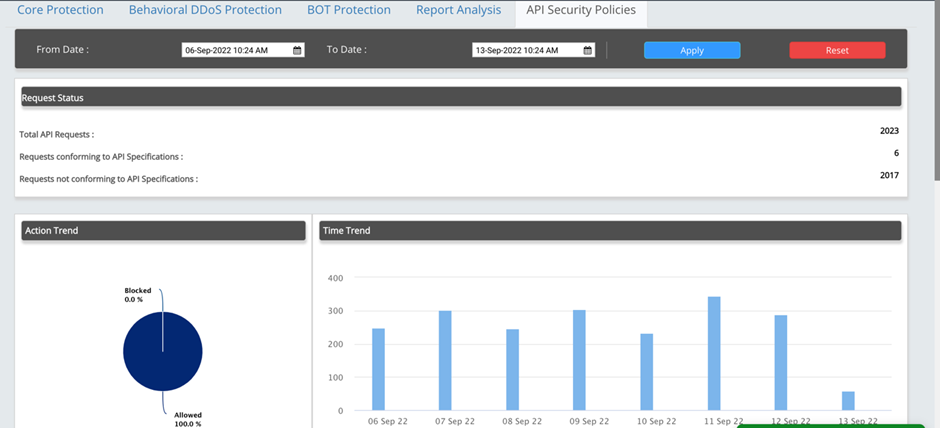
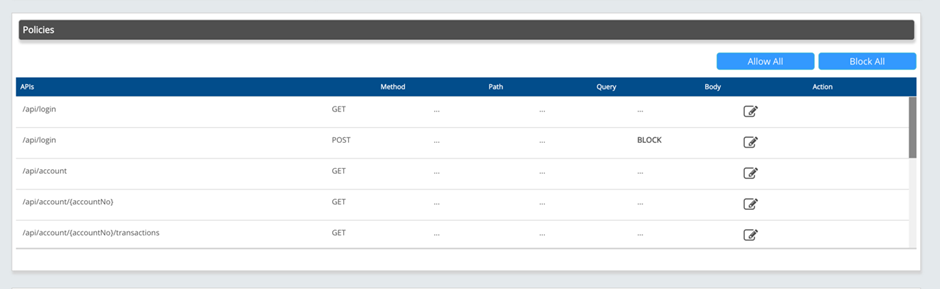
Comprehensive Risk-based API Security
- In line with our web application protection, we have added the risk-based approach to API Protection.
- With the combination of Risk detection, API Threat detection, API Positive Security policies, API-Specific DDoS policies, API-Specific Bot modules, and API Discovery, AppTrana’s API protection is the most comprehensive solution till date.
- For more details, read our blog – Industry’s 1st Comprehensive Risk-based API Security
Consolidated Daily Summary Email
AppTrana users can now opt to receive daily e-mails from AppTrana. This e-mail provides the current status of vulnerabilities, attacks blocked, types of attacks, and WAF status of all sites. Users can opt-in on the “My preferences” section under the ‘Manage’ section in the navigation bar.
Fix for Details in the Action Centre
We have released a fix that when blacklisted IPs are DDoS, the DDoS alert mail won’t be sent as it is already blocking the attack(s).
Automated Purge of CDN Through API
Developers can now purge CDN cache memory by calling an API to the AppTrana server. It’s a 3-step process to clear the CDN memory from all / specific URLs under a given website. Please find more details available in this doc.
Downloadable Executive Report
Users can now download the executive report in the portal.
Anomaly Detection in Bot Protection
- AppTrana's Bot Protection feature is one of the most enhanced security features that allows you to protect your web apps & APIs by correlating the risk scores from the modules - Allow Good Bots/ Block Good Bot Pretenders, Tor IP, User Agent Based Detection, Suspicious Countries, IP Reputation, and Data Center IP.
- Now, in this latest enhancement to Bot Protection, called Anomaly Behaviour Detection, the risk scores from both the core and custom rules are now correlated with the above risk scores. Thus, providing comprehensive risk-based Bot Protection to AppTrana users.
- Under Anomaly Behaviour Detection, TTL/ Block Duration is now 10 mins as the anomaly module triggers only on the escalation of attacks due to various vectors.
WAS Updates
Infinite API Scanner
With our latest update, identify vulnerabilities in your APIs using the most comprehensive API scanner backed by a zero false positive guarantee. It provides:
- Automated API Scanning
- Extending the API scanner capabilities with pluggable modules that pen testers and in-house security teams can write to automate security test cases
- 24x7 support and proof of concepts to eliminate any false positives from automated scanners
Improvements in Defacement Checks
- The user will be more accurately informed of the changes to their site. The new defacement check creates a baseline using the 7-days scan and from then onwards if there is any variance seen on the site, then, it will immediately be reported.
- The defacement baseline is created by looking into various data found on the page including DOM depth, external links, media tags, etc. Based on the degree of changes identified from the baseline, we report the defacement as a Low/ Medium/ High alert.
- The defacement check is tied to Malware scans and would be done following the Malware sequence.
Sig Dev Labs
The following signatures are added to the Scanner to identify the new vulnerabilities.
