Table of Contents
Indusface Product Newsletter - June 20
Updated
by Author
June 2020 Edition
Learn about recent launches and updates to the product
WEB APPLICATION SCANNING
In last few months UX improvements were made to WAS portal to ensure important information is immediately available.
This includes providing total vulnerabilities found across all sites upfront in the portal.
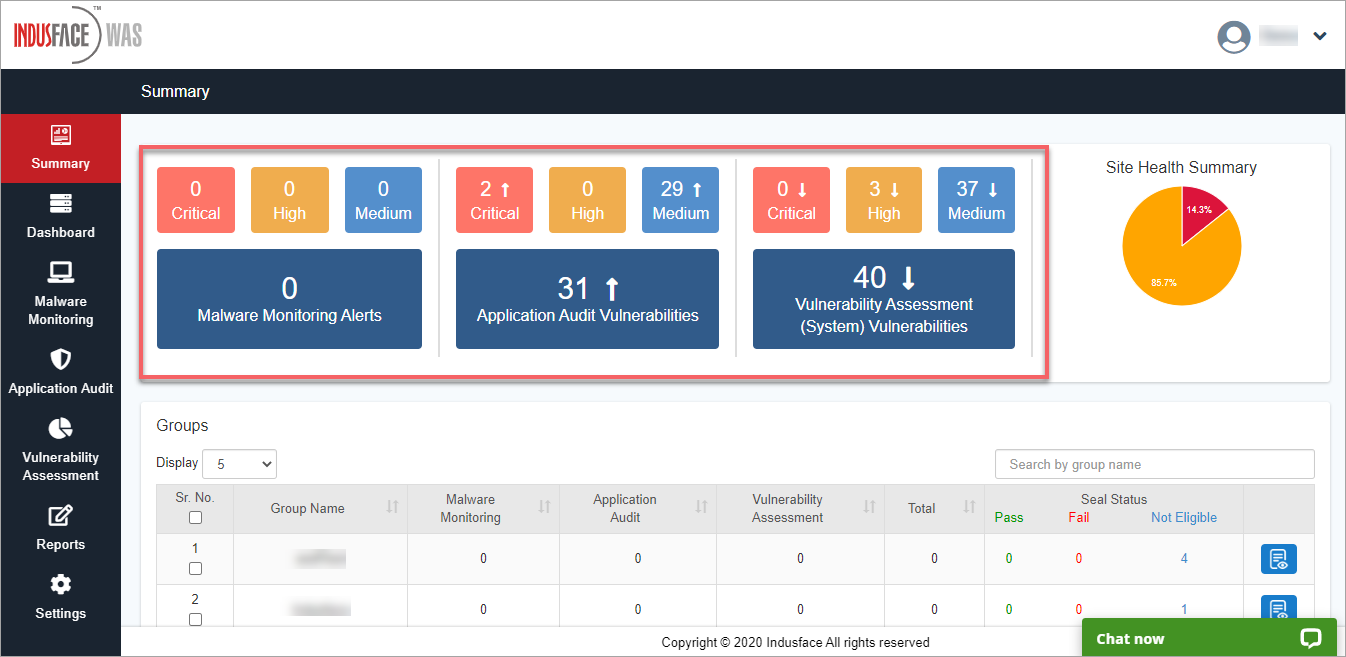
Ability to quickly scan a specific website(s) from the summary page.
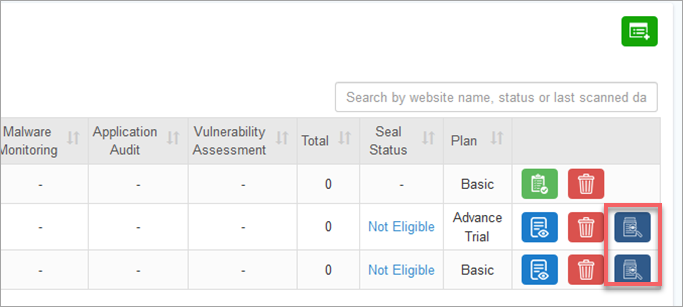
Information architecture of the Settings page is built to ensure important information is easily accessible.
