AppTrana
Getting Started
Frequently Asked Questions
Product Details
API Scan Coverage for OWASP Top 10
Whitelist Vulnerabilities on the AppTrana WAAP
API Request to Purge CDN Data
Analysis page - Attack Trend Visualisation
Advanced Behavioral DDoS
BOT Protection
Asset Discovery
Customize Application Behavior with Bot Score
Restricted Admin User
Self Service Rules
Configuring Custom Error Page in AppTrana
Enabling SIEM Integration
API Discovery Feature
SwyftComply
Analysis page - Access Trend Visualization
Manage WAAP Email Alerts
Enable and Configure Single Sign-On
WAF Automated Bypass and Unbypass
False Positive Analysis Report on WAAP
Product User Guide
Indusface WAS
Getting Started
Product User Guide
Summary
Dashboard
Malware Monitoring[MM]
Application Audit[AA]
Vulnerability Assessment[VA]
Reports
Settings
Asset Monitoring
New Reporting Structure
Frequently Asked Questions
Feature Summary
AcuRisQ – Risk Management with Advanced Risk Scoring
WAS Consulting License
API Key Based - Scan Log Export
WAS Defacement Checks
SIEM Integration with Sumo Logic
Indusface WAS Scanned Vulnerabilities
Total Application Security
Onboarding Documents
Indusface Newsletter
Indusface Product Newsletter - October 2021
Indusface Product Newsletter- April 2021
Indusface Product Newsletter-January21
Indusface Product Newsletter - June 20
Indusface Product Newsletter - October 19
Indusface Product Newsletter - August 19
Product Newsletter of May 19
Product Newsletter of March 19
Product Newsletter of January 19
WAF Portal Revamp June 18
Product Newsletter of July 18
Product Newsletter of May 18
Product Newsletter of March 18
Product Newsletter of February 18
Product Newsletter of January 18
Indusface Product Newsletter - March 2022
Indusface Product Newsletter - February 2023
Indusface Product Newsletter- October 2022
Zero Day Vulnerability Reports
Vulnerabilities Detected in 2023
Vulnerability Report of May 23
Vulnerability Report of March 23
Vulnerability Report of August 23
Vulnerability Report of July 23
Vulnerability Report of April 23
Vulnerability Report of November 23
Vulnerability Report of June 23
Vulnerability Report of December 23
Vulnerability Report of February 23
Vulnerability Report of January 23
Vulnerability Report of September 23
Vulnerability Report of October 23
Vulnerabilities Detected in 2016
CRS vs. Zero Day Vulnerability - December 2016
CRS vs. Zero Day Vulnerability - November 2016
CRS vs. Zero Day Vulnerability - October 2016
CRS vs Zero Day Vulnerability - September 2016
CRS Vs Zero Day Vulnerabilities - August 2016
Vulnerabilities Detected in 2017
Vulnerability Report of April 17
Vulnerability report for Apr 3rd - Apr 9th 17
Vulnerability report for April 17th - Apr 23rd 17
Vulnerability report of April 10th - April 16th
Vulnerability Report of March 17
Vulnerability report for Mar 20th - Mar 26th