Basic Authentication Vulnerability – Improve coverage Plugin: 9271 HTTP Basic Authentication Enabled If the protocol is https but if basic auth is used & credentials are decodedable using bas64decode, then, its vulnerable. |
SQL Injection OOB Web applications that do not properly sanitize user input before passing it to a database system are vulnerable to SQL injection. This type of attack potentially allows a malicious user to recover and/or modify any data that the application has access to. |
Web Cache Poisoning Attack Vulnerability The string in attack vector "haikumsg" is common in multiple plugins so URLs containing the same strings are causing FP in some cases. |
HTTP Host Header Injection (Routing-based SSRF) OOB Routing-based SSRF relies on exploiting the intermediary components that are prevalent in many cloud-based architectures. This includes in-house load balancers and reverse proxies. Fundamentally, they receive requests and forward them to the appropriate back-end. If they are insecurely configured to forward requests based on an unvalidated Host header, they can be manipulated into misrouting requests to an arbitrary system of the attacker's choice. |
Server-side Template Injection OOB Server-side template injection vulnerability arises when an application uses user-controllable data added to the server side template which is then processed by the template engine. An attacker can abuse such functionality to inject template directives/code and execute arbitrary code in system in-turn compromising it. |
Server-Side Request Forgery (SSRF) – OOB Server-side request forgery (also known as SSRF) is a web security vulnerability that allows an attacker to induce the server-side application to make HTTP requests to an arbitrary domain of the attacker's choosing. An attacker can trick the web server that could probably be running behind a firewall to send requests to itself to identify services running on it, or can even send out-bond traffic to other servers. |
XSS and HTML Injection (API) Cross-site scripting (or XSS) is #2 on the 2010 OWASP Top Ten web security risks and it pops up nearly everywhere. XSS occurs when a user-manipulatable value is displayed on a web page without escaping it, allowing someone to inject Javascript or HTML into the page. |
Password Found in Response An attacker would be able to capture the password using weaknesses in session handling, broken access controls, and cross-site scripting vulnerability. It could lead an attacker to quickly compromise the entire application. |
Credential found in token The HTTP Authorization token has confidential data that assert some number of claims. For example, a server could generate a token that has the claim "logged in as admin" and provide that to a client. The client could then use that token to prove that they are logged-in as admin. An attacker can take over the account of the victim if authorization tokens are not configured properly. |
Link Injection OOB Link injection is a type of HTML/XSS Injection attack. The attack happens by inserting link tags into the page/site content which may be used further for phishing, redirection to malicious sites, credential stuffing, etc. |
Path-relative stylesheet import (PRSSI) It is a MIME type confusion vulnerability in web-page styles. It occurs if relative links of the form <link href='folder/styles.css' are used to refer to style files. If an attacker has the ability to add his own text to the content of a page that loads CSS styles using relative paths, he has the opportunity to inject his own CSS rules. |
iFrame Injection A common cross-site scripting attack that combines malicious JavaScript with an iframe that loads a legitimate page in an effort to steal data from an unsuspecting user. This attack is usually only successful when combined with social engineering. |
Possible Sensitive Directories One or more possibly sensitive directories were found. These resources are not directly linked from the website. This check looks for common sensitive resources like backup directories, database dumps, administration pages, temporary directories. Each one of these directories could help an attacker to learn more about his target. |
HTML Form Without CSRF Protection Cross-Site Request Forgery (CSRF/XSRF) is a vulnerability where an attacker tricks the victim into making a request that the victim did not make. So, the attacker abuses the trust a web application has with a victim's browser. Mostly the HTML forms submitted have CSRF tokens embedded in them while submitting the request. If a form is without this preventive measure enabled, then, it's very much prone to CSRF attacks and other dependent attacks. |
WAF Rule Updates
AppTrana now safeguards your applications against the following vulnerabilities and attacks.
Rule Title | Update |
Encoding Abuse Attacks Protection Policy | To check whether the entered strings/characters are in the standard format or as per the standard encoding technologies. It will block a malicious user from injecting encoded strings/characters if it is not in a standard encoding format. |
AngularJS Client-Side Template Injection Detected | This occurs when user-input is dynamically embedded on a page where AngularJS client-side templating is used. By using curly braces it's possible to inject AngularJS expressions in the AngularJS client-side template that is being used by the application. These expressions will be evaluated on the client-side by AngularJS and when combined with a sandbox escape, they allow an attacker to execute arbitrary JavaScript code. |
HTTP Request Smuggling Attack | This attack exploits the inconsistency in parsing non-RFC-compliant HTTP requests via two HTTP devices (generally a backend server and HTTP-enabled firewall or a front-end proxy). The HTTP request smuggling process is carried out by creating multiple, customized HTTP requests that make two target entities see two distinct series of requests. |
Confluence Server OGNL injection - CVE-2021-26084 | It is an Object-Graph Navigation Language (OGNL) injection vulnerability in the Atlassian Confluence Webwork implementation. An unauthenticated, remote attacker could exploit this flaw by sending a specially crafted request to vulnerable endpoints on the Confluence Server or Data Center instance. Successful exploitation would allow an attacker to execute arbitrary code. |
Catch_All_Replay_Requests_Policy | To catch and block all replay requests which are not blocked by any of the rules in config. |