Table of Contents
Indusface Product Newsletter-January21
Updated
by Author
January 2021 Edition
Learn about recent launches and updates to the product.
------------------------------------------------------------------------------------------------------------
AppTrana Updates
Updates on Traffic Summary
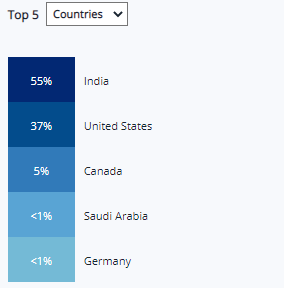
Traffic summary has been enhanced with top 5 country details. WAF Customers can see the top 5 countries from where their web application is being visited. This is in an addition to the top 5 URI and top 5 IP in the traffic summary table. Also, helps the customers to identify the most active regions.
Email Alerts:
Here is the list of email alerts introduced in AppTrana. To get any of the following email alerts, contact: support@indusface.com
SSL Certificate Expiry Alert Emails SSL Certificate expiry alert email will be sent to all associated users that is administrators, view only users, and website administrators. |
WAF status change Alert Emails When there is a change in WAF status for the web application, an alert email will be sent to the all users. |
WAF status change Alert Emails When there is a change in WAF status for the web application, an alert email will be sent to the all users. |
WAF Bypass Alert Emails Whenever WAF is Bypassed or Unbypass, an alert email will be sent to the all users. WAF Bypass is an automated process in AppTrana. If AppTrana finds any infrastructure issue, the website will be automatically bypassed to ensure the availability. |
Block Traffic from TOR IPs:
This feature helps customers to block the traffic coming from TOR IPs. To protect the web application from cyber attackers, customers can enable/disable the TOR IPs on AppTrana Settings page.
By default, TOR IPs are allowed to visit websites. Customers has to unselect Allow TOR IPS option to block the traffic.
Customize File Uploads:
AppTrana has introduced different file upload settings to our customers.
AppTrana customers can modify whether the end-user can upload the documents or media files on their websites or not. Also, customers can restrict the maximum file size allowed on their website.
Four options are available for customer to give access for different files on their website.
Those are:
Option | Action |
Block File Uploads | blocking upload of all files by unselecting Allow File Uploads |
Allow All Files | blocking upload of non-document files & non-media files |
Allow Documents | blocking upload of non-document files |
Allow Media Files | blocking upload of non-media files |
By default, All Files option is selected to allow both documents and media files, and maximum file size allowed is given as 25 MB. Customer can change the default value as per their requirements.
The maximum file size should be an integer value ranges from 1KB to 2GB.
WAS Updates
Download Option for Executive Dashboard Widget
Customers can download the executive format that is CSV format for Application Audit, Malware Monitoring, and Vulnerability Assessment.
Closure Reports
Closure Reports provides information about vulnerabilities closed between two scans. Closure reports play a crucial role in the audit functionality and also provides vulnerability close details between two dates or between two scans. Customers can access it from the Reports section.
Cancel Subscription
Subscribed customers who are onboarded using a credit card can cancel their subscription with a single click. On settings page, customers can see the list of the registered websites and their ongoing subscriptions. Also, customers can cancel any of the ongoing subscriptions. After cancellation, subscription continues till the end of the current cycle. Also, the website will move to basic plan if any free allotment exists or else it will deregister.
Request Manual PT
On WAS dashboard, customers can directly request manual pen testing. To use this feature, sign in to WAS Account. On WAS dashboard, go to Application Audit section and select the website that you want to do pen testing. Customers can see the number of pending manual pen testing requests.
Sig Dev Labs
Scanner Signatures
The following signatures are added in Scanner to identify new vulnerabilities.
Signature title | Functionality |
Denial of Service- Long Password | A flaw in the password hashing process of a web server could exhaust memory and CPU. This leads to the denial of service and the website becoming unresponsive. |
Uncontrolled Format String | The vulnerabilities allow an attacker to read the stack trace, execute code, or cause segmentation faults by attacking with format strings like %f, %s which application/server uses externally. Attacker can read/access the other memory spaces with such attacks. |
W3 Total Cache Debug Mode Found Enabled | W3 Total Cache is a Wordpress plugin for caching. Plugin’s debug mode enables the cache logging in source code, where the detailed information of cache is obtained. |
Possible Social Security Number Found | The website/page has one or more SSNs (social security numbers) disclosed. This is the possible disclosure found but SSN validity has to be verified manually. |
Chrome Logger Header Sensitive Information Disclosure | Chrome Logger Header Sensitive Information Disclosure is a Google Chrome extension to debug server side applications on chrome terminal. If this is enabled, the server side sends headers named X-ChromePhp-Data or X-ChromeLogger-Data. The value of these headers may contain sensitive information and must not present in production systems. |
JVM Version Disclosure | Due to the mis-configs done on the server/application the version of remote Java virtual machine (JVM) is disclosed in server header. |
Slowloris Attack | The slowloris attack relies on the server behaviour for receiving a complete request. Server waits for request and until it's complete. it will keep waiting and keep resources occupied. Attackers can use this to always keep resources busy and in turn making a DOS attack. |
Missing Sub Resource Integrity | Sub Resource Integrity (SRI) refers to security feature which helps browsers to ensure that 3rd party resources fetched either from a CDN or other source is not tampered with and integrity of resource is intact. This is verified by cryptographic hash value provided to that file when it fetched. |
XML External Entity DOS Attack | An XML External Entity (XXE) is a parameter parsed entity that can access local or remote content via a declared system identifier. The identifier is assumed to be a URI that can be accessed by the XML processor. An attacker can leverage the same features to endure heavy load on servers by expansion of entity and thus creating a DOS attack. |
HTTP Request Smuggling | HTTP Request Smuggling is a type of attack where specially crafted HTTP messages can be parsed and interpreted in different ways depending on the technology/agent that receives them. By leveraging this an attacker can bypass security controls, firewall checks, and so on. |
Link injection | Link injection is a type of HTML/XSS Injection attack. This attack happens by inserting a link tag in to page/site content which may be used further for phishing, redirection to malicious sites, credential stuffing, and so on. |
Iframe injection | Iframe injection is a type of HTML/XSS Injection attack. This attack happens by inserting iframe tags with ability to load third party links in to page/site content which may be used further for phishing, credential stuffing, and so on. |
WAF Rule Updates
The following rules are added in WAF to improve the protection coverage.
Rule Title | Update |
Improved Cross-site Scripting Attacks | Cross-site scripting attacks category has been improved to provide protection from various advanced cross-scripting attacks such as XSS JavaScript injection, Angular JS client-side injection, HTML injection, attribute injection, and modification of JavaScript global variable. |
DoS/DDoS IP Threshold Based Policy v2.0 | This category has improved upon the basic DoS/DDoS protection provided by Apptrana to protect web-application against advanced DDoS attack. |
Cookie Injection & Tampering Detection Policy | Web Application relies heavily on cookies to provide personalization to the users. These cookies stored in the user browser is used by the web applications. Attacker try to tamper with the cookies or generate cookies with are not belong to the current session or user in order to bypass security measures. This category detects and blocks any such attempt to tamper cookies or inject malicious cookies. |
Advanced SQL Injection Attacks | This rule protects web application from advanced SQL injection attacks like Postgres/MongoDB based SQLi Attempt, blind SQLi tests using sleep() or benchmark(), MySQL in-line comment and MSSQL DoS attempts. |
Revamped Bot attacks | Bot Attacks signature has been revamped as well as new bot signatures like crawler and scrapper signatures are added to continuously protect web application from the emerging bot attack. |