AppTrana
Getting Started
Frequently Asked Questions
Product Details
API Scan Coverage for OWASP Top 10
Whitelist Vulnerabilities on the AppTrana WAAP
API Request to Purge CDN Data
Analysis page - Attack Trend Visualisation
Advanced Behavioral DDoS
BOT Protection
Asset Discovery
Customize Application Behavior with Bot Score
Restricted Admin User
Self Service Rules
Configuring Custom Error Page in AppTrana
Enabling SIEM Integration
API Discovery Feature
SwyftComply
Analysis page - Access Trend Visualization
Manage WAAP Email Alerts
Enable and Configure Single Sign-On
WAF Automated Bypass and Unbypass
False Positive Analysis Report on WAAP
Product User Guide
Indusface WAS
Getting Started
Product User Guide
Summary
Dashboard
Malware Monitoring[MM]
Application Audit[AA]
Vulnerability Assessment[VA]
Reports
Settings
Asset Monitoring
New Reporting Structure
Frequently Asked Questions
Feature Summary
AcuRisQ – Risk Management with Advanced Risk Scoring
WAS Consulting License
API Key Based - Scan Log Export
WAS Defacement Checks
SIEM Integration with Sumo Logic
Indusface WAS Scanned Vulnerabilities
Total Application Security
Onboarding Documents
Indusface Newsletter
Indusface Product Newsletter - October 2021
Indusface Product Newsletter- April 2021
Indusface Product Newsletter-January21
Indusface Product Newsletter - June 20
Indusface Product Newsletter - October 19
Indusface Product Newsletter - August 19
Product Newsletter of May 19
Product Newsletter of March 19
Product Newsletter of January 19
WAF Portal Revamp June 18
Product Newsletter of July 18
Product Newsletter of May 18
Product Newsletter of March 18
Product Newsletter of February 18
Product Newsletter of January 18
Indusface Product Newsletter - March 2022
Indusface Product Newsletter - February 2023
Indusface Product Newsletter- October 2022
Zero Day Vulnerability Reports
Vulnerabilities Detected in 2023
Vulnerability Report of May 23
Vulnerability Report of March 23
Vulnerability Report of August 23
Vulnerability Report of July 23
Vulnerability Report of April 23
Vulnerability Report of November 23
Vulnerability Report of June 23
Vulnerability Report of December 23
Vulnerability Report of February 23
Vulnerability Report of January 23
Vulnerability Report of September 23
Vulnerability Report of October 23
Vulnerabilities Detected in 2016
CRS vs. Zero Day Vulnerability - December 2016
CRS vs. Zero Day Vulnerability - November 2016
CRS vs. Zero Day Vulnerability - October 2016
CRS vs Zero Day Vulnerability - September 2016
CRS Vs Zero Day Vulnerabilities - August 2016
Vulnerabilities Detected in 2017
Vulnerability Report of April 17
Vulnerability report for Apr 3rd - Apr 9th 17
Vulnerability report for April 17th - Apr 23rd 17
Vulnerability report of April 10th - April 16th
Vulnerability Report of March 17
Vulnerability report for Mar 20th - Mar 26th
Vulnerability report for Mar 13th - Mar 19th
Vulnerability report for 27th Feb - 5th Mar
Vulnerability report for Mar 27th - Apr 2nd
Vulnerability report for Mar 6th - Mar 12th
Vulnerability Report of February 17
Vulnerability Report of January 17
Vulnerability Report of December 17
Vulnerability Report of November 17
Vulnerability Report of August 17
Vulnerability Report of September 17
Vulnerability Report of October 17
Vulnerability Report of July 17
Vulnerability Report of June 17
Vulnerability Report of May 17
Vulnerabilities Detected in 2018
Vulnerability Report of December 18
Vulnerability Report of November 18
Vulnerability Report of October 18
Vulnerability Report of September 18
Vulnerability Report of August 18
Vulnerability Report of July 18
Vulnerability Report of June 18
Vulnerability Reports of May 18
