AppTrana
Getting Started
Frequently Asked Questions
Product Details
Browser Protection
API Scan Coverage for OWASP Top 10
Malware Scanning for File Uploads
Whitelist Vulnerabilities on the AppTrana WAAP
API Request to Purge CDN Data
Analysis page - Attack Trend Visualisation
Update Origin Server Address
Advanced Behavioral DDoS
BOT Protection
Asset Discovery
Customize Application Behavior with Bot Score
Restricted Admin User
OWASP API Security Top 10 2023 – AppTrana API Protection
Self Service Rules
ASN based IP Whitelisting
Enhance Your API Security with API Classification
SwyftComply for API Scan
Custom Bot Configuration
Configure Custom Error Pages in AppTrana
Configuring Custom Error Page in AppTrana
Enabling SIEM Integration
API Discovery Feature
SwyftComply
Analysis page - Access Trend Visualization
Manage WAAP Email Alerts
Configuring Custom Error and Maintenance Pages in AppTrana WAAP
Enable and Configure Single Sign-On
Origin Health Check Mechanism
WAF Automated Bypass and Unbypass
False Positive Analysis Report on WAAP
DNS Management
Product User Guide
Indusface WAS
Getting Started
Product User Guide
Summary
Dashboard
Malware Monitoring[MM]
Vulnerability Assessment[VA]
Application Audit[AA]
Reports
Settings
Asset Monitoring
New Reporting Structure
API Security Audit
Frequently Asked Questions
Feature Summary
AcuRisQ – Risk Management with Advanced Risk Scoring
Automated API Scanning
WAS Consulting License
API Key Based - Scan Log Export
WAS Defacement Checks
SIEM Integration with Sumo Logic
Indusface WAS Scanned Vulnerabilities
Indusface Newsletter
Indusface Product Newsletter - October 2021
Indusface Product Newsletter- April 2021
Indusface Product Newsletter-January21
Indusface Product Newsletter - June 20
Indusface Product Newsletter - October 19
Indusface Product Newsletter - August 19
Product Newsletter of May 19
Product Newsletter of March 19
Product Newsletter of January 19
WAF Portal Revamp June 18
Product Newsletter of July 18
Product Newsletter of May 18
Product Newsletter of March 18
Product Newsletter of February 18
Product Newsletter of January 18
Indusface Product Newsletter - March 2022
Indusface Product Newsletter - February 2023
Indusface Product Newsletter- October 2022
Zero Day Vulnerability Reports
Vulnerabilities Detected in 2016
CRS vs. Zero Day Vulnerability - December 2016
CRS vs. Zero Day Vulnerability - November 2016
CRS vs. Zero Day Vulnerability - October 2016
CRS vs Zero Day Vulnerability - September 2016
CRS Vs Zero Day Vulnerabilities - August 2016
Vulnerabilities Detected in 2017
Vulnerability Report of April 17
Vulnerability report for Apr 3rd - Apr 9th 17
Vulnerability report for April 17th - Apr 23rd 17
Vulnerability report of April 10th - April 16th
Vulnerability Report of March 17
Vulnerability report for Mar 20th - Mar 26th
Vulnerability report for Mar 13th - Mar 19th
Vulnerability report for 27th Feb - 5th Mar
Vulnerability report for Mar 27th - Apr 2nd
Vulnerability report for Mar 6th - Mar 12th
Vulnerability Report of February 17
Vulnerability Report of January 17
Vulnerability Report of December 17
Vulnerability Report of November 17
Vulnerability Report of August 17
Vulnerability Report of September 17
Vulnerability Report of October 17
Vulnerability Report of July 17
Vulnerability Report of June 17
Vulnerability Report of May 17
Vulnerabilities Detected in 2018
Vulnerability Report of December 18
Vulnerability Report of November 18
Vulnerability Report of October 18
Vulnerability Report of September 18
Vulnerability Report of August 18
Vulnerability Report of July 18
Vulnerability Report of June 18
Vulnerability Reports of May 18
Vulnerability Report of April 18
Vulnerability Report of March 18
Vulnerability Report of February 18
Vulnerability Report of January 18
Vulnerabilities Detected in 2019
Vulnerability Report of December 19
Vulnerability Report of November 19
Vulnerability Report of October 19