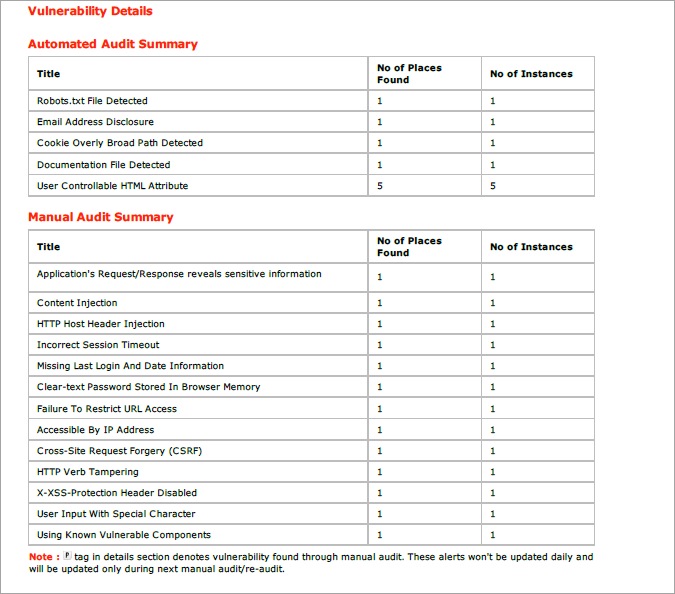
Separation of Manual Audit Summary:
Summary section in the reports were changed to provide separate summary for manual pen-testing findings and automated scanner findings.
To accommodate quick onboarding of sites to WAS portal and initiate scanning we have enabled self-onboarding. This is available to new customers who register from our website. In case existing customers need this functionality, please reach out to Indusface support.
With this customer will be able to onboard their site using Credit Card.
All you need to do is click Add Website icon on the right.
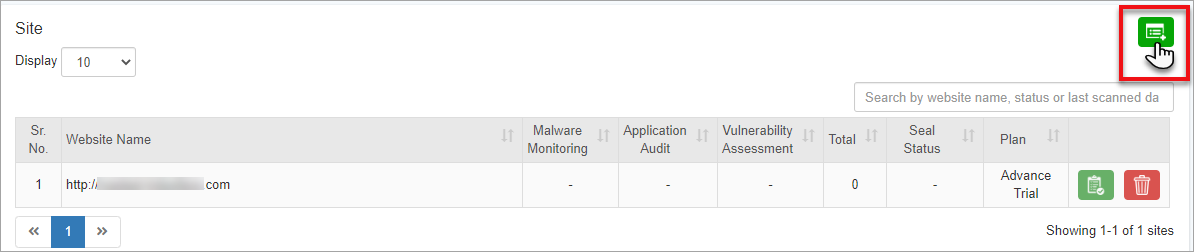
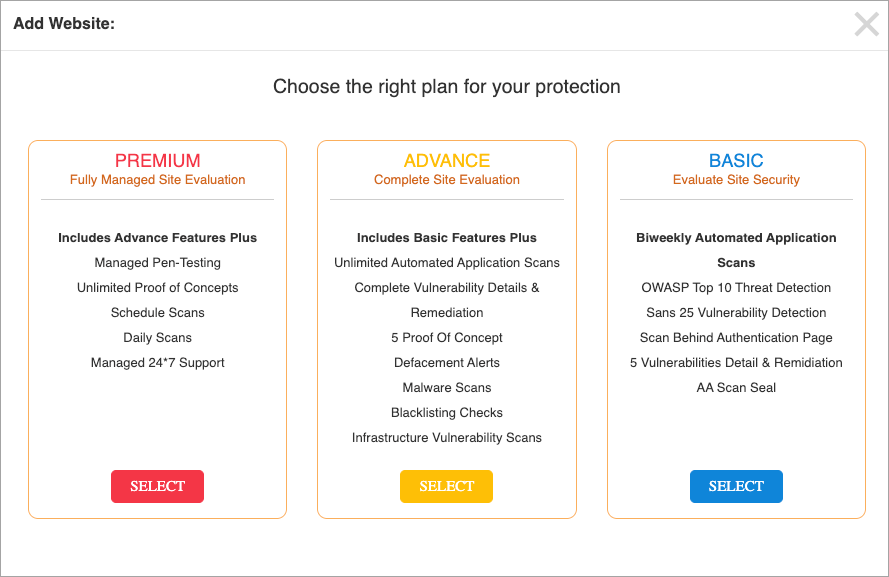
Select a specific plan as per your application security requirements.