Vulnerability Report of April 18
Vulnerability Report of March 18
Vulnerability Report of February 18
Vulnerability Report of January 18
Vulnerabilities Detected in 2019
Vulnerability Report of December 19
Vulnerability Report of November 19
Vulnerability Report of October 19
Vulnerability Report of September 19
Vulnerability Report of August 19
Vulnerability Report of July 19
Vulnerability Report of June 19
Vulnerability Report of May 19
Vulnerability Report of April 19
Vulnerability Report of March 19
Vulnerability Report of February 19
Vulnerability Report of January 19
vulnerabilities Detected in 2020
Vulnerability Report of December 20
Vulnerability Report of November 20
Vulnerability Report of October 20
Vulnerability Report of Sep 20
Vulnerability Report of July 20
Vulnerability Report of June 20
Vulnerability Report of May 20
Vulnerability Report of April 20
Vulnerability Report of March 20
Vulnerability Report of February 20
Vulnerability Report of January 20
Vulnerabilities Detected in 2021
Vulnerability Report of November 21
Vulnerability Report of October 21
Vulnerability Report of September 21
Vulnerability Report of August 21
Vulnerability Report of July 21
Vulnerability Report of June 21
Vulnerability Report of May 21
Vulnerability Report of April 21
Vulnerability Report of March 21
Vulnerability Report of February 21
Vulnerability Report of January 21
Vulnerability Report of December 21
Vulnerabilities Detected in 2022
Vulnerability Report of January 22
Vulnerability Report of February 22
Vulnerability Report of March 22
Vulnerability Report of April 22
Vulnerability Report of May 22
Vulnerability Report of June 22
Vulnerability Report of July 22
Vulnerability Report of August 22
Vulnerability Report of September 22
Vulnerability Report of October 22
Vulnerability Report of November 22
Zero-Day Vulnerability Report - December 2022
Vulnerabilities Detected in 2024
Security Bulletin
Vulnerabilities 2024
Critical Apache OFBiz Zero-day AuthBiz (CVE-2023-49070 and CVE-2023-51467)
ScreenConnect Authentication Bypass (CVE-2024-1709 & CVE-2024-1708)
CVE-2024-1071 – Critical Vulnerability in Ultimate Member WordPress Plugin
Oracle WebLogic Server Deserialization
ApacheStructs_VG
Apache Struts 2 Vulnerability CVE-2023-50164 Exposed
Unpacking the Zimbra Cross-Site Scripting Vulnerability(CVE-2023-37580)
Adobe ColdFusion Vulnerabilities Exploited in the Wild
Remote Unauthenticated API Access Vulnerabilities in Ivanti
Multiple Moveit Transfer Vulnerabilities
HTTP/2 Rapid Reset Attack Vulnerability
Apache log4j RCE vulnerability
Table of Contents
- All Categories
- Indusface Newsletter
- Indusface Product Newsletter- April 2021
Indusface Product Newsletter- April 2021
Updated
by Author
Indusface has produced new features and changes in this quarter. These changes are informative and appealing.
Date: 08/04/2021
-----------------------------------------------------------------------------------------------------
AppTrana Updates
Export the data into CSV format
Now AppTrana customers can export data into the CSV format and conduct offline analysis. Download CSV option will help customers to analyze data for a specific time slice using various filters available, download and pass to internal team for further analysis.
AppTrana allows customers to set the period and export the selected data into a CSV file. This feature is available for Action details, Attack Logs, Access Logs, and Vulnerabilities.
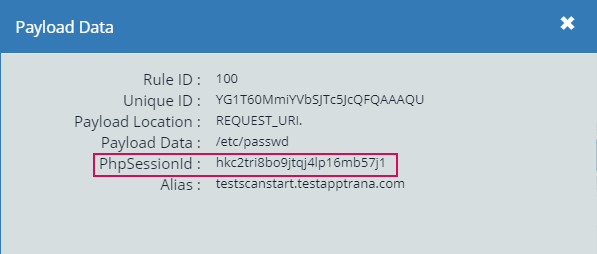
Attack payload parameters- PHP Session ID
Attack Payload Data enhanced with PHP Session ID variable. The PHP session Id variable helps to identify the exact requests that cause the attacks by checking the logs.