Vulnerability Report of September 19
Vulnerability Report of August 19
Vulnerability Report of July 19
Vulnerability Report of June 19
Vulnerability Report of May 19
Vulnerability Report of April 19
Vulnerability Report of March 19
Vulnerability Report of February 19
Vulnerability Report of January 19
vulnerabilities Detected in 2020
Vulnerability Report of December 20
Vulnerability Report of November 20
Vulnerability Report of October 20
Vulnerability Report of Sep 20
Vulnerability Report of July 20
Vulnerability Report of June 20
Vulnerability Report of May 20
Vulnerability Report of April 20
Vulnerability Report of March 20
Vulnerability Report of February 20
Vulnerability Report of January 20
Vulnerabilities Detected in 2021
Vulnerability Report of November 21
Vulnerability Report of October 21
Vulnerability Report of September 21
Vulnerability Report of August 21
Vulnerability Report of July 21
Vulnerability Report of June 21
Vulnerability Report of May 21
Vulnerability Report of April 21
Vulnerability Report of March 21
Vulnerability Report of February 21
Vulnerability Report of January 21
Vulnerability Report of December 21
Vulnerabilities Detected in 2022
Vulnerability Report of January 22
Vulnerability Report of February 22
Vulnerability Report of March 22
Vulnerability Report of April 22
Vulnerability Report of May 22
Vulnerability Report of June 22
Vulnerability Report of July 22
Vulnerability Report of August 22
Vulnerability Report of September 22
Vulnerability Report of October 22
Vulnerability Report of November 22
Zero-Day Vulnerability Report - December 2022
Vulnerabilities Detected in 2023
Vulnerability Report of May 23
Vulnerability Report of March 23
Vulnerability Report of August 23
Vulnerability Report of July 23
Vulnerability Report of April 23
Vulnerability Report of November 23
Vulnerability Report of June 23
Vulnerability Report of December 23
Vulnerability Report of February 23
Vulnerability Report of January 23
Vulnerability Report of September 23
Vulnerability Report of October 23
Vulnerabilities Detected in 2024
Vulnerability Report of October 2024
Vulnerability Report of April 2024
Vulnerability Report of July 2024
Vulnerability Report of May 2024
Vulnerability Report of September 2024
Vulnerability Report of February 2024
Vulnerability Report of December 2024
Vulnerability Report of January 2024
Vulnerability Report of June 2024
Vulnerability Report of March 2024
Vulnerability Report of November 2024
Vulnerability Report of August 2024
Security Bulletin
Vulnerabilities 2024
Hotjar's OAuth+XSS Flaw Exposes Millions at Risk of Account Takeover
Critical Apache OFBiz Zero-day AuthBiz (CVE-2023-49070 and CVE-2023-51467)
CVE-2024-4879 & CVE-2024-5217 Exposed - The Risks of RCE in ServiceNow
ScreenConnect Authentication Bypass (CVE-2024-1709 & CVE-2024-1708)
CVE-2024-4577 – A PHP CGI Argument Injection Vulnerability in Windows Servers
CVE-2024-8517 – Unauthenticated Remote Code Execution in SPIP
CVE-2024-1071 – Critical Vulnerability in Ultimate Member WordPress Plugin
Cryptocurrency Mining Attack Exploiting PHP Vulnerabilities: An Emerging Threat
Oracle WebLogic Server Deserialization
ApacheStructs_VG
Apache Struts 2 Vulnerability CVE-2023-50164 Exposed
Unpacking the Zimbra Cross-Site Scripting Vulnerability(CVE-2023-37580)
Adobe ColdFusion Vulnerabilities Exploited in the Wild
Remote Unauthenticated API Access Vulnerabilities in Ivanti
Multiple Moveit Transfer Vulnerabilities
HTTP/2 Rapid Reset Attack Vulnerability
CVE-2024-9264 - Grafana’s SQL Expressions Vulnerability
CVE-2024-8190 – OS Command Injection in Ivanti CSA
Apache log4j RCE vulnerability
- All Categories
- Indusface Newsletter
- Indusface Product Newsletter - March 2022
Indusface Product Newsletter - March 2022
 Updated
by Rama Sadhu
Updated
by Rama Sadhu
March 2022 Edition
Learn about the recent launches and updates to the product.