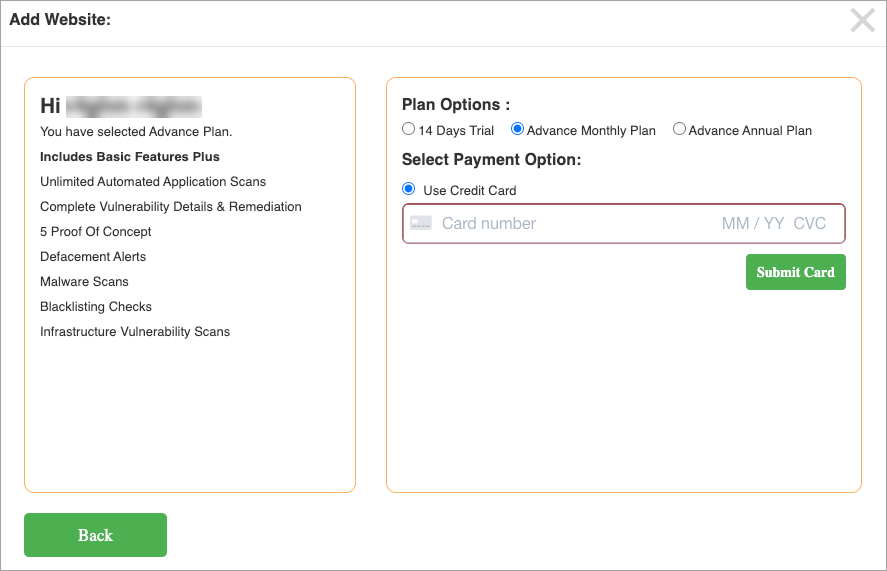
Provide the CC(Credit Card) details.
And then provide the domain customer wants to scan and validate the domain. That’s it, now onboarding can be done in few clicks.
Signature Updates
Following signatures were added to Scanner to improve detection coverage
Missing Account Lockout Policy Multiple unsuccessful login attempts with invalid passwords is suspicious behavior as it may be caused by brute force password guessing attacks which are intended to steal sensitive information, get access to administrative panels to perform unauthorized transactions or assisting to perform further attacks. To mitigate this issue, account lockout mechanisms are used, and such locked out accounts can only be unlocked after a predetermined period, via a self-service unlock mechanism, or intervention by an administrator. This check ensures if account lockout policy is enforced. | WAF/IPS Detected The site/server is protected by packet filtering systems like WAF (Web Application Firewall) or IPS (Intrusion Protection System). As they filter traffic and drop/redirect the connection, our scanner will not be successful in determining exploitable environment and hence will not be able to get comprehensive list of vulnerabilities exists in the current application. This check reports if any WAF/IPS is detected. | Insecure Cache-Control Header Detected Cache-Control header is used to control the behavior of browser caches and proxy caches based on multiple directives. With maxage directive enabled, the browser may cache the page, but it must re-validate with the server when its value is exceeded. Setting max-age to zero ensures that a page is never served from cache but is always re-validated against the server. Thus, reduces the performance of the server as it increases load. This check is to see If the cache control is set properly. | Old SSL/TLS Version Detected If the connection to site is made using old ssl/tls versions like SSLv3, TLSv1 & TLSv1.1 then connection is prone to vulnerabilities like BEAST, POODLE, etc. Usage of old ssl/tls version often results in information leakage and other attacks. | Old Cipher Suites Detected This is to check if SSL connection to the site is made using old ciphers and this are considered weak in the current time. These ciphers can be decoded to reveal the information and could lead to other potential attacks and vulnerabilities like SWEET32. | Apache Axis2 LFI Apache server Axis2 has LFI vulnerability which allows attacker to access arbitrary/sensitive files. By sending a crafted request using xsd parameter, attacker can obtain the file requested which contains sensitive information which is further used to perform other attacks. | Insecure/Deprecated Cryptography Detected This is to detect presence of a weak/depreciated hashing/crypto function in the site. These if sniffed can be easily decrypted to obtain sensitive information and in doing