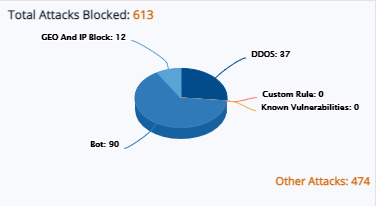
Attack details with Geo, IP, and BOT categories
Attack details categorized as Geo, IP, BOT categories, and other attacks. Blocked attacks count represented in a pie chart, which displays attacks blocked by GEO and IP blocking separately.
Grouping Websites
Group's feature simplifies the work process for customers with multiple websites. Websites typically have multiple characteristics and properties. Group's feature helps to club the websites that have the same properties and characteristics.
- Customers can check the progress of vulnerabilities found, bandwidth details, and attack details of their sites within the group.
How to Create a New Group?
Customers can create group in two ways.
1. Customers can create a new group through Overview tab.
2. Customers can create new group through the manage tab.
Add Websites to the Group
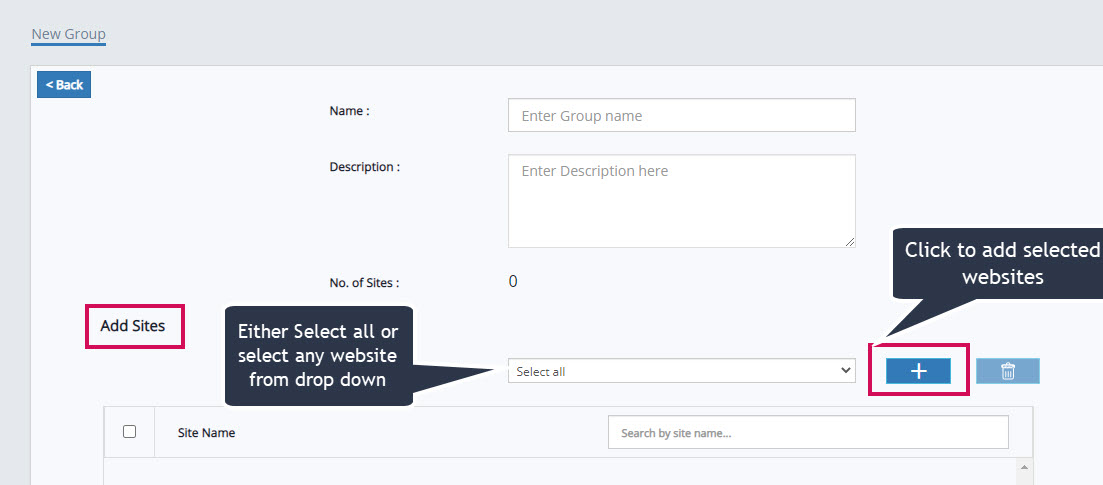
In which section Group data will be available?
Group level data will be available in the ‘Overview’ Tab.
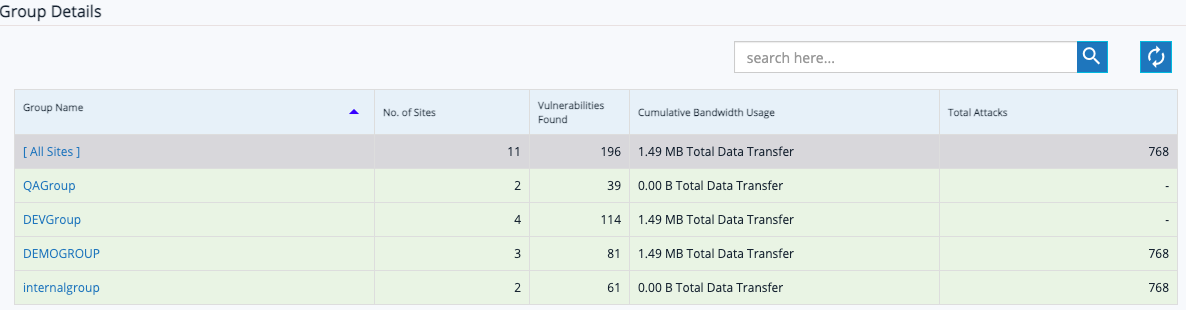
Access to the group
While adding a user to the account, admin can set access to the specific group for the user and the user will get access to all the sites associated with that group.