------------------------------------------------------------------------------------------
AppTrana Updates
Automatic Scan Scheduling
- We have added the Scan schedule option to the Detect page. The scan will be automatically started at the scheduled time.
- The user can cancel the scheduled scan before the scan gets started.
- The stop option is provided for the running scan.
- The last 5 scan details will be available, and the user can select any scan detail from the dropdown to view the details.
- Rule visibility option will be enabled for All Users for newly registered customers.
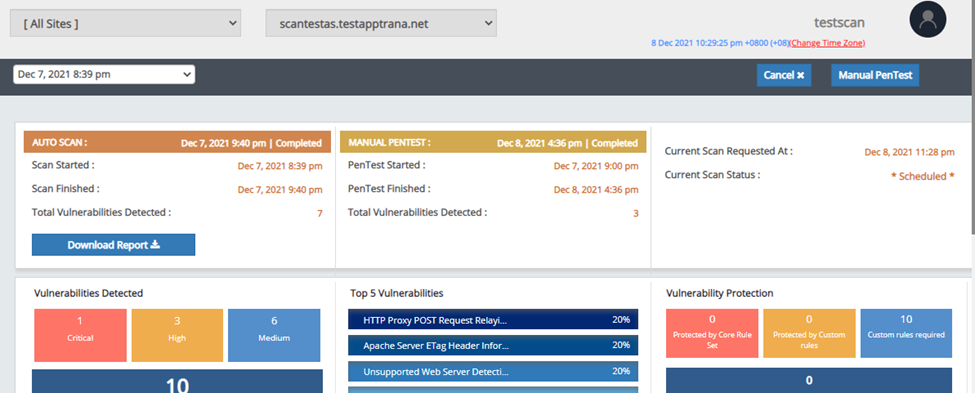
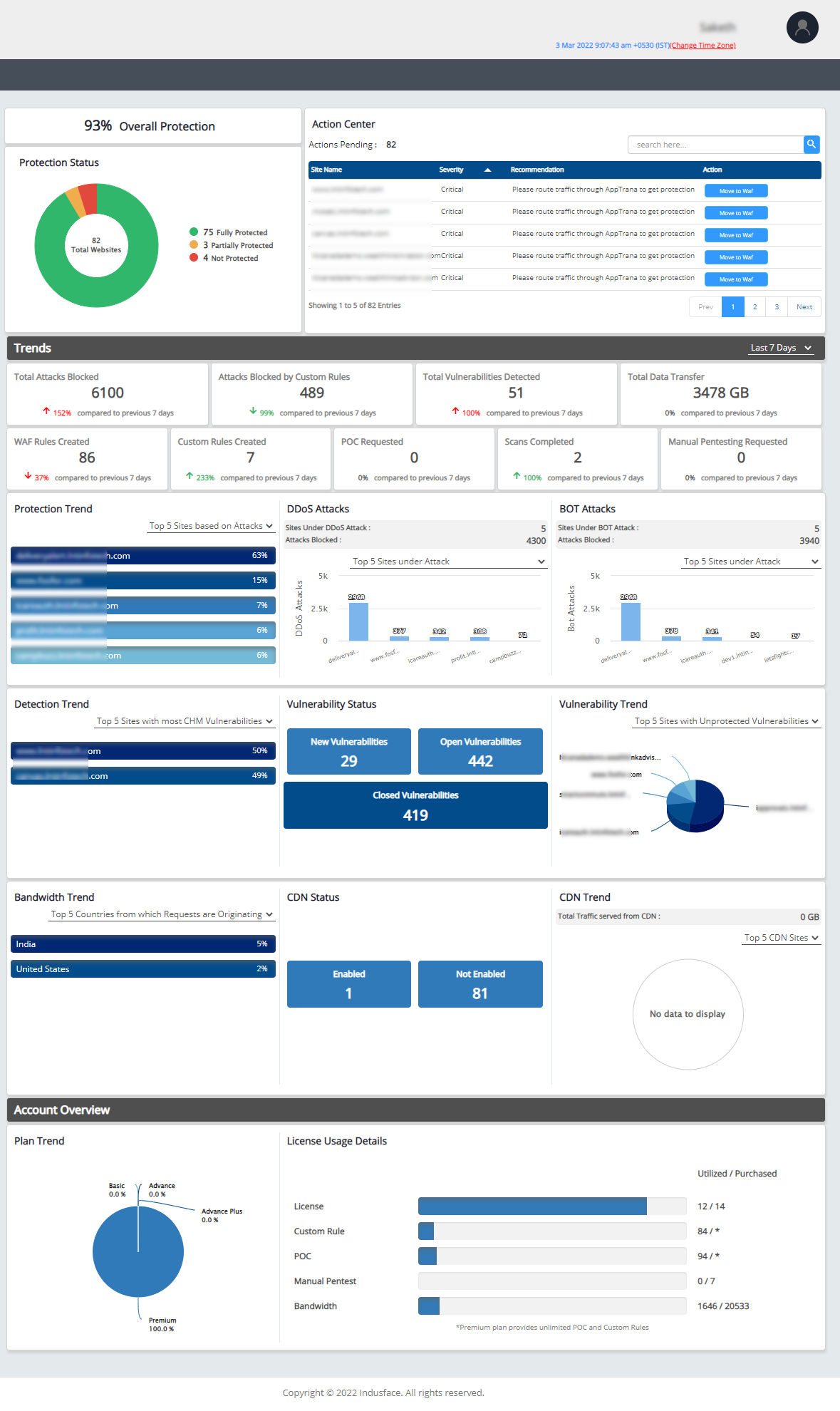
Executive Dashboard
- It provides executives with an easy-to-use dashboard that gives the summary of the account while providing all the necessary information to make decisions.
- Note - All the data in the executive dashboard will be shown for active sites in the account.
- Please find the dashboard’s screenshot below with dummy data -
Sig Dev Labs
The following signatures are added to the Scanner to identify the new vulnerabilities.
- SQL Injection - SQL injection is a code injection technique used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution
- Apache Range DoS (Denial of Service) – The byte range filter in the Apache HTTP Server 2.0.x through 2.0.64, and 2.2.x through 2.2.19 allows remote attackers to cause a denial of service (memory and CPU consumption) via a Range header that expresses multiple overlapping ranges, exploit called "Apache Killer".
- XSS and HTML Injection - HTML injection is a type of injection vulnerability that occurs when a user is able to control an input point and is able to inject arbitrary HTML code into a vulnerable web page. This vulnerability can have many consequences, like disclosure of a user’s session cookies that could be used to impersonate the victim, or, more generally, it can allow the attacker to modify the page content seen by the victims.
