Table of Contents
Indusface Product Newsletter - October 2021
 Updated
by Rama Sadhu
Updated
by Rama Sadhu
Indusface has produced new features and changes in this quarter. These changes are informative and appealing.
Date: 28/10/2021
------------------------------------------------------------------------------------------------------
AppTrana Updates
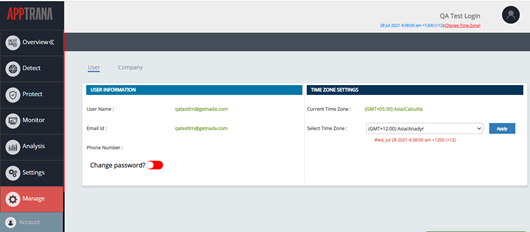
Time Zone
The much-awaited time zone feature is now available for AppTrana users. Now users can select their time zone and data will be reflecting the same. A user can also set a preferred time zone for his/her account.
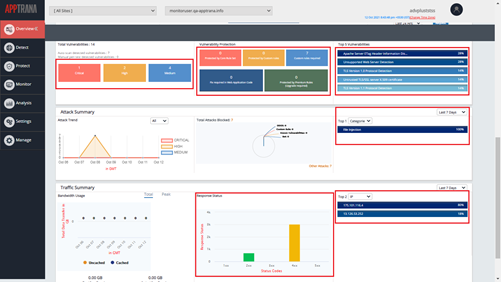
Clickable Charts
- The users will be able to click on charts like Vulnerability summary, Attack summary, or Traffic summary on the overview page, and will be redirected to the respective page with all the filters applied.
- This feature will be helpful to drill-down on the summary the user is viewing.
Behavioral DDoS
Behavioral DDoS Protection solution – One of the most advanced DDoS Protection solutions which allows organizations to protect their application by configuring policies at the Site level, IP level & Session level.
Salient Features:
- Behavioral DDoS will replace traditional rate-limiting rules within AppTrana.
- Behavioral DDoS provides one of the most comprehensive DDoS protection by allowing the user to configure policies at three-level Site level, IP level & Session level.
- The user will be able to understand historical traffic pattern and set the rules to be relative to the changing trends
- The user can configure rate limiting policies based on static values or % of historical data. For example, 120% above the max of last 7 days then block.
- The user can set the action to be performed when the Behavioral DDoS policy is triggered.
- A notification can be configured based on the trigger criteria.
- The policies' details are as follow:
-> Site Level Policy - Notification to users when the total number of requests for a site goes above the set value.
-> IP Level Policy - Block /Log/Notify when the number of requests per IP goes beyond the set value.
-> Session Level Policy - Block /Log/Notify when the number of requests per session goes beyond the set value.
- These policies will be enabled with default settings that will work for all sites. Customers can choose to customize it as needed.
- If customers have enabled any custom rules around the DDOS protection, those will not be affected by this role out.
Advance Plus Plan
An advance user can now enjoy Premium plan features with lower cost by upgrading to Advance Plus plan. The Advance Plus plan will have:
- 50 GB free monthly bandwidth
- 4 custom rules per site
- 5 POC per site
- Premium rules
WAS Updates
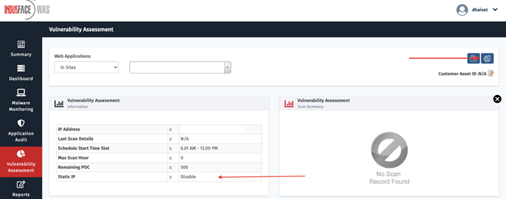
Static IP for Vulnerability Assessment Scan
For the applications which are registered for Application Audit, Vulnerability Assessment & Malware Monitoring - the user can now provide the static IP of the server for Vulnerability Assessment Scan. This feature will help indirectly scanning the server without passing through any intermediaries like WAF & CDN.
Sig Dev Labs
Scanner Signatures:
The following signatures are added to the Scanner to identify the new vulnerabilities.
- http.sys rce: A remote code execution vulnerability exists in the HTTP protocol stack (HTTP. sys) that is caused when HTTP. sys improperly parses specially crafted HTTP requests. Successful exploitation can allow a remote attacker to cause the blue screen of death, crash, restart server.
- Breach: BREACH is a variant of Compression Ratio Info-leak vulnerability against HTTP compression such as the use of gzip or deflate. A mitm attacker exploiting this flaw can bruteforce secret information from encrypted ssl/tls traffic such as csrf token, cookie, session id, anti-csrf token, etc. successful attack can lead to session hijack, sensitive information exposure, CSRF, XSS.
- GHOST Vulnerability: The identified vulnerability is a buffer overflow flaw in a Linux glibc library. The remote web server is detected with the version of php vulnerable to this flaw. Kindly update to the patched version and ignore if already done. An attacker can exploit this vulnerability to perform remote code execution, restart or crash the server, install a backdoor, etc.
- LFI in Apache mod-cgi: Local File Inclusion (LFI) vulnerability in the event mod-cgi enabled on Apache 2.4.49 allows remote attackers to access arbitrary/sensitive files which are normally inaccessible. By sending a crafted request, the attacker can obtain the file requested which contains sensitive information which is further used to perform other attacks.
- JWT Misconfiguration: JSON Web Token (JWT) is a standard for creating tokens that assert some number of claims. For example, a server could generate a token that has the claim "logged in as admin" and provide that to a client. The client could then use that token to prove that they are logged in as admin. An attacker can take over the account of the victim if authorization tokens are not configured properly.
- Incorrect Session Timeout (JWT): The Timeout property specifies the time-out period assigned to the Session object for the application, in minutes. If the user does not refresh or request a page within the time-out period, the session ends. It was observed that the application doesn't terminate the session automatically even if the user session is inactive for a prolonged period after login. An attacker can use the compromised/leaked token to perform unauthorized and unintended activities on behalf of the user pretending to be legitimate.
- User Controllable HTML Attribute: HTML attributes provide additional information about HTML elements and are generally in the form of name/value pair. There are many techniques that could use HTML attributes to submit HTML content. Using untrusted, user-controlled, or attacker-controlled input in such attributes of a sensitive HTML tag and successful submission can cause XSS or HTML injection vulnerabilities.
- Permissive Client Access Policy File Detected: Silverlight client access policy file (clientaccesspolicy.xml). It is used to provide the access to cross-domain to obtain any document on the server. So web clients easily understand that if cross-domain is accessible or not. It is located in the root directory. It could allow for cross-site request forgery or other attacks.
- Weak TLS CBC Cipher Detected: TLS connection to the site is made using old ciphers and this are considered weak in the current time. Server uses TLS 1.2 or TLS 1.1 or TLS 1.0 with CBC cipher, it could lead Zombie POODLE, GOLDENDOODLE, 0-Length OpenSSL and Sleeping POODLE vulnerabilities.
- Partial User Controllable Script Source: HTML attributes provide additional information about HTML elements and are generally in the form of name/value pair. Script src attribute specifies the URL of external JavaScript file. The attribute is user-controlled and exploiting it can cause XSS, Reverse Clickjacking attacks, and exposure to other security issues.
WAF Rule Updates
- MS Http.sys RCE vulnerability: A remote code execution vulnerability exists in the HTTP protocol stack (HTTP.sys) that is caused when HTTP.sys improperly parses specially crafted HTTP requests. An attacker who successfully exploited this vulnerability could execute arbitrary code in the context of the System account. Indusface WAF Rules have been updated to block MS Http.sys RCE attacks.
- Cross-Site-Scripting: Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it. Indusface rules have been updated to block cross-site-scripting attack.