WAS Updates
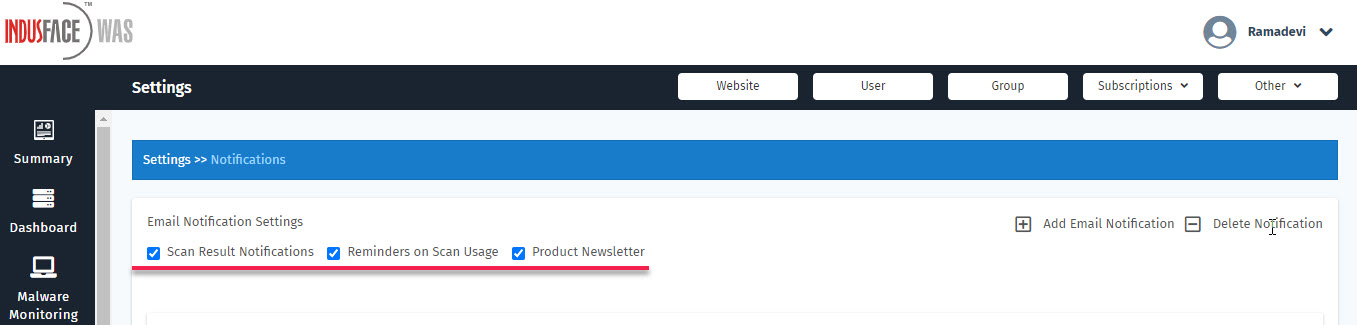
Email Alerts
Users can enable/disable email alerts that they want to receive. Below are some of the alerts that users can control.
Scan Result Notification
Users can enable/disable scan result emails. Scan Result emails are a great way to get quick snapshots when the scan is completed.
Reminders on Scan Usage
Scan reminders emails send to the customers if the site auto-scan has not been done for the last 30 days and manual pen-testing has not been done for the last 90 days.
Product Newsletter
Product Newsletter is a great way to get the latest information about new features, signatures, and plugins released by Indusface.
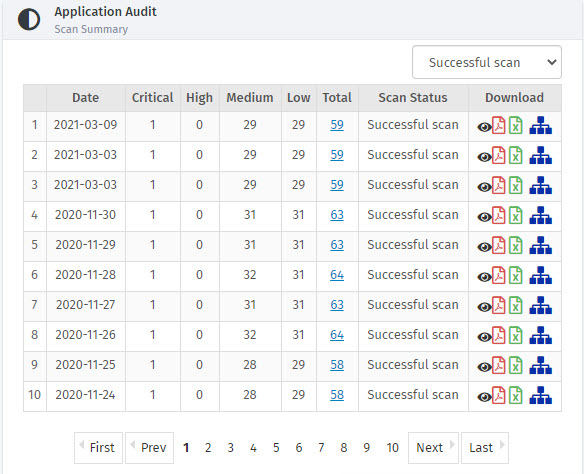
URI Sitemap
Application Audit scans have an additional report that is URI Sitemap. URI Sitemap shows a list of all the URIs that the scanner has scanned. URI Sitemap is available in the Application Audit tab.
Version Upgrade
Our web Application Scanner gets updates periodically to support the latest version of the application framework for which the scan is being performed. Our Scanner has been upgraded to support.
- Electron version - 11.3.0
- Node Version - 12.18.3
This will enable better detection as the ability of both the crawler and scanner is improved.
