Indusface Product Newsletter - October 19
Updated
by Author
October 2019 Edition
Learn about recent launches and updates to the product
WEB APPLICATION SCANNING
Based on the feedback received from multiple customers, we have come up with a new format for the reports. Currently we show each instance of the vulnerability in our report and dashboard without grouping. This becomes cumbersome for customers as they are not able to track what the vulnerabilities are at each URI level, places and how many variances are there clearly. It is to address this that we have come up with a new reporting structure, which groups the vulnerabilities based on where they are found and how customer would fix them. For further details click here.
Signature Updates
Signatures were updated/added to find additional vulnerabilities. Details below:
|
HTML Form Without CSRF Protection Cross-Site Request Forgery (CSRF/XSRF) is a vulnerability where an attacker tricks a victim into making a request which was not supposed to be made. So, attacker abuses the trust a web application has with a victim's browser. Mostly the HTML forms submitted have CSRF tokens embedded in them while submitting the request. If a form is without this preventive measure enabled then it's very much prone to CSRF attacks and other dependent attacks. |
Log Injection Logs are a source of information that can be used for debugging, data collection and performance optimisations. Injecting in the logs allow an attacker to insert malicious data and false entries into the logs and ultimately corrupt the file or use it for other penetration attempts. |
Web Administration Login Page Detected An application can be configured & controlled by an administrator who can access the admin panel through a login page or administration (admin) pages. A remote attacker can target such admin pages available in public to gain admin access of an application or compromise the sites via brute-force attacks, SQL Injection etc. |
VBulletin Pre-Auth RCE Vulnerability VBulletin is a software for running forums on your website. A pre-authentication remote code execution vulnerability exists in this which allows attacker to execute commands and compromise your systems. |
Apache Range Denial Of Service Apache httpd server has denial of service vulnerability in few of their versions. This exists due to the range header that expresses multiple overlapping ranges and this byte filter range allows remote attacker to cause a DOS attack resulting in memory and CPU consumption. |
Web Server Content Sniffing Enabled Content Sniffing is a technique used by the browsers to determine an asset’s correct file format. Web Servers examine the content of HTTP responses in addition to the Content-Type header field in order to determine the effective MIME (Multipurpose Internet Mail Extensions) type of the response. If any response does not contain the content type then browser will try to sniff the MIME, meaning try to determine type of content based on looking at the response body. Attackers can use this to perform Cross Site Scripting attacks by manipulating content sent to server or injecting code in the file. |
APPTRANA & TAS
On the AppTrana side, major changes continue in the direction of providing more stability and providing more enterprise friendly features to our customers.
Portal Updates
|
Rate limiting by User (Applies only for SaaS customers) One of the major changes that went live for all our SaaS customers last quarter is the implementation of Rate limiting by user for SaaS sites. By default, we provide Rate limiting by IP to all our customers, Rate limiting by user can be enabled from Apptrana portal. It has two parts i.e., Cookie based, and User API based DDOS protection. For every user, cookie will be injected, since every browser cookie is different, blocking is done at cookie level, which ensures more granular protection can be provided to customer. Customer can set Number of requests a user can make per 2 minutes (User Threshold). The user is tracked based on cookie. 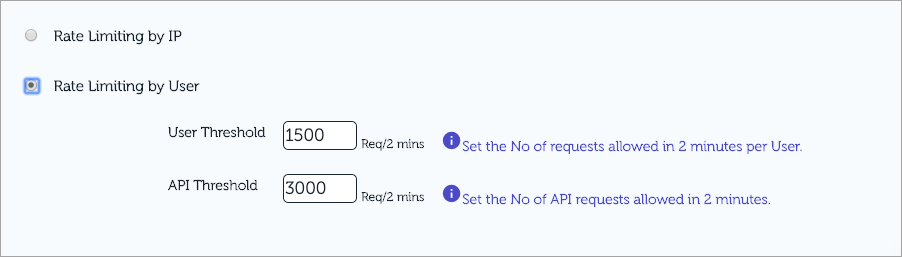
Now, API’s cannot have cookies. To support this, a separate threshold is provided for API’s. API requests will be tracked based on IP. |
Rule Updates
|
Cross-Site Scripting Rule Update (XSS) Rule ID 405: (Premium Rule) Rule will protect injection of client side scripts into web pages by an attacker. A Cross Site Scripting vulnerability can be used by attackers to bypass access controls. |
HTML5 Ping DOS Rule ID 812,814 & 816: (Advance Rule) Protect web server from DOS attack done using HTML5 attribute tag. This tag usually used by website owners to monitor/track clicks on a link, but can be used by attackers to do DDOS on the web server. |
Possible Malicious File Upload Rule ID 808: (Premium Rule) Protect malicious files from being uploaded to a web server. These files are most liked with extensions like .exe, .bin etc. |
MS15-034 IIS HTTP.sys Remote Code Execution Exploit - CVE-2014-6321 Rule ID 826: (Advance Rule) The vulnerability is due to crafted HTTP request by passing large value in Range header, IIS fails to validate the value properly leading to Denial of Service (Unresponsive or Blue Screen of Death) and possible Code Execution. |
Local Flie Injection (LFI) Rule ID 304: (Premium Rule) This rule triggers when attacker tries to access any local files to server using directory traversal. |
Apache Range Header DoS Attack Rule ID 826: (Advance Rule) A denial of service vulnerability has been found in the way the multiple overlapping ranges are handled by the Apache HTTPD server. This exploit works by making a series of HTTP requests with overlapping ranges in the "Range" or "Request-Range" request headers and results in memory and CPU exhaustion. This vulnerability concerns a 'Denial of Service' attack on a vulnerable server. This means that a remote attacker under the right circumstances is able to slow your service or server-down to a crawl or exhausting memory available to serve requests, leaving it unable to serve legitimate clients in a timely manner. |
