Table of Contents
- Tolerance Status
- Total Requests
- BOT Classification Trend
- Traffic Graph
- BOT Classification Table
- Top 20 URIs Accessed by Bots
- Top 20 User Agents
- Top 10 Country Data
- Policies
- Allow Good Bots/ Block Good Bot pretenders
- TOR IP
- User Agent Based Detection
- Suspicious Countries
- IP Reputation
- Data Center IP
- Anomaly Behavior Detection
- How Does Anomaly Behavior detection work?
BOT Protection
 Updated
by Rama Sadhu
Updated
by Rama Sadhu
- Tolerance Status
- Total Requests
- BOT Classification Trend
- Traffic Graph
- BOT Classification Table
- Top 20 URIs Accessed by Bots
- Top 20 User Agents
- Top 10 Country Data
- Policies
- Allow Good Bots/ Block Good Bot pretenders
- TOR IP
- User Agent Based Detection
- Suspicious Countries
- IP Reputation
- Data Center IP
- Anomaly Behavior Detection
- How Does Anomaly Behavior detection work?
This page gives insights into the total no. of BOT attacks, various protection methods, BOT trends, the correlation of the risk scores from various modules - Allow Good Bots/ Block Good Bot Pretenders, Tor IP, User Agent Based Detection, Suspicious Countries, IP Reputation, Data Center IP, and so on.
Tolerance Status
- The tolerance status is defined as the act of allowing bot attacks at a certain level.
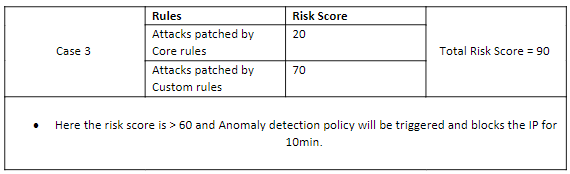
- When the risk score of a host IP against a website breaches its tolerance level, then the IP address of the website will automatically be blocked for 10minutes.
Parameter | Description |
High (relaxed) | High tolerance means the customer is willing to accept the bot attacks. Risk score is 80 |
Medium | Medim tolerance means the customer is accepting the bot attacks by any chance. Risk Score is 70 |
Low (paranoid) | Low tolerance means the customer is not compromising to accept bot attacks. Risk score is 60 |
Log Only | When the tolerance level is breached no attacks will be blocked but they will be logged. |
Log and Block | When the tolerance level is breached, it blocks further bot attacks, even the valid requests will be blocked till the TTL time is elapsed. |
- Click the drop-down to change the tolerance status and then click the Update button.
Total Requests
The Bot protection dashboard shows the number of Bot requests out of total requests along with their bandwidth usage for a selected time span.
Users can change the time span to Last 24 Hours, Last 7 Days, and Last 7 Days.
BOT Classification Trend
- The following trend displays the count of total bot attacks, attacks blocked, and allowed for each module.
- Users can change the time span to Last 24 Hours, Last 7 Days, and Last 7 Days.
Traffic Graph
The graph displays the comparison between the total traffic and the bot traffic for a selected time span.
BOT Classification Table
The following table helps users to gain a deeper understanding of the bot classification, the total bot requests received, and the total requests blocked and allowed.
Click Analyze to see the full bot details of a website.
Top 20 URIs Accessed by Bots
- The table provides a quick summary of the top 20 URI data accessed by BOTs with the respective count.
- Click Analyze tab to see the further details of URI data.
Top 20 User Agents
- Select UserAgents from the drop-down menu.
- User agents are softwares’ that retrieve web content for end users. The table provides the user agents data from which bot requests are received and their respective counts.
- Click Analyze to see further details of user agents used by bots.
Top 10 Country Data
- Select Countries from the drop-down.
- The number of bot attacks by the top 10 countries is displayed. Click Analyze to view further details.
Policies
The following tables consists of different policies which help users to configure based on the requirements.
|
- Bing -DuckDuckGo
The maximum risk score threshold for Good Bot Pretenders is 100. |
|
The maximum risk score threshold for TOR IPs is 30. |
|
|
|
|
|
|
|
|
|
Risk Score for Critical Severity– 10, Risk Score for High Severity – 5, Risk score for Medium Severity – 3
The maximum risk score threshold for anomaly detection is 100. Anomaly Behavior Detection policy is now only available for Premium and API plan customers. |
How Does Anomaly Behavior detection work?
Walk through the following example for a better understanding.
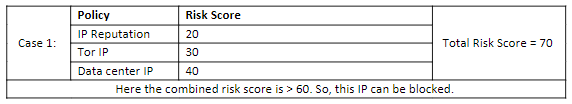
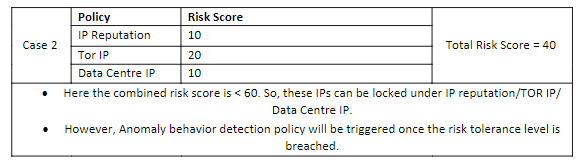
As per the tolerance level IP will be blocked only if the risk score is >60.