Vulnerability report for Mar 13th - Mar 19th
Vulnerability report for 27th Feb - 5th Mar
Vulnerability report for Mar 27th - Apr 2nd
Vulnerability report for Mar 6th - Mar 12th
Vulnerability Report of February 17
Vulnerability Report of January 17
Vulnerability Report of December 17
Vulnerability Report of November 17
Vulnerability Report of August 17
Vulnerability Report of September 17
Vulnerability Report of October 17
Vulnerability Report of July 17
Vulnerability Report of June 17
Vulnerability Report of May 17
Vulnerabilities Detected in 2018
Vulnerability Report of December 18
Vulnerability Report of November 18
Vulnerability Report of October 18
Vulnerability Report of September 18
Vulnerability Report of August 18
Vulnerability Report of July 18
Vulnerability Report of June 18
Vulnerability Reports of May 18
Vulnerability Report of April 18
Vulnerability Report of March 18
Vulnerability Report of February 18
Vulnerability Report of January 18
Vulnerabilities Detected in 2019
Vulnerability Report of December 19
Vulnerability Report of November 19
Vulnerability Report of October 19
Vulnerability Report of September 19
Vulnerability Report of August 19
Vulnerability Report of July 19
Vulnerability Report of June 19
Vulnerability Report of May 19
Vulnerability Report of April 19
Vulnerability Report of March 19
Vulnerability Report of February 19
Vulnerability Report of January 19
vulnerabilities Detected in 2020
Vulnerability Report of December 20
Vulnerability Report of November 20
Vulnerability Report of October 20
Vulnerability Report of Sep 20
Vulnerability Report of July 20
Vulnerability Report of June 20
Vulnerability Report of May 20
Vulnerability Report of April 20
Vulnerability Report of March 20
Vulnerability Report of February 20
Vulnerability Report of January 20
Vulnerabilities Detected in 2021
Vulnerability Report of November 21
Vulnerability Report of October 21
Vulnerability Report of September 21
Vulnerability Report of August 21
Vulnerability Report of July 21
Vulnerability Report of June 21
Vulnerability Report of May 21
Vulnerability Report of April 21
Vulnerability Report of March 21
Vulnerability Report of February 21
Vulnerability Report of January 21
Vulnerability Report of December 21
Vulnerabilities Detected in 2022
Vulnerability Report of January 22
Vulnerability Report of February 22
Vulnerability Report of March 22
Vulnerability Report of April 22
Vulnerability Report of May 22
Vulnerability Report of June 22
Vulnerability Report of July 22
Vulnerability Report of August 22
Vulnerability Report of September 22
Vulnerability Report of October 22
Vulnerability Report of November 22
Zero-Day Vulnerability Report - December 2022
Vulnerabilities Detected in 2024
Security Bulletin
Vulnerabilities 2024
Critical Apache OFBiz Zero-day AuthBiz (CVE-2023-49070 and CVE-2023-51467)