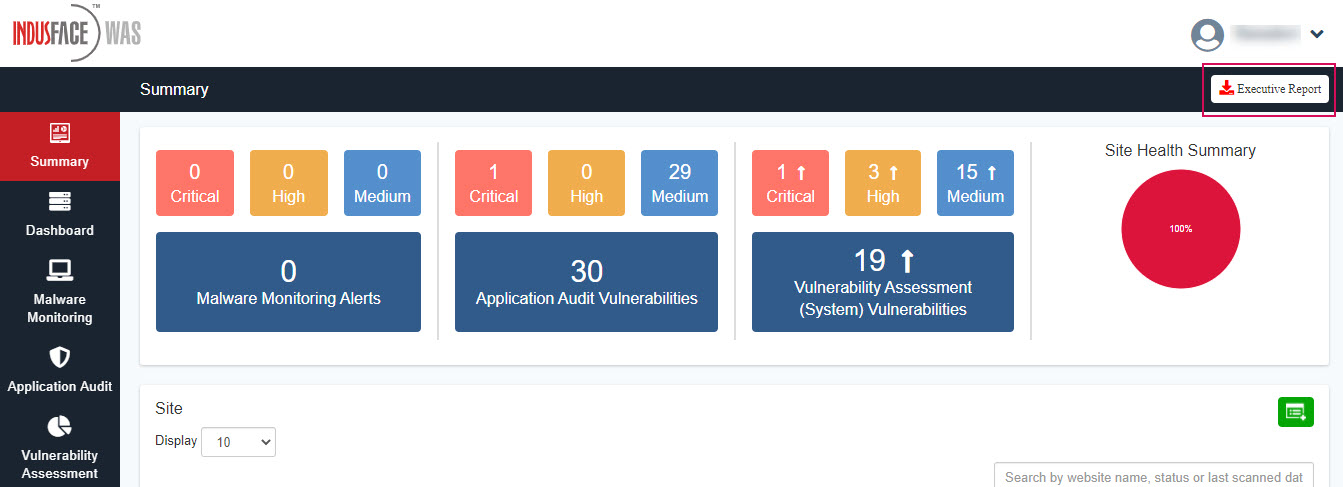
Executive Report
WAS Customers can download the Executive Report from the Summary page. Executive Report contains a summary of the WAS account for executives to understand security posture very quickly.
The report contains five sections 1. Usage Report 2. Action Center 3. Application Audit 4. Malware Monitoring 5. Vulnerability Assessment.
Sig Dev Labs
The following signatures are added to the Scanner to identify the new vulnerabilities.
Web Cache Poisoning Attack
Web Cache Poisoning is an attack against the integrity of the web cache repository. Users of the web cache repository will consume spoofed content instead of genuine ones. Combined with injection attacks such as XSS which leads to sensitive data exposure, cookie stealing, and session hijack.
Oracle WebLogic Server URI Attack
CVE-2020-14882, CVE-2020-14883 vulnerabilities allows unauthenticated attacker with network access via HTTP to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server. Supported versions that are affected are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0.
Microsoft Exchange Server RCE
Microsoft Exchange Server RCE is a SSRF flaw against exchange sever exploited as part of the initial attack chain leading to various post-authentication vulnerabilities. A successful exploit can lead to RCE, expose sensitive information, send spam campaigns, exfiltrate data and compromise the internal network. this plugin will provide coverage for CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065.
WAF Rule Updates
The following rules are added to the WAF to improve protection coverage.
HTTP Request Smuggling Attack
HTTP Request Smuggling Attack is identified and blocked with multiple Content-Length HTTP headers. This helps to protect the application from the malicious requests which pose as regular HTTP requests and gain access to the crucial resources.
Microsoft Exchange Server Remote Code Execution
Remote code execution attempt (CVE-2021-26855) in Microsoft Exchange Server can be exploited via sending arbitrary HTTP requests with configured headers. AppTrana now protects applications with this vulnerability of being exploited.