- HTML Form Without CSRF (Cross-Site Request Forgery) Protection - An attacker may force the users of a web application to execute actions of the attacker's choosing. A successful CSRF exploit can compromise end user data and operation in case of normal user. If the targeted end user is the administrator account, this can compromise the entire web application.
- Apache Server ETag Header Information Disclosure vulnerability - ETag header providing sensitive information that could aid an attacker, such as the inode number of requested files.
WAF Rule Updates
- Apache Http Server Path Traversal Vulnerability
- A new rule has been written to prevent path traversal attack.
- The Apache Http Server Path Traversal Vulnerability is a vulnerability that has been discovered in Apache HTTP Server, which could allow for a path traversal attack. Apache HTTP Server is an open-source, cross-platform web server for Unix and Windows. Successful exploitation allows threat actors to map URLs to files outside the expected document root by launching a path traversal attack and would give a remote attacker access to arbitrary files outside of the document root on the vulnerable web server. Additionally, exploits of this flaw may lead to the leaking of the source of interpreted files such as CGI scripts.
- Systems Affected:
-Apache HTTP Server 2.4.49
-Apache HTTP Server 2.4.50
- Microsoft Exchange .NET Deserialization RCE Vulnerability
- From the advisory of Microsoft, it stated that this CVE-2021-42321 is a post-auth RCE vulnerability
- Exchange that affects on-premises servers running Microsoft Exchange 2016 and 2019, including those using Exchange Hybrid mode.
- This exploit enables authenticated threat actors to execute code remotely on vulnerable servers and launch an attack.
- Apache Log4j RCE Vulnerability CVE-2021-44228
- Log4j 2 is a logging library used in many Java applications and services. The library is part of the Apache Software Foundation’s Apache Logging Services project. A remote code execution vulnerability exists in Apache Log4j2 <=2.14.1 JNDI features where configuration, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI-related endpoints.
- An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when the message lookup substitution is enabled. This vulnerability is also known as “Log4Shell”.