ScreenConnect Authentication Bypass (CVE-2024-1709 & CVE-2024-1708)
CVE-2024-1071 – Critical Vulnerability in Ultimate Member WordPress Plugin
Oracle WebLogic Server Deserialization
ApacheStructs_VG
Apache Struts 2 Vulnerability CVE-2023-50164 Exposed
Unpacking the Zimbra Cross-Site Scripting Vulnerability(CVE-2023-37580)
Adobe ColdFusion Vulnerabilities Exploited in the Wild
Remote Unauthenticated API Access Vulnerabilities in Ivanti
Multiple Moveit Transfer Vulnerabilities
HTTP/2 Rapid Reset Attack Vulnerability
Apache log4j RCE vulnerability
Table of Contents
- All Categories
- AppTrana
- Product Details
- Self Service Rules
Self Service Rules
 Updated
by Rama Sadhu
Updated
by Rama Sadhu
This feature helps the customers to create the custom rules in a self-service mode.
The following demo gives more details about self service rules:
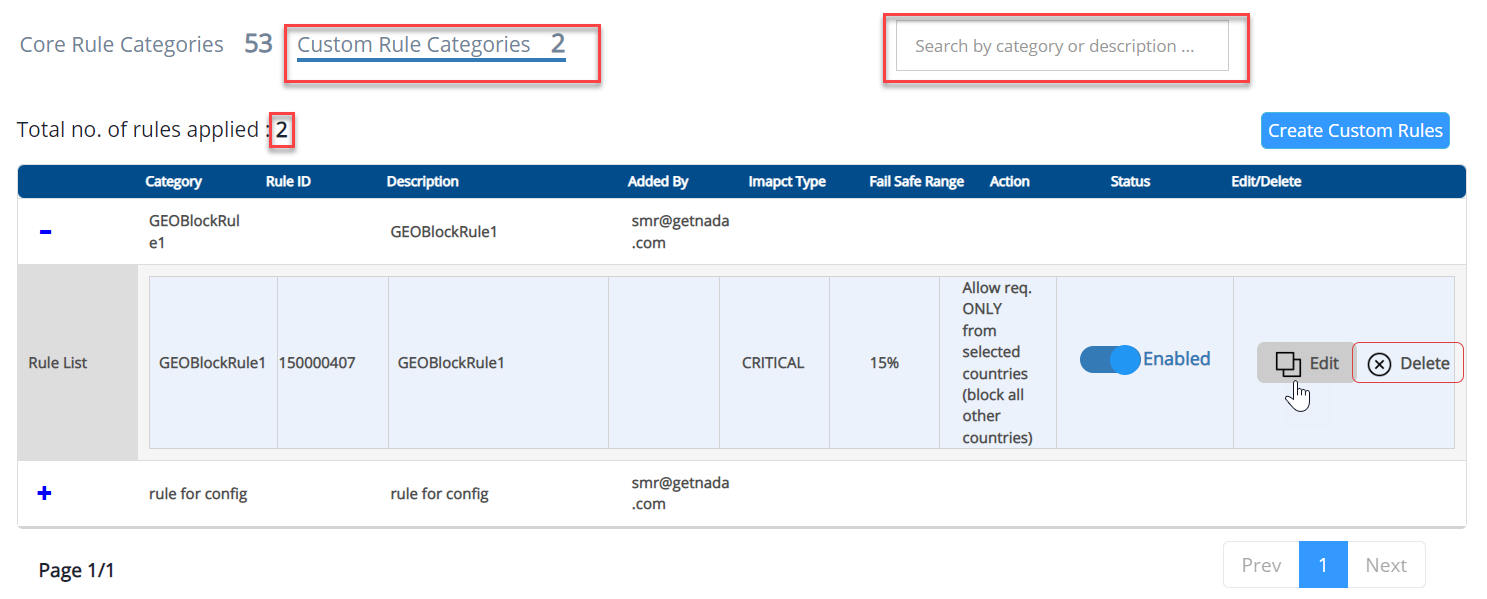
Custom Rule Categories
- Click on the Custom Rule Categories button.
- The total number of customer rules applied to the site is displayed.
- Use the search bar to find the specific rule.
Parameter | Description |
Category | The rule name is displayed here. |
Rule ID | Once the rule is created successfully, an ID will be assigned to the rule automatically. |
Description | The information about the rule which is entered by rule creator is displayed here. |
Added by | The rule creator's official mail address will be displayed here. |
Impact type | Rule impact such as Critical, High, Medium are displayed. |
Fail Safe Range | Fail safe range of the rule in percentage value is given here. |
Action | An action will be assigned by the rule creator, and the assigned action will be displayed. |
Status | A toggle button is given in this field and a user can enable or disable the rule |
Modify/Delete | Edit and Delete buttons are given to modify or edit the rules. |
Product Walkthrough
Create Custom Rules
Step 1: Rule Basic Details
This field consists of basic details of the rule.
- Enter the rule name and description in the respective fields.
- Enter a value in the fail safe range field.
- Add the applications in Rule Coverage field to apply the rule.
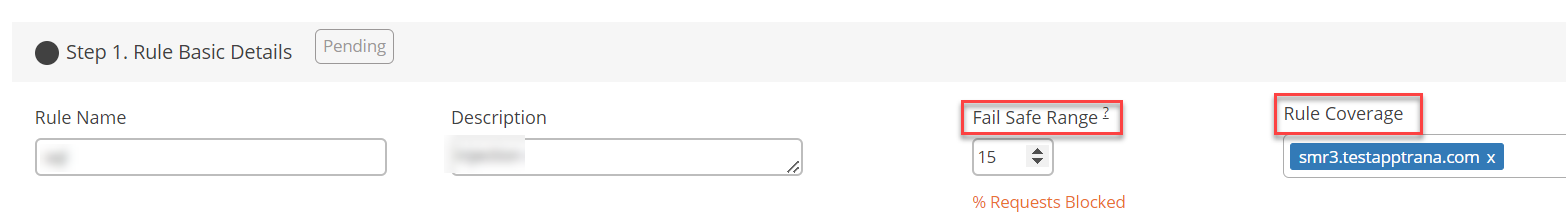
Fail safe range use case
- The number entered in the Fail Safe Range field is calculated by percentage.
- Consider a user enters “10” in the field, selects the triggered condition as Geo Block/Allow Criteria > Block request from selected countries, selected the list of countries need to be blocked.
- As per the above condition, failsafe move the rule to log only mode if the percentage of requests blocked by the rule is greater than 10% of all requests received by WAF/ Origin Server.
- A check box has also been given in the failsafe range field. The checkbox is to ensure that the rule is always ON, so it cannot go back to log only mode automatically.