further attacks based on that. | Server Side Request Forgery Detected Server Side Request Forgery known as SSRF is vulnerability which allows an attacker to force servers into sending requests to arbitrary domains. Once exploited, attacker would have access to unauthorized actions and sensitive data which can be used for other attacks. | AWS Metadata Server Side Request Forgery SSRF vulnerability which allows an attacker to access aws metadata from the instances hosted upon by querying in the url. Once exploited attacker would have access sensitive information like secret key, tokens etc. | Server Side Request Forgery Local File Inclusion SSRF vulnerability which allows an attacker to perform local file inclusion by querying in the url. Once exploited attacker would have access to sensitive information like passwords, user groups, etc. | Server Side Request Forgery JSMOL2 LFI JSMOL2 SSRF vulnerability which allows an attacker to perform local file inclusion by attacking the url with specific payload. Once exploited attacker would have access sensitive information like database usernames, passwords, etc. | HTTP Verb Tampering: HTTP Verb Tampering vulnerability allows an attacker to bypass authorization by manipulating HTTP method in the request. Also, any arbitrary method can be tried for the same which may lead to other attacks once executed successfully. | Script Source Code Disclosure The vulnerability allows an attacker to read the source code of any script by injecting script filename as a parameter. Mostly script includes a file which name is determined via user-supplied input and this input is not validated at all in most cases before it is parsed to include function. | Long Password Denial of Service The vulnerability allows an attacker to send very long passwords via password input and in turn create denial of service attack. Because of long passwords sent the website will become unresponsive due to password hashing process which will exhaust CPU & memory utilization. | Uncontrolled Format String The vulnerability allows an attacker to read the stack trace or execute code or cause segmentation faults by attacking with format string like %f, %s which application/server uses externally. Attacker can read/access other memory spaces with such attacks. |
APPTRANA & TAS
On the AppTrana side, major changes continue in the direction of providing more stability and providing more enterprise friendly features to our customers.
Portal Updates
|
Naked Domain Support Domain name without any subdomains like www is called naked domain. For example, www.indusface.com is a subdomain whereas Indusface.com is a naked domain. The problem with naked domain is that CNAME (canonical name) cannot be added to naked domain as most DNS do not support this. So, this was a bottleneck to onboard naked domain sites on AppTrana. To solve this problem, we have worked with our CDN partners and have extended naked domain support in AppTrana through Anycast IP. So, if a customer onboards a naked domain site behind AppTrana, they will be provided an Anycast IP instead of CNAME removing the bottleneck around onboarding naked domain sites. |