- Once the checkbox is enabled, the user cannot enter the failsafe range value and it automatically shows 100.
Rule Trigger Condition
The section is equipped with three different criteria.
- Geo Block/Allow Criteria
- IP Block/ Allow Criteria
- Custom Rule
Geo Block/Allow Criteria
Based on this criterion, user can allow or block the request from the selected country/ countries.
There are two conditions given in this criterion.
C1: Block requests from selected countries
C2: Allow request ONLY from the selected countries (Block all other countries)
Select the respective condition based on the requirement and use the drop-down menu in the “Countries Selected” field to add the country/ countries and then click on the Create Button.
IP Block/ Allow Criteria
Based on this criterion, user can allow, block, or whitelist the selected IPs.
There are three conditions given in this criterion.
- Allow requests ONLY from the selected IP addresses (Block all others).
- Block all requests from selected IP addresses.
- Whitelist selected IP addresses.
Select the respective condition, enter the IP address, and then add the remarks.
“+Add IP” button is given to add multiple IP addresses.
Once the IPs successfully added, click on the Create button.
Custom Rule
Based on this criterion, user can create a rule for multiple parameters such as URI, USER AGENT, HTTP METOD, HTTP REFERRER, and ARGs.
For every parameter rule action is given and users can select the rule action accordingly.
For URIs:
For URIs multiple operators are given, that is URI starts with, does not start with, ends with, does not end with, contains, does not contain, equals, and does not equals.
In the request parameter field select URI and in operator field select the operator, and then enter the value in comparing value field.
For IPs:
Users can enter multiple IP addresses by comma separated format or by uploading a CSV file that contains all the list of IP addresses.
IP referrer consists of two operators, those are “Equal To and Does not Equal To”.
In comparing value field, users can enter multiple IPs by comma separated format or by uploading a CSV file.
Click on the “Add From File” to upload the CSV file.
Also, click “Download Sample File Format” to see the structure of entering IPs in the CSV file.
For User Agents:
For user agents four operators are given:
- Start With
- Does not Equal to
- Contain
- Does not Contain
In the request parameter field select USER AGENT and in operator field select the operator, and then enter the comparing value.
Users can enter multiple values by in Comparing value field using comma separated format.
Case Study:
A user enters two values in comparing value field such as chrome/116.0.0.0 safari 537.36 and chrome 117.0.0.0 safari/537.36, and the operator selected is Contains.
If any one of the values match with the user agent or both the values matches with multiple user agents, then the rule trigger condition will be activated.
For HTTP Referrer:
For HTTP Referrer multiple operators are given, that is URI starts with, does not start with, ends with, does not end with, contains, does not contain, equals, and does not equals to.
In the request parameter field select HTTP Referrer and in operator field select the operator, and then enter the comparing value.
For HTTP Method:
For HTTP Methods two operators are given, one is “Equals to” and second is “Does not Equals to.”
In the request parameter field select HTTP Method and in operator field select the operator, and then select the http method in comparing value field.
In this case, any HTTP request will be checked if the selected methods are used, if the methods are found, the rule action is triggered.
For ARGS:
For ARGS four operators are given, those are Starts with, Ends with, Contains, Equals to.
In the request parameter field select ARGS and in operator field select the operator, and then enter the value in comparing value field.
Rule Action
This section is available only for the Custom rule Criterion.
Also, the rule action list is the same for all the parameters except ARGS method.
Actions for rules with conditions URI, USER AGENT, HTTP METHODS, HTTP REFERRER:
- Whitelist Request and Log
- Skip Rule Category (Whitelist Rule) and Log
- Skip Rule and Log
- Log only
- Block Request and Log
Rule Action for rules with ARGS condition:
Select “Skip Rule for Selected ARG”
In the Whitelisted Rules field drop-down menu select the rules and then click on the Create button.
How to Change a Specific Rule to Log Only Mode?
- Enter the basic details of the rule in Step 1.
- Rule trigger condition in Step 2 is not required.
- From Step 3 Rule Action, select the rule “Move Rule to Log Only”.
- The rule Move Rule to Log Only set another rule to Log Only mode.
- Also, use Search Rule field to identify the target rule easily.
Default Rule
Default rules do not need any rule trigger condition.
Three different rule actions available such as:
- Skip Rule
- Skip Rule Category
- Move rule to log only