Multi-port Support in SaaS AppTrana used to support only 2 ports. Generally one port for Http (80) and one port for Https (443). These ports could be changed according to application needs but there was no support to more than 2 ports for an application in AppTrana. With the advent of micro-architecture there was a growing demand to support applications having services running on multiple ports. To support this, updates have been made to our architecture to accomodate more than 2 ports. If a customer has more than 2 ports then needs to be supported in their application or need to open up ports other than 80 & 443. Please do reach out to Indusface support at support@indusface.com |
Analysis Page Analysis page is added to the AppTrana portal which will help customers analyse the protection status, requests coming into the sites and vulnerabilities found in the application in a more granular manner. Last 30 days data is available in the portal and analysis can be done for 7 days data at a time. 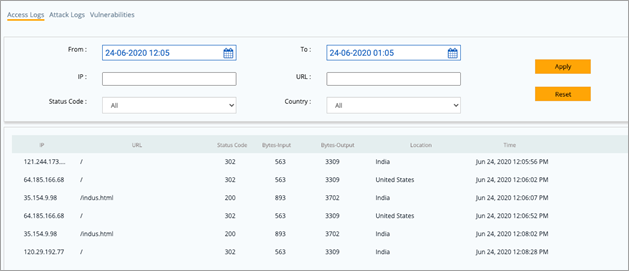 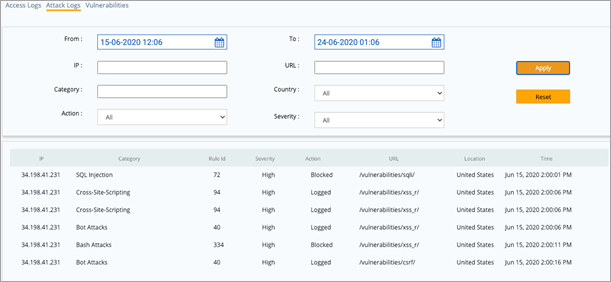 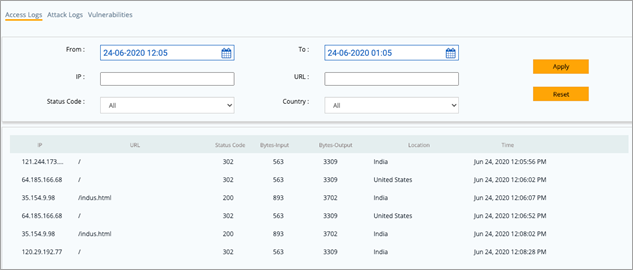 |
UX Improvements Over the past few months, lot of usability improvements have been updated to ensure users find traffic and attack related insights in real time. Important information is now provided upfront in the dashboard. 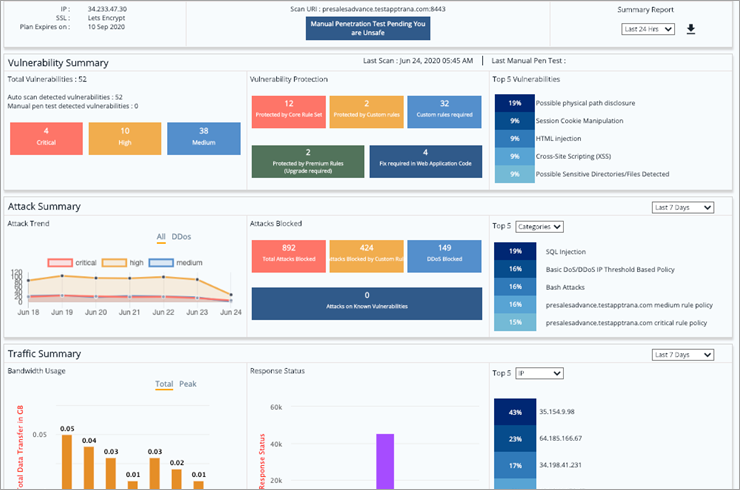 |
Rule Visibility As a part of managed services, we constantly update rules i.e., both core rules as well as custom rules that are applied to a specific application. One of the key requirements that multiple customers have requested in past is the visibility into rules applied on the application. To support this request, we have enabled this visibility in the portal. Customers can view it under Settings page-> WAF section. 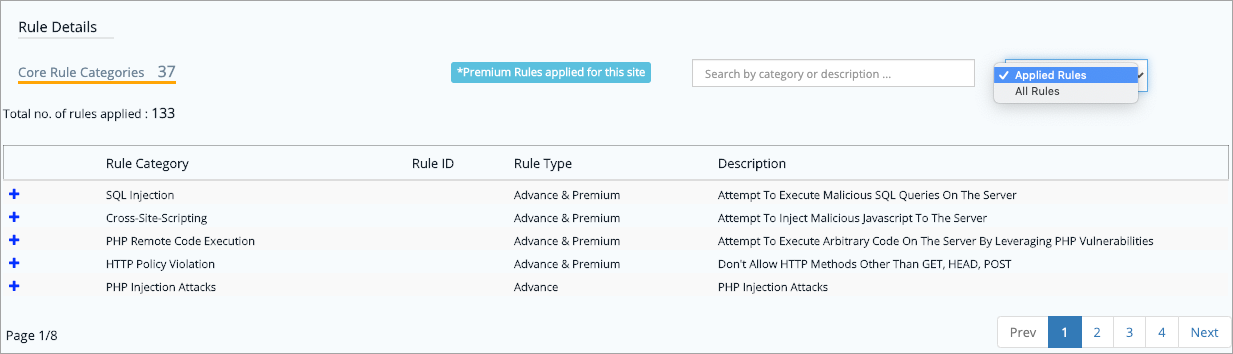 Customers can look for applied rules that are active in the application and also the set of all rules that are available. Information is updated in the Rule Details option as and when new rules are applied. |
WAF Version As we update our WAF constantly, customers have also requested us to provide the version that has been applied in the application. This is important more from compliance perspective as an ability to prove which version of WAF is applied for the site. To make this readily available we have added the version to the /indus.html page. One can get the version by checking <sitename>/indus.html. For example, if www.indusface.com is the site onboarded for protection then version can be got by www.indusface.com/indus.html. 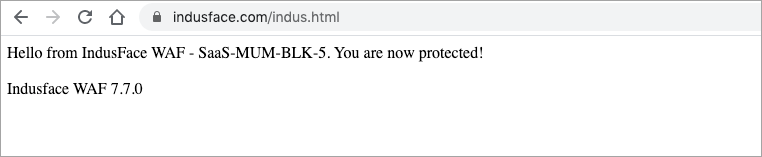 |
Rule Updates
Following Rules were added/updated to WAF to improve protection coverage
|
XML External Entity (XXE) Injection Policy These rules will have generic defence for XML External Entity (XXE) Injection. An XML input containing a reference to an external entity processed by a weakly configured XML parser can lead to disclosure of confidential data, denial of service, server-side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts. These rules intend to provide generic defence for exploiting XML External Entity (XXE) to retrieve known files like /etc/passwd/,/etc/hosts/, system.ini, win.ini, boot.ini , php.ini, web.config etc. |
Generic Deserialization Defence for Java, Microsoft Products & Ruby on Rails Insecure Deserialization is an attack where a manipulated object is injected into the context of the web application leading to logic manipulation or arbitrary code execution. These rules provide generic defence for exploiting Java/Microsoft/Ruby-on-Rails applications via an insecure deserialization leading to remote code execution via crafted http requests. |
Node.js-injection Attacks This Rule category detects and prevents attacks performed over Node.JS environment. It protects Node.JS based applications from Insecure unserialization/generic remote code execution vulnerabilities. |
Apache Struts and Java Attacks This rule category will detect and safeguard exploitation of Apache Struts vulnerabilities with CVE-IDs: CVE-2017-5638, CVE-2017-9791, CVE-2017-9805, CVE-2017-10271. This will detect and prevent arbitrary command execution due to vulnerable Apache struts environment. |
Remote File Inclusion Attacks A remote file inclusion (RFI) occurs when a file from a remote web server is inserted into a web page. These vulnerabilities exploited to display sensitive information from a remote web application. This rule category detects and protects RFI exploitation attempts |
PHP Injection Attacks An attacker may read any file accessible for the user that is running the web server (usually www-data). If the server has badly configured file permissions (very common), this attack can be escalated further. This category detects and protects against PHP Injection attempts. |
Path Traversal Attack A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. This category detects and protects against Path Traversal exploitation attempts |
HTTP Protocol Attack Prevention Malicious HTTP requests can be identified and blocked by inspecting HTTP requests comply to HTTP RFC standards or not. This category rules are meant to enforce RFC standards over HTTP requests like mandates Content-Length, Encoding etc., and prevents in case of RFC violation by blocking such requests. |
HTTP Protocol Enforcement HTTP protocol is vulnerable to various attacks exploited in multiple ways due to protocol violations. This category of rules is meant to identify and prevent from generic HTTP protocol violations attempts detected like HTTP request smuggling, Malformed byte encoding etc. |